Hello cyber learners,
Welcome to our exploration of the Tor browser! It's like a secret passage on the internet, helping you stay hidden from snoopy eyes. But just like any adventure, there are twists and turns along the way. We're here to guide you through the maze of Tor vulnerabilities, showing you how they can affect your online safety and what the smart folks at the Tor Project are doing to keep you protected.
- Traffic Analysis Attacks
- Exit Node Vulnerability
- Tor Browser Bundle Vulnerabilities
- Relay Early Traffic Confirmation Attack
- Cross-Site Scripting (XSS) and Fingerprinting
- The Future of Tor
- Challenges Facing the Tor Project
- Conclusion
- Commonly Asked Questions
The Tor browser, designed to protect user's anonymity and privacy online, has faced several vulnerabilities over the years. These vulnerabilities range from minor bugs to significant security loopholes that could potentially compromise user anonymity.
Traffic Analysis Attacks
One of the most significant vulnerabilities comes from traffic analysis attacks, such as end-to-end timing attacks, where an attacker tries to analyze traffic patterns entering and exiting the Tor network to de-anonymize users.
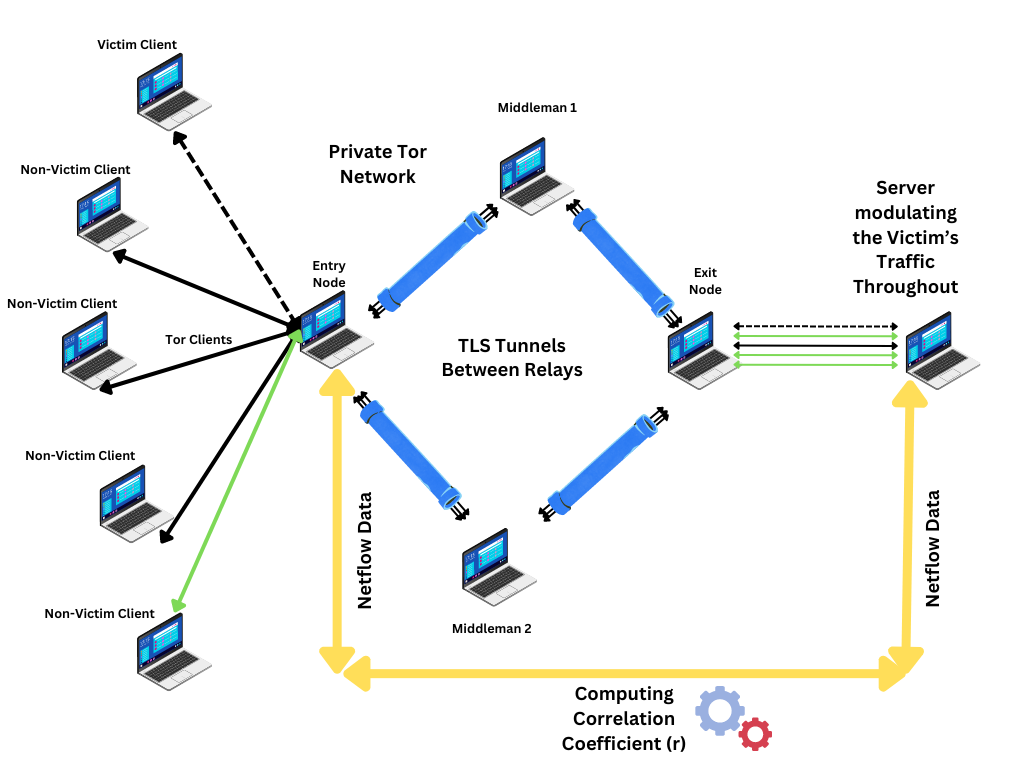
Solution: To combat traffic analysis attacks, the Tor network employs a variety of strategies. One key approach is the use of padding strategies to introduce dummy traffic, making real user traffic less distinguishable from noise. This helps obscure patterns that could be used in timing attacks. Additionally, Tor uses layered encryption and routes traffic through multiple relays, making it significantly harder for attackers to analyze traffic patterns accurately. Learn more about Traffic analysis attacks.
