Hello Cyber Learners,
Welcome to my blog on preventing blind SQL injection attacks! If you're new here, I highly recommend checking out my previous posts on basic SQL injection, Practical exploitation of blind SQL injection, and Cheetshet on blind SQL injection. These posts provide a solid foundation for understanding the different types of blind SQL injection attacks and how they can be exploited.
In this post, we'll focus on practical steps you can take to prevent blind SQL injection attacks and protect your web application from this serious security threat.
- Common Blind SQL Injection Vulnerabilities
- Best Practices for Securing Web Applications
- Incident Response Best Practices on Blind SQL Injection Attacks
- Conclusion
Common Blind SQL Injection Vulnerabilities
Blind SQL injection attacks can be difficult to detect and prevent, but understanding common vulnerabilities and attack vectors can help you identify and mitigate these risks.

Input Validation
One of the most common vulnerabilities that can lead to blind SQL injection attacks is inadequate input validation. If a web application doesn't properly validate user input, an attacker can inject SQL code into the input fields and potentially execute arbitrary code on the application's database.
For example, consider a form that allows users to search for products by name:
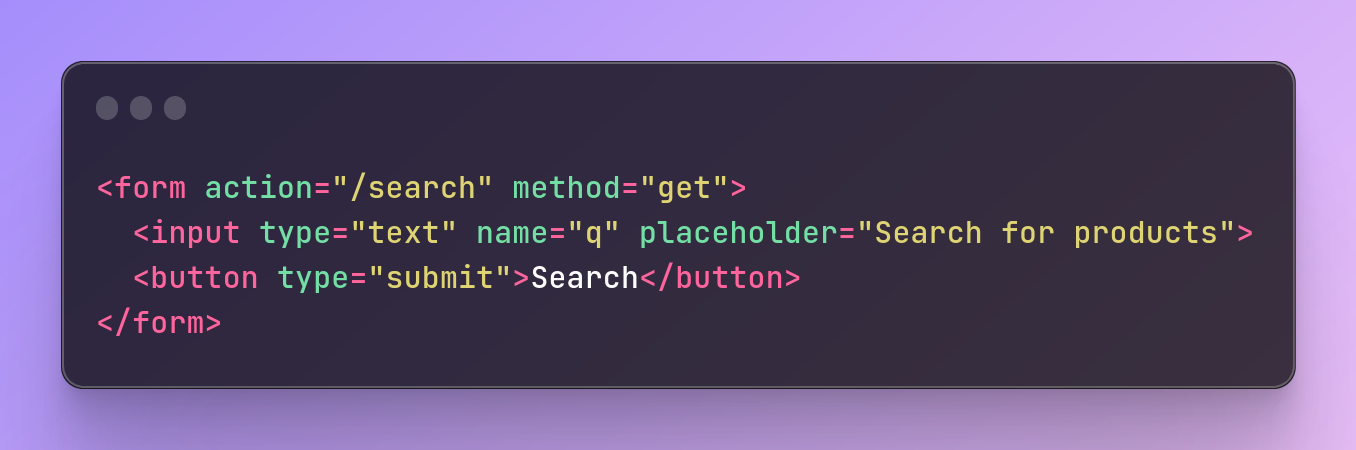
<form action="/search" method="get">
<input type="text" name="q" placeholder="Search for products">
<button type="submit">Search</button>
</form>
Without input validation, an attacker could inject malicious SQL code into the "q" parameter of the search query.
Prevention
To prevent this type of vulnerability, you should implement strict input validation and sanitize all user input before it's used in database queries. This can include checking for invalid characters or patterns in input fields, and limiting the length of user input to prevent buffer overflow attacks.
You can implement input validation like this:
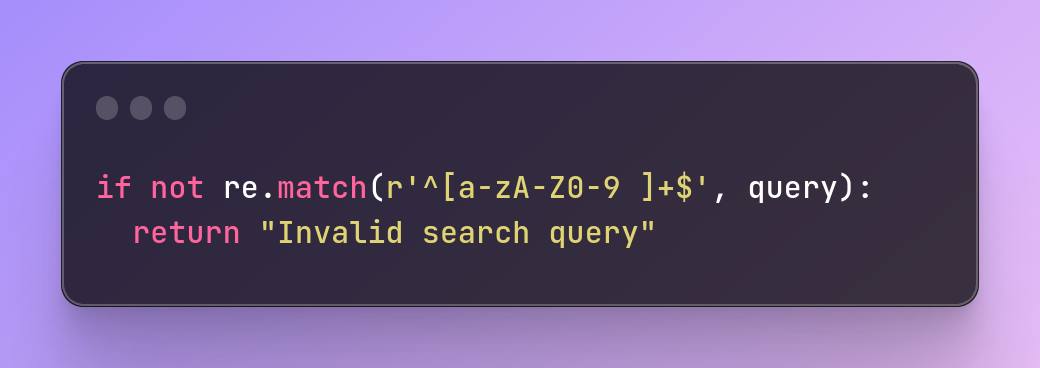
if not re.match(r'^[a-zA-Z0-9 ]+$', query):
return "Invalid search query"
This regular expression checks that the search query contains only alphanumeric characters and spaces, and rejects any input that contains special characters or SQL keywords.
