Hello Cyber Learners,
Digital devices and online communication have become an integral part of our daily lives, enabling us to connect with others and access information from anywhere in the world. However, this digital landscape also presents new challenges and risks, particularly in the area of cybercrime. As more and more criminal activities are conducted online, the need for effective digital forensics has never been greater. In this blog, we will explore the latest trends and techniques in digital forensics, offering insights and guidance to help investigators and analysts stay ahead of the curve.
Also, I will show you a step-by-step guide with a video on a forensics tool.
- What Is Digital Forensics?
- Types of Digital Forensics
- Practical Demo on Volatility
- Practical Video on Digital Forensics
- Conclusion
What is Digital Forensics?
Digital forensics refers to the scientific process of identifying, preserving, collecting, analyzing, and presenting electronic evidence in a manner that is admissible in a court of law. It involves the use of specialized tools and techniques to investigate various types of digital media, such as computers, smartphones and storage devices to uncover evidence of cybercrime, data breaches, or other forms of malicious activity.
If you want to know digital forensics from basics like the job opportunities, tools, advantages and disadvantages of digital forensics then you can check out my previous blog Digital Forensics. where I have explained everything about digital forensics in detail.
Types Of Digital Forensics
There are several types of digital forensics, each with its own focus and scope. Some of the most common types include:
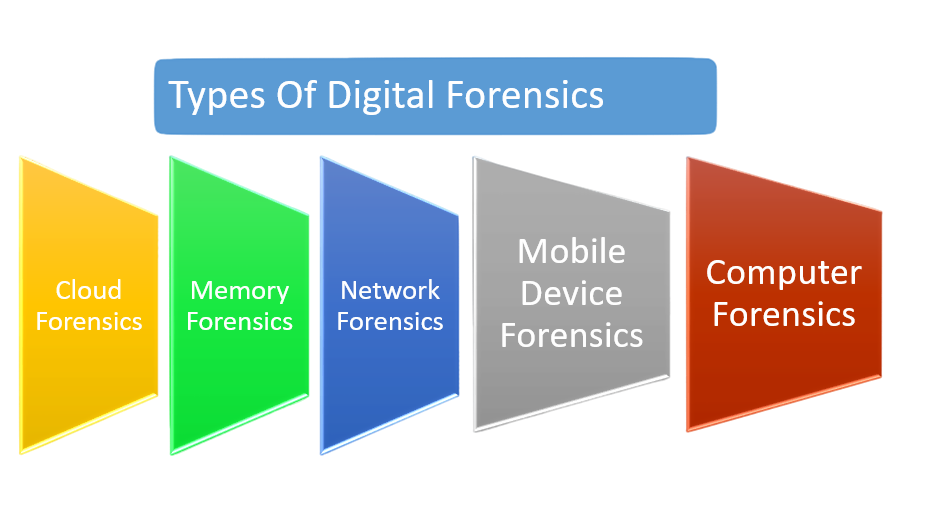
Computer forensics: This involves the investigation and analysis of computer systems, such as desktops, laptops, servers, and storage devices to uncover evidence of cybercrime, data theft, or other malicious activity.
Mobile device forensics: This focuses on the investigation and analysis of mobile devices, such as smartphones and tablets, to identify evidence of cybercrime, data breaches, or other forms of malicious activity.
Network forensics: This involves the investigation and analysis of network traffic, such as logs, packets, and protocols, to identify evidence of cyber-attacks, data breaches, or other forms of malicious activity.
Memory forensics: This focuses on the analysis of volatile memory, such as RAM, to uncover evidence of malware, hacking, or other malicious activity that may not be visible on the disk.
Cloud forensics: This involves the investigation and analysis of data stored on cloud-based platforms, such as Google Drive or Dropbox, to identify evidence of cybercrime, data breaches, or other forms of malicious activity.
These are just a few examples of the many types of digital forensics that exist. Each type requires specialized tools and techniques, as well as a deep understanding of the underlying technology and potential risks involved.
Practical Demo On Volatility
After learning about What is Digital Forensics and Types Of Digital Forensics, we will see the Practical Demo On Volatility. In this Demo, we will see practical on memory forensics.
Note: I am considering you already have installed the Volatility tool on your machine. If you are new and don't know how to install and set up the Volatility tool in Kali Linux you can check my video at the end of this blog.