Exit Node Vulnerability
Since Tor traffic exits through an exit node before reaching its final destination, any data not encrypted can be read or modified by the operator of the exit node. Malicious exit nodes can potentially capture unencrypted traffic, leading to privacy breaches. Check our article to learn more about how these nodes work, and everything about the Tor network What is Tor? | How Does it Work? | Everything About Tor Network
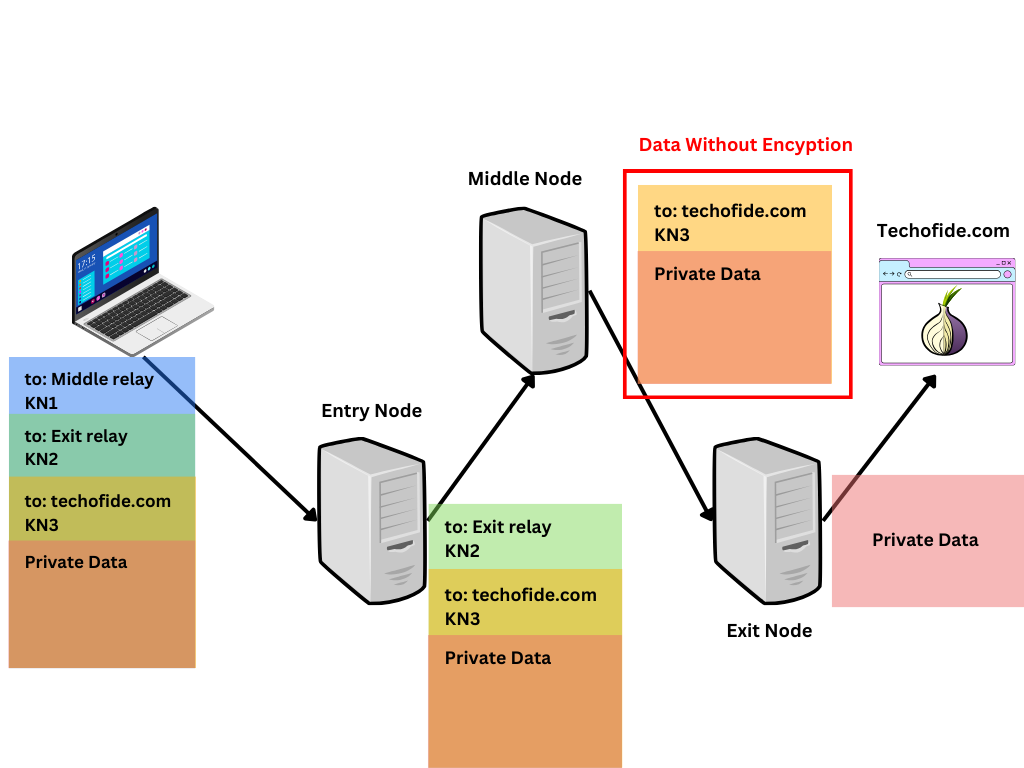
Solution: While the nature of the Tor network means that exit node vulnerability cannot be eliminated, users are encouraged to use end-to-end encryption (such as HTTPS) to protect their data from being read or modified by exit nodes. The Tor Project also actively monitors the network for malicious exit nodes and removes them when discovered. Furthermore, the use of .onion services, which keep traffic within the Tor network, can mitigate this risk as the traffic does not exit through an exit node to the open internet. Learn more about Exit node vulnerability.
Tor Browser Bundle Vulnerabilities
The Tor Browser itself, based on Firefox, has inherited vulnerabilities from the underlying browser. These have included issues like JavaScript exploits, which could potentially de-anonymize users if they had JavaScript enabled on non-HTTPS sites.