To validate and sanitize user input, developers can also use functions like htmlentities() and mysqli_real_escape_string() in PHP or the Input Validation library in Java. Here's an example in PHP:
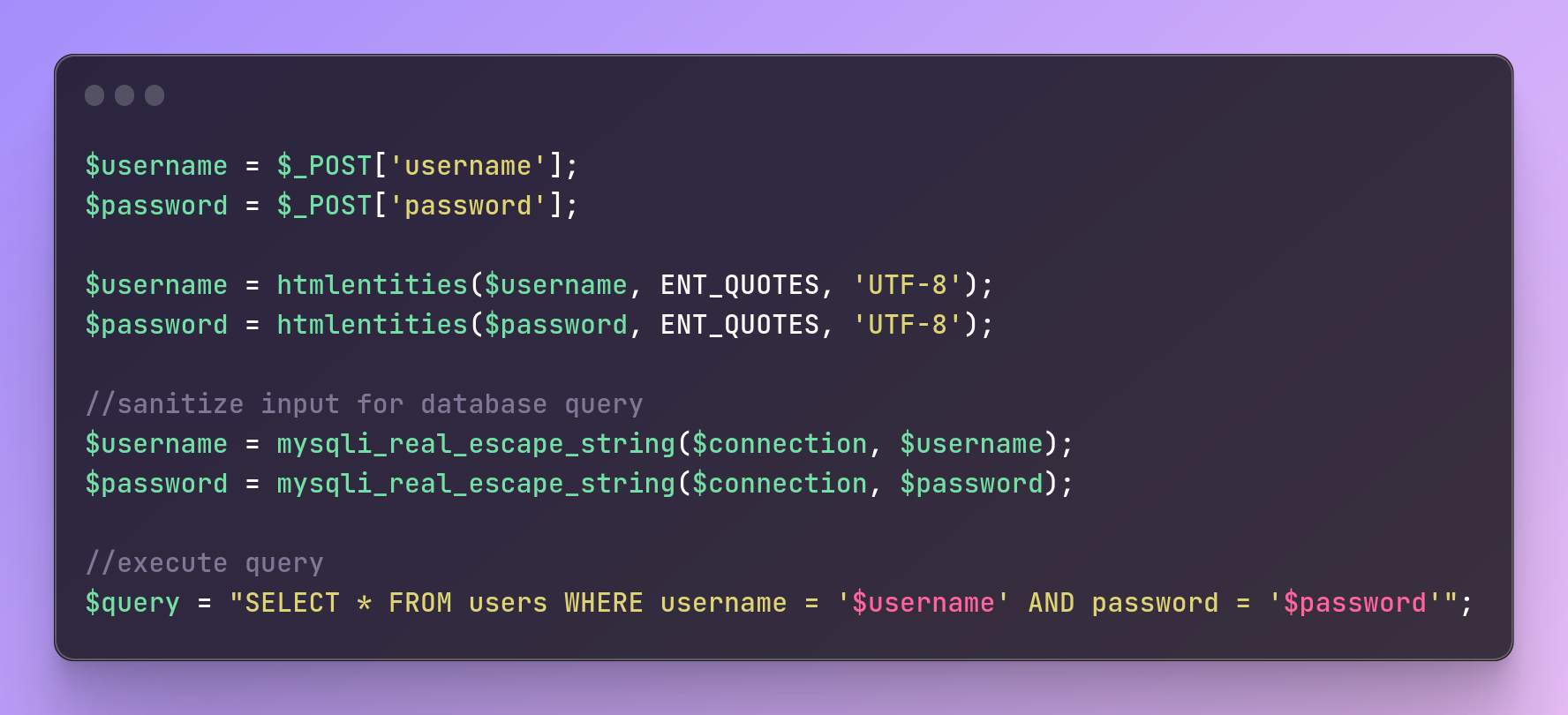
$username = $_POST['username'];
$password = $_POST['password'];
$username = htmlentities($username, ENT_QUOTES, 'UTF-8');
$password = htmlentities($password, ENT_QUOTES, 'UTF-8');
//sanitize input for database query
$username = mysqli_real_escape_string($connection, $username);
$password = mysqli_real_escape_string($connection, $password);
//execute query
$query = "SELECT * FROM users WHERE username = '$username' AND password = '$password'";
Error Messages
Another common vulnerability that can lead to blind SQL injection attacks is the way that error messages are displayed by web applications. If an application displays detailed error messages that include SQL query syntax, an attacker can use this information to craft SQL injection attacks that are more effective.