For this demonstration, we need a memory dump file and I have downloaded a dummy file from the internet. If you also want to use the same file then you can download the memory dump file by clicking on the memory-dump.
Step 1: Before using any tool it is good practice to first see the help section of the tool. You can type the following command to open the help section of the tool.
volatility --help
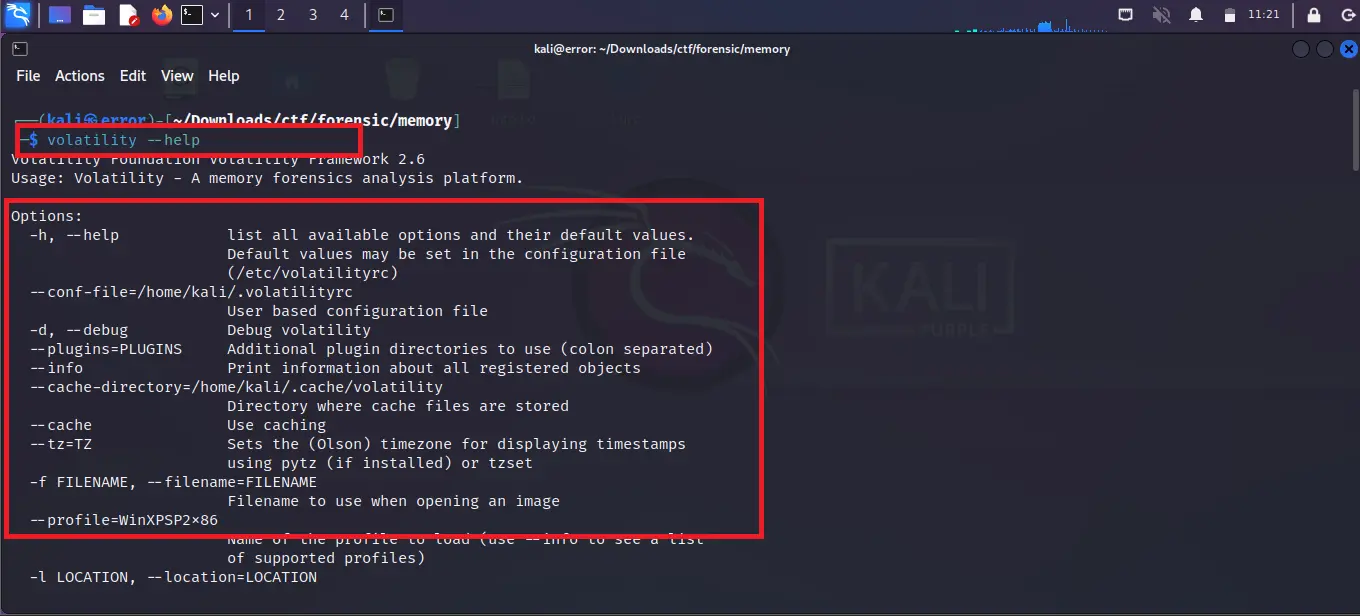
Step 2: After opening the help section you can use the volatility tool. You can run the tool by typing the below command.