Solution: The Tor Browser is regularly updated to fix inherited vulnerabilities from Firefox. The Tor Project also disables or modifies certain features of Firefox that could compromise privacy and security, such as disabling JavaScript on non-HTTPS sites by default in the highest security settings. Regular security updates and patches are released to address new vulnerabilities as they are discovered. You can also use no script suite extension to block JavaScript in the Tor browser. Learn more to know about no script suite extension.
Relay Early Traffic Confirmation Attack
In 2014, researchers discovered a vulnerability where attackers could potentially confirm or deny if a given user was accessing a particular website. This was done by modifying the traffic flowing through compromised relays in the Tor network.
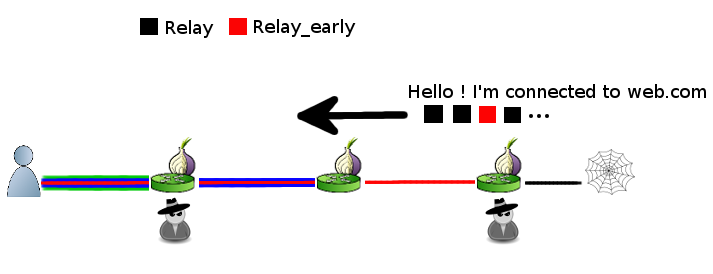
Solution: In response to the relay early traffic confirmation attack, the Tor Project implemented changes in the way relays handle traffic, including updates to the protocol to prevent the specific pattern of traffic that was indicative of the attack. This included both short-term fixes to immediately mitigate the risk and longer-term protocol improvements to prevent similar vulnerabilities. Read more about the Relay early traffic confirmation attack.
Cross-site Scripting (XSS) and Fingerprinting
Vulnerabilities in websites accessed through Tor, such as XSS attacks, can be used to inject malicious scripts and track users across sessions. Similarly, browser fingerprinting techniques can potentially identify users based on their browser and device characteristics, even when using Tor.
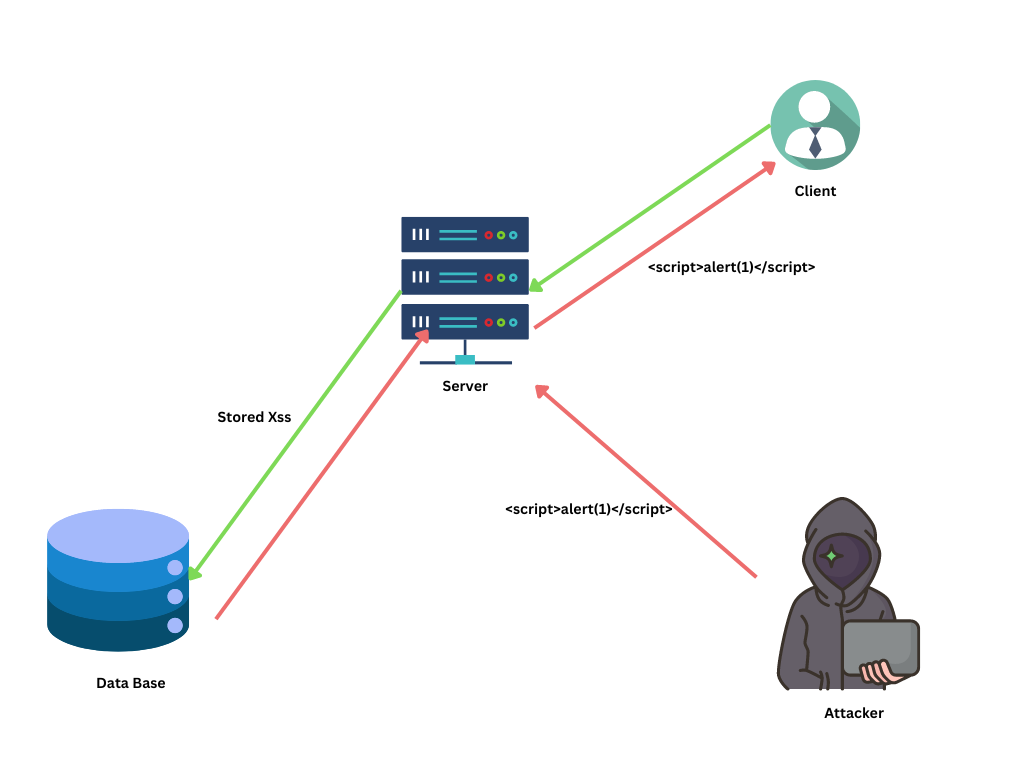
Solution: To mitigate XSS attacks, the Tor Browser includes strong content security policies that restrict the execution of potentially malicious scripts. For fingerprinting, the Tor Browser aims to make all users appear as similar as possible, reducing the amount of unique information that websites can collect about a browser. This includes uniformity in the user agent string, screen size, fonts, and more. For your security, you can use u-block origin-type extensions to block all trackers and malicious scripts. read more to know more.