For example,
Let's say that a web application has a search functionality that takes a user's input and queries a database to find matching results. If the input is not properly sanitized, an attacker can inject SQL code into the input to manipulate the query and potentially access or modify sensitive data in the database.
Now, let's say that the web application is also set up to display error messages if the query fails for some reason. If the error message includes details about the syntax of the query, an attacker can use this information to refine their SQL injection attack and increase their chances of success.
For example, let's say that the attacker injects the following SQL code into the search input:
' OR 1=1;--
If the query fails, the web application might display an error message that includes the following details:
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '' OR 1=1;--'
Now the attacker knows that the web application is using MySQL as its database server, and they also know that the syntax for injecting SQL code is correct. They can then refine their attack by adding additional SQL code to extract or modify data from the database.
By carefully analyzing the error messages displayed by the web application, an attacker can gain valuable insights into the database structure and refine their SQL injection attack to be more effective. That's why it's important for web applications to properly sanitize user input and limit the amount of information disclosed in error messages.
Prevention
To mitigate this vulnerability, you should avoid displaying detailed error messages that include SQL query syntax. Instead, use generic error messages that don't reveal any information about the application's underlying database.
Authentication and Authorization
Authentication and authorization vulnerabilities can also lead to blind SQL injection attacks. If an application doesn't properly authenticate users or restrict their access to sensitive data, an attacker can gain access to the application's database and potentially execute arbitrary SQL code.
To implement user permissions and access controls, administrators can configure user accounts and roles in their database management system and assign appropriate permissions to each user or role.
Here's an example in PostgreSQL:
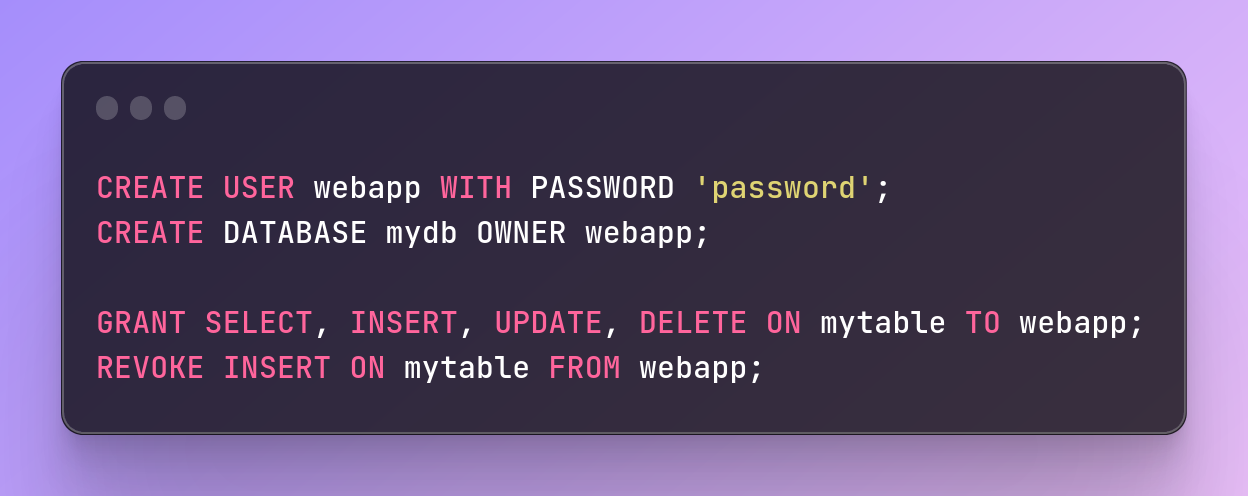
CREATE USER webapp WITH PASSWORD 'password';
CREATE DATABASE mydb OWNER webapp;
GRANT SELECT, INSERT, UPDATE, DELETE ON mytable TO webapp;
REVOKE INSERT ON mytable FROM webapp;
Prevention
To prevent this type of vulnerability, you should implement strong authentication and authorization controls, including password policies and access controls that limit user access to sensitive data.