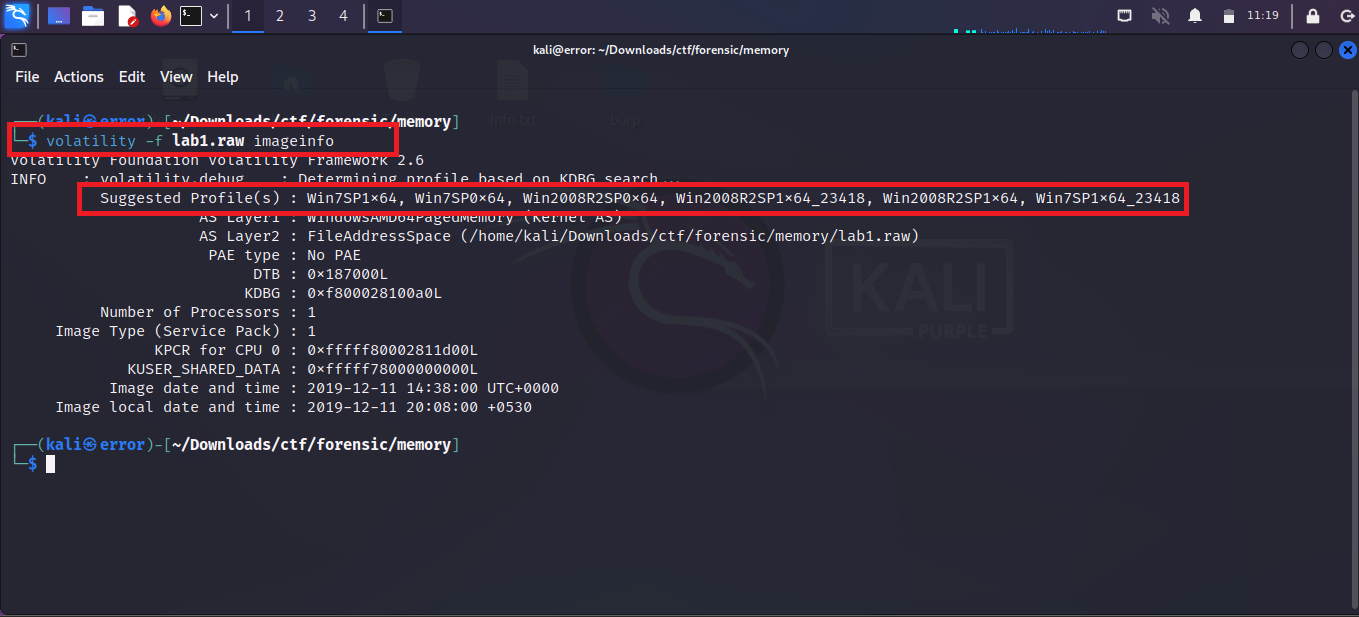
volatility -f [ file name ] imageinfo
-f: -f flag is used to specify the filename. In our case, the file name is lab1.raw which is the same file that we have downloaded from the internet.
imageinfo: As it names it will show the information about the memory dump file. While you are starting digital forensics you must have to identify which memory dump file belongs to which OS system and what is version of the OS. for example Windows 10 has various varieties like windows 10 pro, windows 10 enterprise, and windows 10 entertainment.
You can see the below image where I run the above command and it shows me the details of the memory dump file where the suggested profile shows the OS version from where the memory dump belongs.
Step 3: After identifying the profile you can start by applying from the first profile, As we see it shows multiple profiles in the previous step so, if the first profile is wrong you can choose another profile from the dump file. After finding the profile of the dump file you can run the following command
volatility -f [filename] --profile=[ specify the profile ] pslist
-f: -f flag is used for the file name.
--profile: You can specify the profile name so that tool can give you the exact details It is important to choose the right profile.
pslist: This flag is used to check the list of running processes so if you have to check which processes are running at that time when memory is dumped then pslist will be helpful.
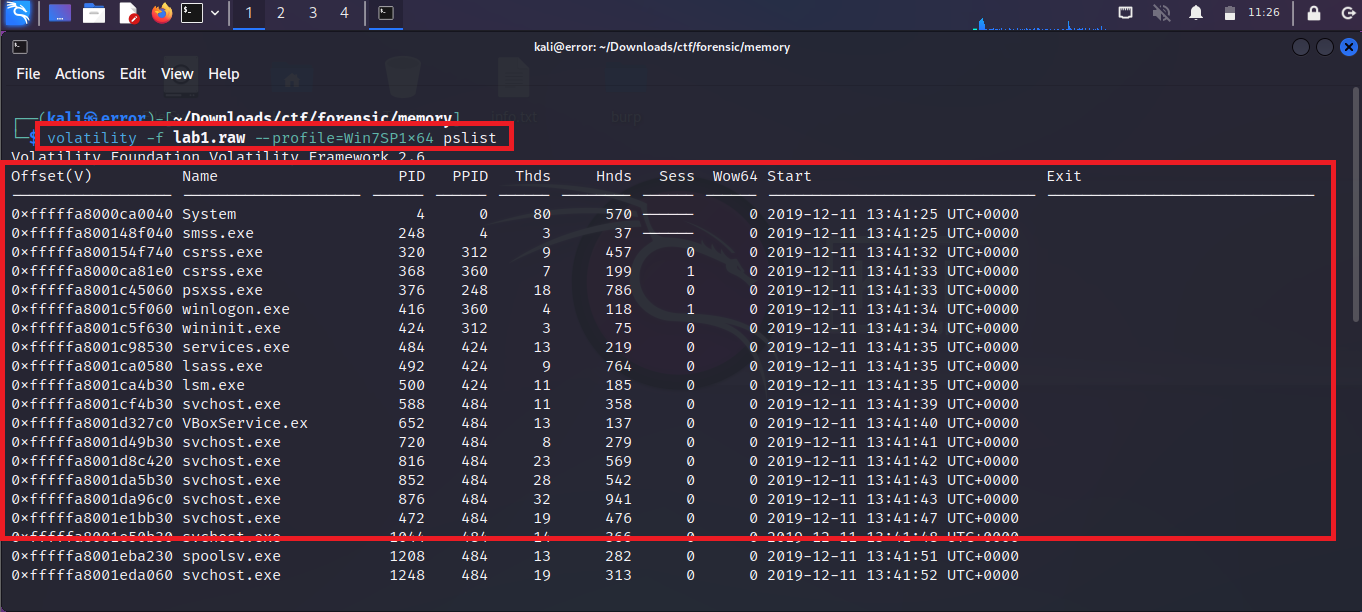
You can see the above image where a list of processes with their names is showing when the memory dump is running.