It's important to note that the battle against vulnerabilities and attacks in systems like Tor is ongoing. The Tor Project continuously works to identify, understand, and mitigate new and existing threats to user privacy and security.
The Future of Tor
Now that we've explored the past vulnerabilities that have challenged Tor, let's peer into the future and see what exciting developments are coming ahead.
The Tor project is continuously evolving, with the team working tirelessly to enhance its functionality and user experience. One of the key focus areas is improving speed and reliability. Users can look forward to faster connection times and more stable browsing sessions, making the use of Tor smoother than ever before.
Another significant area of development is mobile integration. With the increasing use of smartphones for internet access, the Tor team is dedicated to optimizing Tor for mobile platforms.

Despite the exciting developments, the road ahead is not without its hurdles. One of the biggest challenges is combating censorship and blocking efforts by governments and organizations. As some entities strive to restrict access to Tor, the project must innovate ways to circumvent these barriers, ensuring users can connect freely and anonymously. Funding is another critical challenge. Being a free and open-source project, Tor relies heavily on donations and grants. Securing sufficient resources is essential for research, development, and maintaining the infrastructure needed to keep Tor running smoothly.
Conclusion
In wrapping up, we've seen how Tor faces challenges but keeps getting stronger. As it aims for faster, better browsing and fights against censorship and cyber threats, it needs support to keep going. With the help of its community, Tor is heading towards a future where everyone can browse the internet safely and privately. So let's keep moving forward together, making sure online privacy stays within everyone's reach.
Commonly Asked Questions
Q1. Is Tor completely anonymous and secure?
Ans. While Tor provides a high level of anonymity and security, it's not foolproof. Users should be aware of potential vulnerabilities and take additional measures like using end-to-end encryption and keeping software up to date.
Q2. How can I contribute to the Tor project?
Ans. There are several ways to contribute to the Tor project, including donating funds, volunteering as a relay operator, contributing code, or simply spreading awareness about online privacy and security.
Also you can buy some stickers or t-shirts from tor's store https://donate.torproject.org/
Q3. Can I use Tor on my mobile device?
Ans. Yes, there are Tor browser versions available for mobile devices, allowing you to browse the internet securely and privately on your smartphone or tablet.
You can download from here: https://www.torproject.org/download/#android
Related Blogs
- What is the Dark Web | Is Dark Web Illegal? - An Introduction
- What is Tor | How to Use Tor Browser?
- How to Access Dark Web | Use Dark Web Links Safely
- What is Tor? | How Does it Work? | Everything About Tor Network
- How are TOR Onion Hidden Addresses Created | How Does it Work?
- OWASP ZAP | A Powerful Web Application Security Testing Tool
- What is Wireshark | How to Use Wireshark [Practical Demo]
- How to Install Kali Linux Step By Step Guide