Session Management
Session management vulnerabilities can also lead to blind SQL injection attacks. If an attacker can hijack a user's session or access sensitive session data, they can potentially execute arbitrary SQL code on the application's database.
If the session data includes sensitive information, such as database credentials or SQL query syntax, the attacker could use this information to craft a blind SQL injection attack. They could inject SQL code into the application's queries by manipulating the session data, potentially accessing or modifying sensitive data in the database.
For example, let's say that the user's session data includes a database query that looks like this:
SELECT * FROM users WHERE username='johndoe' AND password='mypass'
If the attacker can access this query by hijacking the user's session, they could modify it to look like this:
SELECT * FROM users WHERE username='johndoe' OR 1=1;--' AND password='mypass'
This modified query would return all records from the users table, effectively bypassing the authentication check and potentially exposing sensitive user data.
Prevention
To prevent blind SQL injection attacks that exploit session management vulnerabilities, web applications should implement secure session management practices, such as using strong session identifiers, enforcing session timeouts, and encrypting session data. Additionally, web developers should always sanitize user input and use parameterized queries to avoid SQL injection vulnerabilities.
Third-Party Libraries and Components
Finally, third-party libraries and components can also introduce blind SQL injection vulnerabilities into web applications. If a library or component is vulnerable to SQL injection attacks, an attacker can potentially use this vulnerability to gain access to the application's database.
For example, a web application uses a third-party library for user authentication. The library uses an SQL query to verify a user's credentials, but the query is not properly sanitized, allowing an attacker to inject SQL code.
If an attacker is able to identify this vulnerability, they can use a blind SQL injection attack to potentially access or modify sensitive data in the application's database. For example, they could try injecting a payload that bypasses the authentication check and grants them access to the application as an administrator:
' OR 1=1 AND username='admin' AND password LIKE '%';--
If the library executes this SQL code without properly sanitizing the user input, it would return all users in the users the table where the username is 'admin' and the password contains any character (due to the wildcard '%'), effectively bypassing the authentication check and granting the attacker administrative access to the application.
Prevention
To prevent blind SQL injection vulnerabilities introduced by third-party libraries and components, it is important to carefully vet and review any third-party code used in web applications. Additionally, developers should always sanitize and validate user input and use parameterized queries to avoid SQL injection vulnerabilities. Regular security audits and vulnerability scans can also help identify and remediate any vulnerabilities in third-party code.
Best Practices for Securing Web Applications
Here are some best practices for preventing Blind SQL Injection attacks:
Parameterized Queries
One of the most effective way to prevent blind SQL injection attacks is to use parameterized queries in your application code. Parameterized queries separate the SQL code from user input, which makes it much more difficult for attackers to inject malicious SQL code into your queries.
For example, consider the following SQL query that retrieves a user's account information based on their username and password:
SELECT * FROM users WHERE username = 'john' AND password = 'password123'
This query is vulnerable to SQL injection attacks, as an attacker could modify the password field to inject malicious SQL code.
To prevent this, you can use a parameterized query like this:
SELECT * FROM users WHERE username = ? AND password = ?
In this query, the "?" characters indicate placeholders for user input.
Your application code can then pass user input as parameters to the query, like this:
db.execute("SELECT * FROM users WHERE username = ? AND password = ?", [username, password])
This prevents attackers from injecting malicious SQL code into your queries, as any user input is treated as data rather than executable code.