Normally a forensics investigator monitors the processes and analyzes the process that looks unwanted. In the process list, there are lots of windows default processes which run automatically.
Step 4: After finding the weird or different process a forensics investigator often uses the following command that helps to find out what commands the system user runs at that time. This command helps you to find out what commands system user run at that time.
volatility -f [ file name ] --profile=[ profile name ] cmdscan
-f: -f flag is used to specify the file name.
--profile: You can specify the profile name so that tool can give you the exact details.
cmdscan: This flag is used for finding what custom command is running.
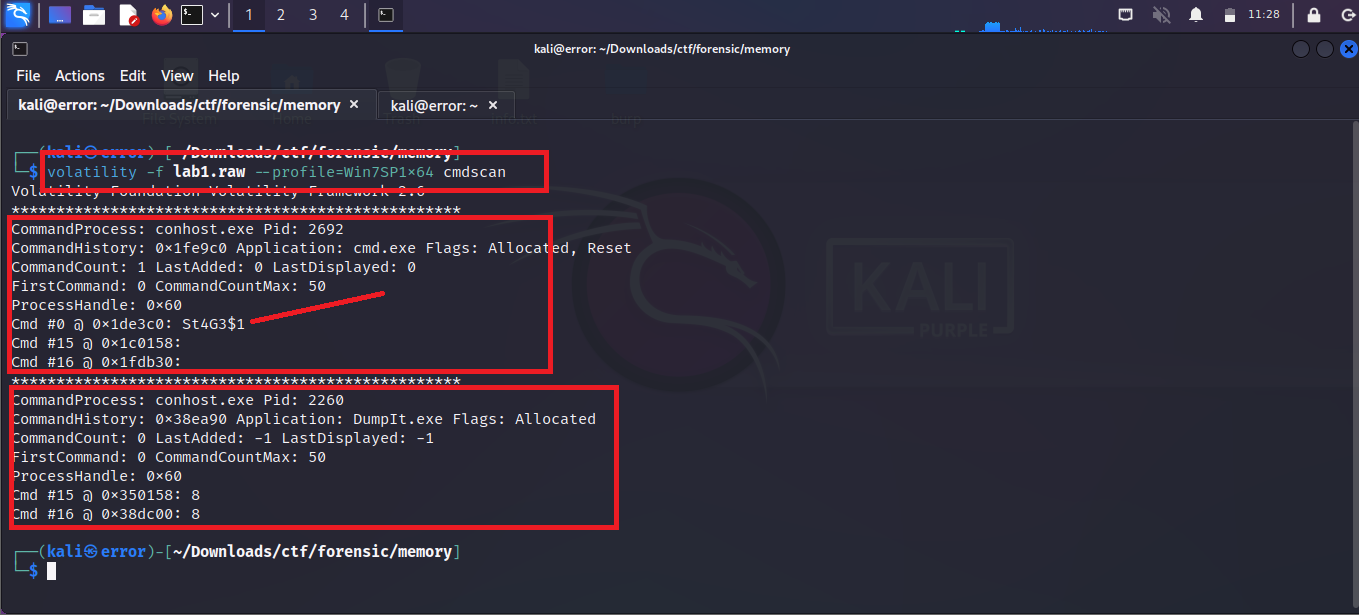
You can see in the above image St4G3$1 is a custom command which is run by the user or system user. also, you can see DumpIT.exe which is a tool used to dump the memory
It means in our memory dump file a user has added a tool DumpIT.exe and an St4G3$1 custom command. Adding such thing can be harmful for your system and we know what are the intentions of hackers to add such stuff.
