Hello Cyber Learners,
In today's digital age, where every click, search, and interaction online can be tracked, the quest for privacy has led many to explore Tor. But what exactly is Tor? Let's dive deep into its world, understanding its purpose, history, how it works and the fundamental concept of online anonymity all explained in simple terms.
- What is Tor?
- The History of Tor
- What is Onion Routing?
- How a Request Travels Through The Tor Network
- Why are .onion Websites Hard to Trace?
- Conclusion
- Commonly Asked Questions
What is Tor?
Tor, short for The Onion Router, is a free software that enables anonymous communication on the internet. Imagine it as a special browser, much like Google Chrome or Firefox, but with a twist. When you use Tor, your internet activity is wrapped in layers of encryption, similar to the layers of an onion, and sent through a global network of servers. This process makes it extremely difficult for anyone to trace your online actions back to you, offering a high level of privacy and security.
Interested in downloading and installing the Tor browser in your system? Don't worry we got you covered. Check our step-by-step guide on What is Tor | How to Use Tor Browser?
The History of Tor
The story of Tor begins in the mid-1990s, developed initially by the United States Naval Research Laboratory. The primary goal was to protect the online communications of intelligence agencies. However, recognizing its broader potential, it was later released as an open-source project for public use. Today, Tor serves a diverse user base, from journalists and activists seeking to bypass censorship, to regular individuals who simply want more privacy online.

Tor's purpose extends beyond just hiding browsing activity. It's a vital tool for those living under oppressive regimes, providing a lifeline to access unbiased information, connect with the outside world, and exercise their freedom of speech without fear of retribution.
What is Onion Routing?
Anonymity means that your identity, location, and what you do on the internet are hidden from others. In the context of Tor, this is achieved through a unique method called onion routing.

Onion routing is a technique that ensures online communication remains anonymous and secure. It uses multiple layers of encryption, much like the layers of an onion. Each layer encrypts the information about the next destination, ensuring that no single point in the journey knows both where the data came from and where it's going.

Imagine sending a letter with multiple envelopes, each addressed to a friend who only knows the next friend in the sequence. Each friend opens one envelope and forwards it to the next, ensuring that no single person knows both the sender and the final recipient. Similarly, Tor encrypts your data multiple times and routes it through several relays in its network, peeling away one layer of encryption at each step. By the time your data reaches its destination, its origins are obscured, protecting your identity and activities from prying eyes.
How a Request Travels Through the Tor Network
When you use Tor to visit a website, your request doesn't go straight to its destination. Instead, it embarks on a remarkable journey through the Tor network, which is made up of thousands of volunteer-run servers known as nodes. We can divide them in main 3 Nodes for better understanding.
Node: Node is a computer that helps in passing encrypted data between users. It forwards data packets through the network while keeping the information secure and anonymous.
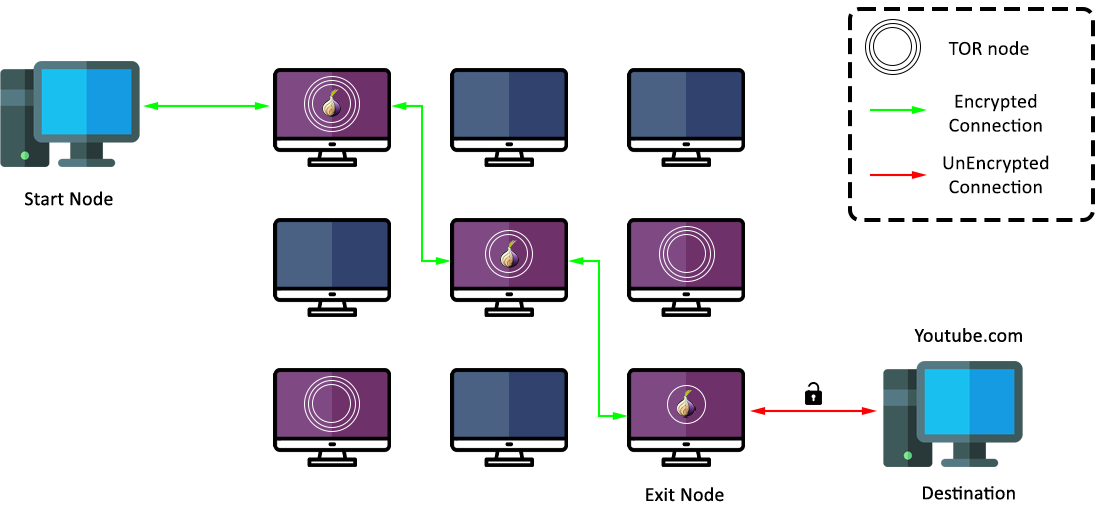
1. Entry Node (Guard Node): Your request first reaches an entry node, which knows your IP address but not what you're looking for. It peels off the first layer of encryption, revealing the next destination but not the final one.