Here's an example for Java applications:
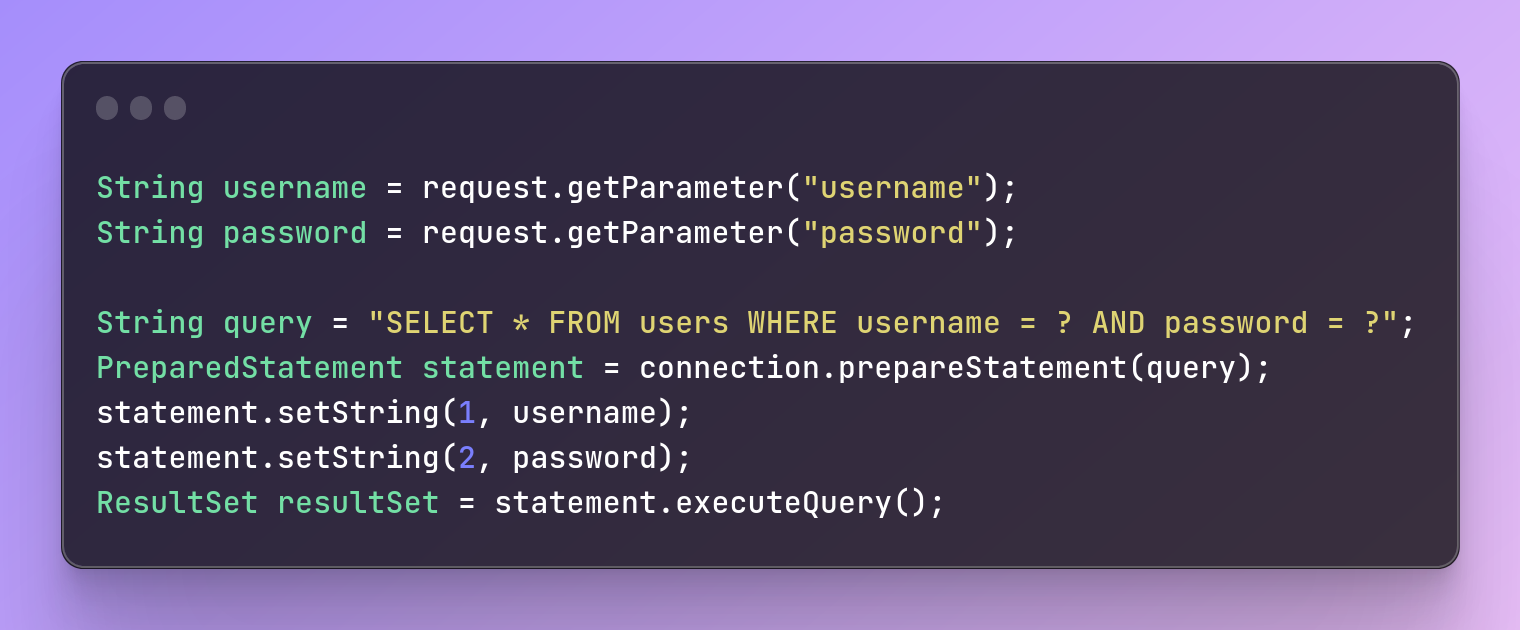
String username = request.getParameter("username");
String password = request.getParameter("password");
String query = "SELECT * FROM users WHERE username = ? AND password = ?";
PreparedStatement statement = connection.prepareStatement(query);
statement.setString(1, username);
statement.setString(2, password);
ResultSet resultSet = statement.executeQuery();
Stored Procedures
To use stored procedures, developers can define database procedures and call them from their code.
Here's an example in SQL Server:
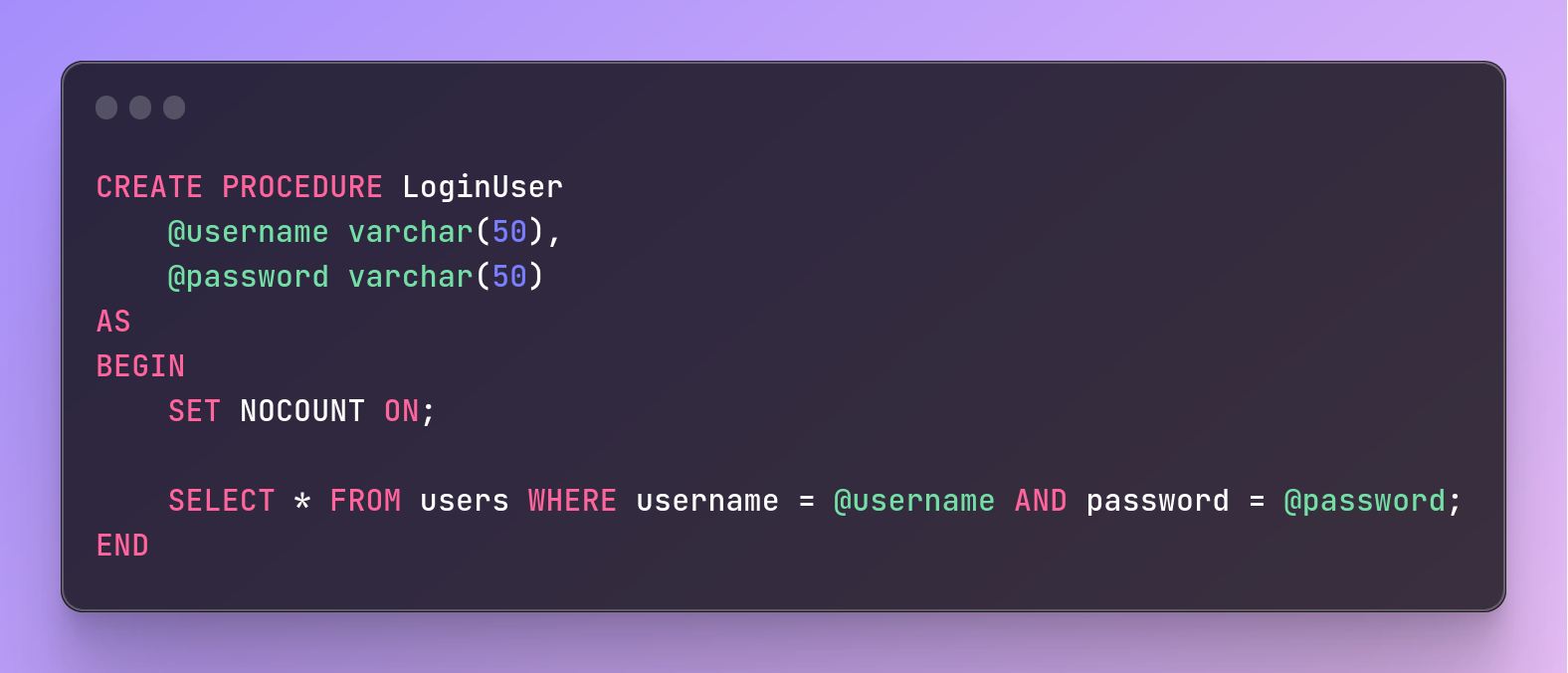
CREATE PROCEDURE LoginUser
@username varchar(50),
@password varchar(50)
AS
BEGIN
SET NOCOUNT ON;
SELECT * FROM users WHERE username = @username AND password = @password;
END
WAF (Web Application Firewall)