Step 5: We can also check what type of input is given by the user at that time. You can run the following command to find the inputs.
volatility -f [ file name ] --profile= [ profile name ] consoles
-f: -f flag is used for the file name.
--profile: You can specify the profile name so that tool can give you the exact details.
consoles: consoles flag is used for finding the input given by the users.
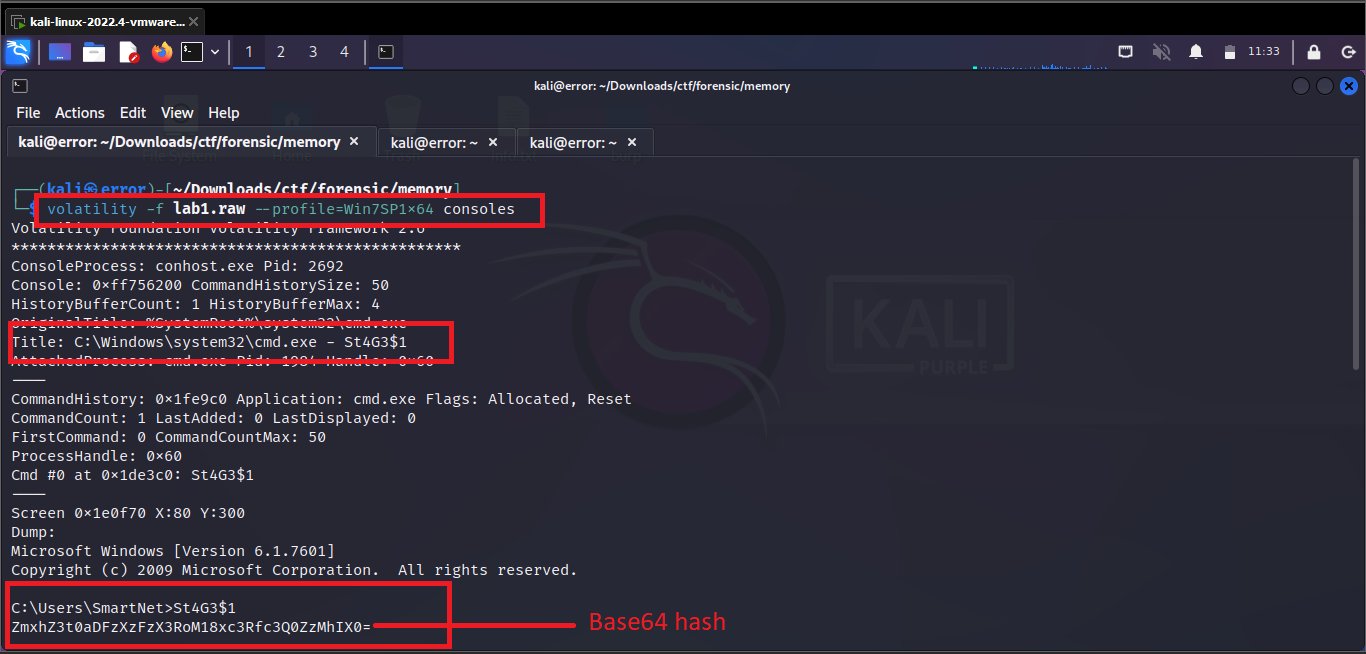
You can see that the user enters the two inputs first is St4G3$1 and the second one is a long string which is encoded into base64 which means the user is trying to hide something. Let's decode the hash.
Que 1: What is Encoding?
Ans: Encoding is the process of converting information from one format to another to make it more secure. It involves different encoding techniques such as base64, Hex, URL encoding etc.