2. Middle Node (Relay Node): The request then passes through a series of middle nodes, each of which removes another layer of encryption and forwards the request to the next node. This process continues until the innermost layer of encryption is removed.

3. Exit Node: Finally, your request reaches the exit node. This node removes the last layer of encryption and sends your request to the final destination. The exit node knows the website you're accessing but not who you are.

Exit Nodes are the final relay points before your request reaches the internet. They decrypt the last layer of encryption and send your request to the intended destination. Since they deal with unencrypted data, exit nodes are often subjected to scrutiny and legal challenges.
Now, we understand how a client or visitor’s web request goes through different encrypted layers and protects the visitor’s identity, but what about the website’s owner? Is his identity protected? Let’s see.
Why are .onion Websites Hard to Trace?
When we talk about the internet, most of us think about websites ending in .com, .org, or similar. These sites are part of the "surface web," easily accessible and indexed by search engines. However, .onion websites are part of the "dark web," accessible only through the Tor browser. The key difference lies in how data travels and the level of anonymity.
Check my article on What is the Dark Web | Is Dark Web Illegal? - An Introduction to understanding everything about the Dark web, Surface web and Deep web in depth.

These are the main 4 reasons why .onion-hosted websites are very difficult to trace down :
- Every .onion Website Has Its Unique Address: Imagine your home address, but instead of numbers and street names, it's a mix of random letters and numbers. That's how .onion addresses look. for example r76ryrdvythrhbo.onion
They are special addresses that come from a website's public key. Only the person with the matching private key, like a secret password, can use the website. This makes it hard for anyone else to mess with the site or even find out who's running it.
- Secret Codes Called Hidden Service Descriptors: For a .onion website to talk to its visitors, it puts out a hidden service descriptor on Tor's distributed hash table (DHT). Think of it as a secret map that shows how to get to the website.
But, this map is locked in a box (encrypted), and only those who already know the address (.onion) can open the box and see the map. This keeps the website's location a secret from everyone else.
- How Users Connect to .onion Websites: When someone wants to visit a .onion website, their Tor browser does some detective work. It goes to the DHT, finds the hidden service descriptor, and figures out how to connect to the website.
This process is like finding and following a secret path that only you and the website know about, keeping both of you hidden from others.
- Meeting at a Secret Spot: The Rendezvous Point: Finally, the users of the Tor browser and the .onion website agree to meet at a secret spot in the Tor network, called a rendezvous point. This is like agreeing to meet a friend at a hidden cafe where no one can find you.
The conversation between the user and the website happens here, secretly and safely, without anyone else knowing where you are or what you're talking about.
Conclusion
Tor stands as a vital tool for preserving online privacy and freedom. Its onion routing and .onion hosting exemplify its commitment to anonymity. In our next instalment, we'll delve into how Tor generates .onion addresses and randomizes user IPs, underscoring its dedication to privacy. Let's continue championing Tor's principles of empowerment and innovation in the digital realm.
Commonly Asked Questions
Q1. If I use Tor to Visit any website, will my original IP used as a exit node of some criminal?
Ans. Tor does not "use" your IP as an exit node unless you've configured your Tor relay to act as one. The IPs seen are those of volunteer-operated Exit Nodes.
Q2. From Where Tor Creates these Fake Ips to hide our real IP?
Ans. Tor's "fake IPs" are actually the real IPs of the Exit Nodes. The network relies on volunteers around the world who run these nodes.
Q3. Why Can't Goverment just Ban All Tor IPs?
Ans. Banning Tor IPs is challenging due to the network's global and decentralized nature. Moreover, new nodes can be set up, and existing ones can change their IPs.
Q4. How many Number of IPs Tor have?
Ans. The number of IPs in Tor is dynamic, reflecting the current number of active nodes. This number changes as nodes join or leave the network.
Related Blogs
- What is the Dark Web | Is Dark Web Illegal? - An Introduction
- What is Tor | How to Use Tor Browser?
- How to Access Dark Web | Use Dark Web Links Safely
- What is Tor? | How Does it Work? | Everything About Tor Network
- How are TOR Onion Hidden Addresses Created | How Does it Work?
- Vulnerabilities in Tor | Is the Tor Browser Safe?
- OWASP ZAP | A Powerful Web Application Security Testing Tool
- What is Wireshark | How to Use Wireshark [Practical Demo]
- How to Install Kali Linux Step By Step Guide
- What is Computer Network | Basics of Networking [With Practical Examples]
- Types of Network Topology with Network Topology Diagram | Techofide
- What is DoS Attack | How to do Denial of Service Attack [Practical Demo]
- Nmap Commands | How to Use Nmap Tool
- Linux Commands | Linux Commands Cheat Sheet
- What is OSINT? | OSINT Framework | Tools for OSINT | Best OSINT Techniques