To use a WAF, organizations can deploy a WAF appliance or service and configure it to filter and block malicious traffic.
Here's an example of configuring ModSecurity in Apache:
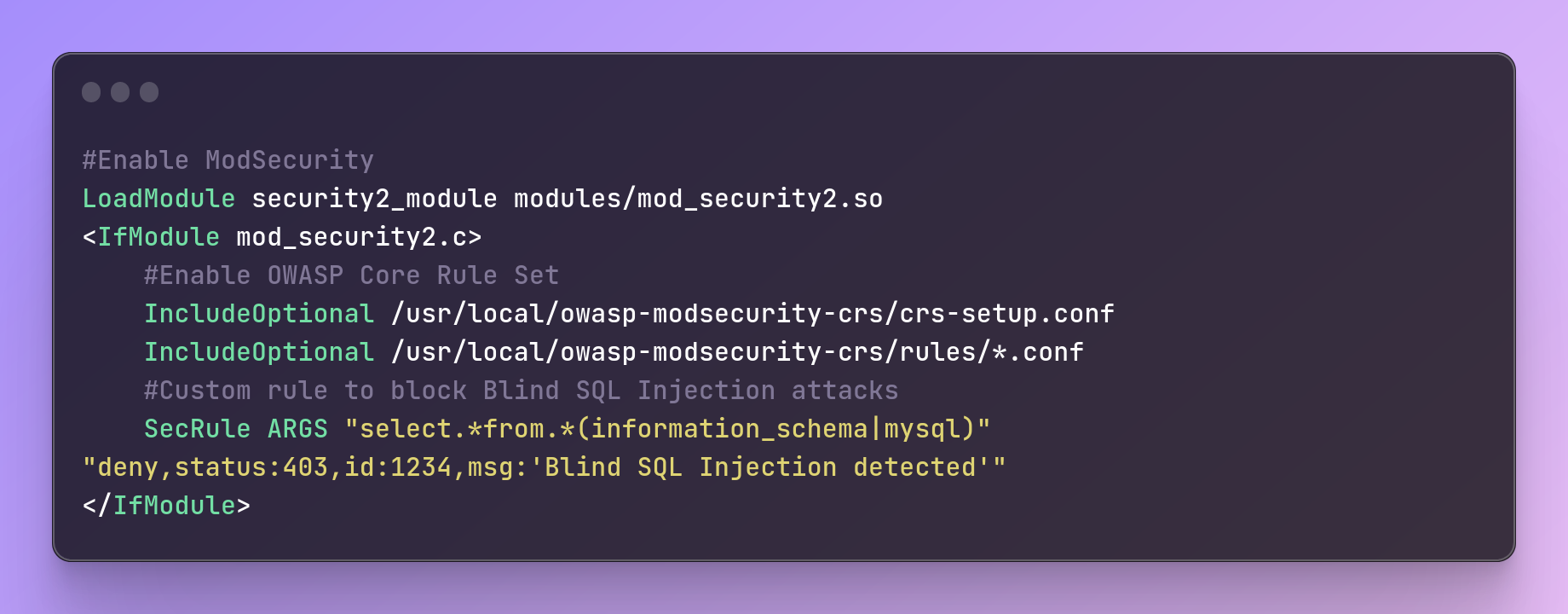
#Enable ModSecurity
LoadModule security2_module modules/mod_security2.so
<IfModule mod_security2.c>
#Enable OWASP Core Rule Set
IncludeOptional /usr/local/owasp-modsecurity-crs/crs-setup.conf
IncludeOptional /usr/local/owasp-modsecurity-crs/rules/*.conf
#Custom rule to block Blind SQL Injection attacks
SecRule ARGS "select.*from.*(information_schema|mysql)" "deny,status:403,id:1234,msg:'Blind SQL Injection detected'"
</IfModule>
Database Auditing and Logging
To enable database auditing and logging, administrators can configure database logging and monitoring tools like Audit Vault and Database Firewall or the native logging features in their database management system.