Note: If youwant to know more about encoding and it's types then you can check it by clicking on Encoding
Step 6: We find the hash in step 5 so let's crack the hash and for that, you can run the following command.
echo [ base64hash ] | base64 -d
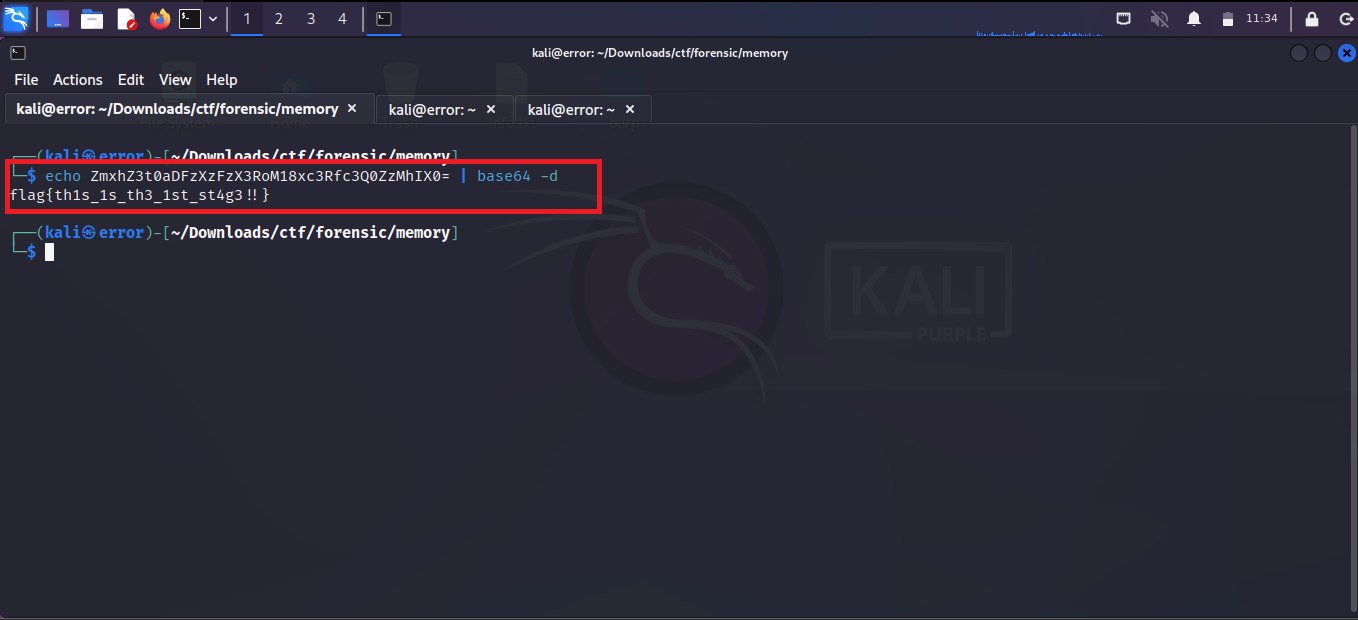
As you can see in the above image we got a string after decoding.
This is just a small demo with some basic commands that shows how you can use the Volatility tool. There lot of other things that this tool can do.
I suggest you learn this tool with the above steps and also explore by yourself with its help section.
Practical Video on Digital Forensics
In this video, you will see how to use the digital forensics tool Volatility with a practical example. We will also see encoding base64 and how to decode it with a single command. If you are new to digital forensics and are first time going to use Volatility then don't worry this video also covers first how to download and install the Volatility tool.
Conclusion
This blog has provided an overview of digital forensics and its importance in investigating cybercrime. We discussed the various types of digital forensics, including computer forensics, network forensics, mobile device forensics, and memory forensics. Furthermore, we conducted a practical demo on Volatility, which is a popular memory forensics tool used by digital forensic investigators to analyze volatile memory. We explored the features of Volatility and demonstrated how it can be used to identify hidden processes, detect rootkits, and analyze network connections.
Overall, digital forensics plays a critical role in modern-day crime investigations, and it is essential for organizations to have trained professionals and effective tools to handle cyber incidents. By leveraging tools like Volatility, digital forensic investigators can gather crucial evidence that can be used to identify perpetrators, establish timelines of events, and support legal proceedings.
Related Blogs
- What is Digital Forensics | How to Use Digital Forensics Tools
- What is Packet Sniffing | How to perform Packet Sniffing | Praactical Demo On Wireshark
- SQL Injection Attack (SQLi) | SQL Injection Prevention | SQL Injection Cheat Sheet [Practical Demo]
- What is DoS Attack | How to do Denial of Service Attack [Practical Demo]
- Nmap Commands | How to Use Nmap Tool
- What is Metasploit Framework | What is Penetration Testing | How to use Metasploit