Here's an example in MySQL:
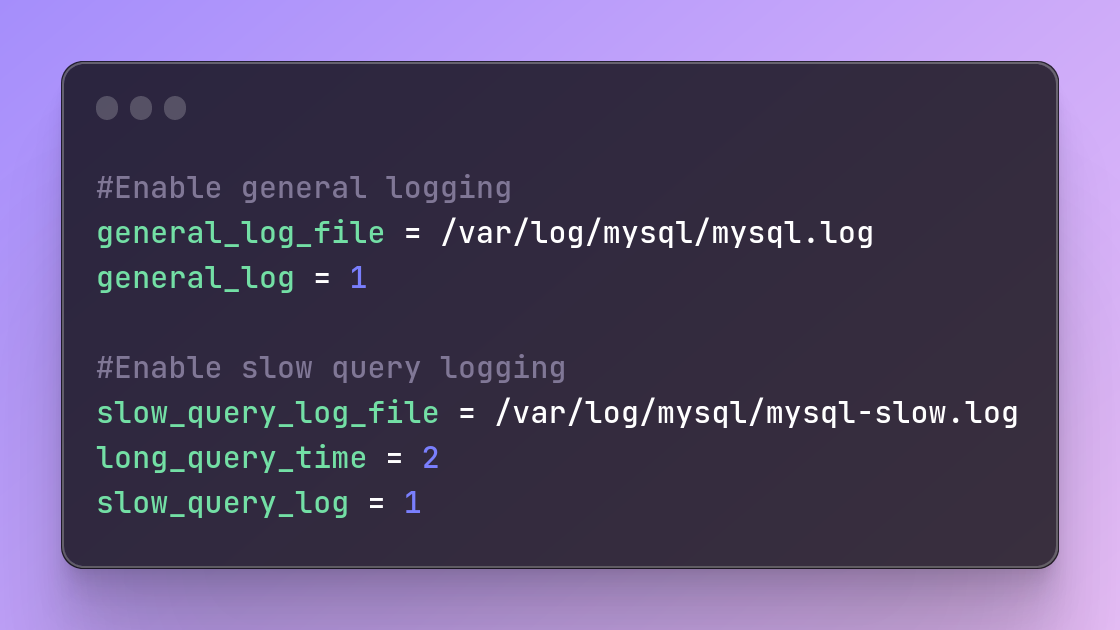
#Enable general logging
general_log_file = /var/log/mysql/mysql.log
general_log = 1
#Enable slow query logging
slow_query_log_file = /var/log/mysql/mysql-slow.log
long_query_time = 2
slow_query_log = 1
Regular Software Updates and Security Patches
Keeping software and security patches up to date is critical in mitigating Blind SQL Injection attacks. Developers should stay informed of the latest vulnerabilities and security patches and implement them as soon as possible. This helps prevent attackers from exploiting known vulnerabilities in the software. This includes not only your application code, but also any third-party libraries or dependencies that your application relies on.
For example, if your application uses a popular web framework such as Django or Flask, you should regularly check for updates and apply any security patches as soon as possible.
Incident Response Best Practices on Blind SQL Injection Attacks
Blind SQL injection attacks can be difficult to detect and respond to, as they often involve attackers exploiting vulnerabilities in your application without leaving any visible traces. However, it's important to have an incident response plan in place in case of such an attack, as a quick and effective response can minimize the damage and prevent further exploitation.

Identify the Attack
The first step in responding to a blind SQL injection attack is to identify that an attack is occurring. This can be challenging, as the attack may not leave any visible signs and may not generate any unusual activity in your logs.
One way to identify a blind SQL injection attack is to monitor your application's behavior and look for any anomalies. For example, if you notice a sudden spike in database queries, or if queries are taking longer than usual to execute, this may be a sign of an attack.
Another way to identify an attack is to use specialized tools such as SQLmap, which can automate the process of identifying and exploiting SQL injection vulnerabilities in your application.
Contain the Attack
Once you've identified that an attack is occurring, your next step should be to contain the attack to prevent further damage. This may involve shutting down certain parts of your application, blocking incoming traffic from certain IP addresses, or even taking your application offline entirely.
For example, if you suspect that the attacker is exploiting a vulnerability in a specific page of your application, you may choose to take that page offline while you investigate the issue.
Investigate the Attack
After you've contained the attack, you should begin investigating the attack to determine its scope and severity. This may involve reviewing your application logs, examining your database to see if any data has been stolen or modified, and analyzing any code or server configurations that may have contributed to the vulnerability.
It's important to document your investigation thoroughly, as this will help you identify any vulnerabilities in your application and prevent similar attacks from occurring in the future.
Remediate the Vulnerability
Once you've identified the vulnerability that allowed the attack to occur, your next step should be to remediate the vulnerability to prevent future attacks. This may involve patching your application, modifying your code, or changing your server configurations.
For example, if the attack was caused by a SQL injection vulnerability in your application code, you may need to modify your code to use parameterized queries and input validation, as we discussed in a previous post.
Notify Affected Parties
If the attack resulted in the theft or modification of sensitive data, you may need to notify affected parties such as customers or regulatory agencies. It's important to be transparent and forthcoming about any data breaches or security incidents, as this will help build trust with your customers and demonstrate your commitment to security.
Conclusion
Blind SQL injection attacks can be difficult to detect and prevent, but understanding common vulnerabilities and attack vectors can help you identify and mitigate these risks. By implementing strict input validation, avoiding detailed error messages, implementing strong authentication and authorization controls, implementing strong session management controls, and vetting third-party libraries and components, you can reduce the risk of blind SQL injection attacks in your web application.
Commonly Asked Questions
Q1. I have found Blind SQL Injection Vulnerability in an application, how can I ask the authorities to reward me with a bug bounty?
Ans. To claim a bug bounty for finding a Blind SQL Injection Vulnerability in an application, follow these steps:
- Check if the application has a bug bounty program.
- Document the vulnerability with supporting evidence.
- Contact the authorities responsible for the application's security.
- Wait for a response from the authorities.
- If the vulnerability is confirmed, follow instructions for claiming the bug bounty.
It's important to act responsibly and ethically when reporting vulnerabilities and respect the privacy and security of the application and its users.
Q2. How does one find the database of Website with an SQL injection Automated Tools?
Ans.To find the database of an Web Application, you need to identify the vulnerable parameter using a tool like SQLmap. Once you have identified the database, you can use SQLmap to enumerate it, extract data from it, and analyze the data to determine its significance and impact. However, it is important to obtain proper authorization and follow ethical guidelines when performing security testing or conducting vulnerability assessments.
Related Blogs
- SQL Injection Attack (SQLi) | SQL Injection Prevention | SQL Injection Cheat Sheet [Practical Demo]
- Advanced SQL Injection Attack (SQLi) | Blind SQL Injection And Prevention
- Advanced SQL Injection Attack (SQLi) | Blind SQL Injection And Prevention [Practical Demo] part 2
- What is Website Hacking | Web Application Penetration Testing | Lab Setup
- What is OSINT? | OSINT Framework | Tools for OSINT | Best OSINT Techniques
- OSINT Framework | OSINT for Bug Hunters [Practical Demo] Part 1
- OSINT Framework | OSINT for Bug Hunters [Practical Demo] Part 2
- What is Smurf Attack? | What is the Denial of Service Attack? | Practical DDoS Attack Step-By-Step Guide
- What is DoS Attack | How to do Denial of Service Attack [Practical Demo]
- What is Packet Sniffing? | How to Perform Packet Sniffing | Practical Demo on Wireshark
- What is Metasploit Framework | What is Penetration Testing | How to use Metasploit
- How to Install Metasploit on Windows and Linux | [Step by Step Guide]
- How to Use Metasploit | Metasploit Commands | Metasploit Tutorial