Hello Cyber learners,
Ever wondered how these special .onion addresses work or how Tor keeps your online activities private? In this blog, we'll explore how Tor does its magic, from creating those unique .onion addresses to keeping your browsing anonymous and secure. We'll talk about how Tor shuffles your IP address like a deck of cards, and why it's allowed in places like China and North Korea despite attempts to block it. So, let's dive in and uncover the secrets of Tor.
- How are Onion Addresses Generated?
- How is Rendezvous Point Generated?
- Which Encryptions are used by Tor?
- The Process of Randomizing IPs and Tor Circuits
- Nodes and Network Structure in the Tor Network
- Conclusion
- Commonly Asked Questions
Prerequisite: Before moving further, If you don't know what is .onion and what is rendezvous point, Then you should first read our pervious blog which is first part of this blog on: What is Tor? | How Does it Work? | Everything About Tor Network
How are Onion Addresses Generated?
The unique .onion address of a website is derived from its public key, specifically using a portion of the hash of the public key. Here's a simplified overview:
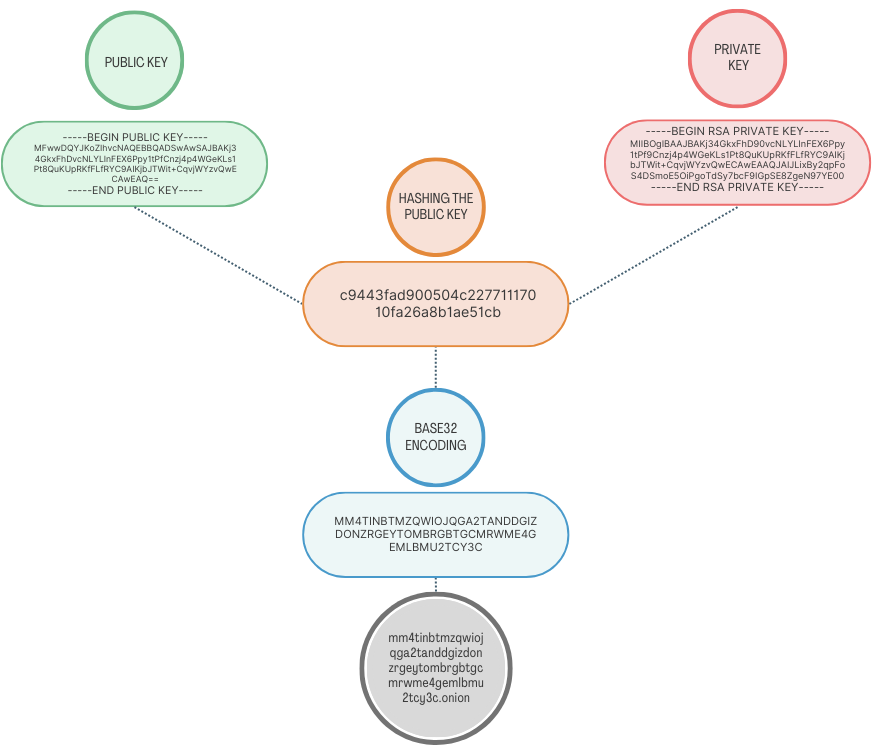
- Public Key Generation: The .onion service generates a cryptographic key pair (public and private keys). As you can see in the image, the process starts with 2 cryptographic keys.
- Hashing the Public Key: As you can see in the image, A hash of the public key is computed. This hash function outputs a fixed-size string.
- Base32 Encoding: A portion of this hash is then encoded using Base32, resulting in the .onion address. This ensures the address is a human-readable string.
What is Public Key?
Public key is like a digital lock that keeps websites and online transactions safe. It's part of a pair of keys used in encryption, where the public key is shared openly to encrypt data, while the private key is kept secret by the website owner to decrypt it. This ensures that only the intended recipient can read the encrypted information.
What is Hashing?
Hashing is like creating a secret code for data. It transforms information into a unique string of characters, making it difficult for anyone to reverse-engineer the original data from the hash.
Now, let's understand how a rendezvous point is generated, which plays a critical role in connecting users with the .onion hosting server while keeping both parties anonymous from each other.
How is Rendezvous Point Generated?
The process for establishing a rendezvous point between a user and a .onion service involves several steps:
1. Service Descriptor: The .onion service publishes a service descriptor to the Tor network's distributed hash table (DHT). This descriptor contains the service's public key and information on how to initiate communication.
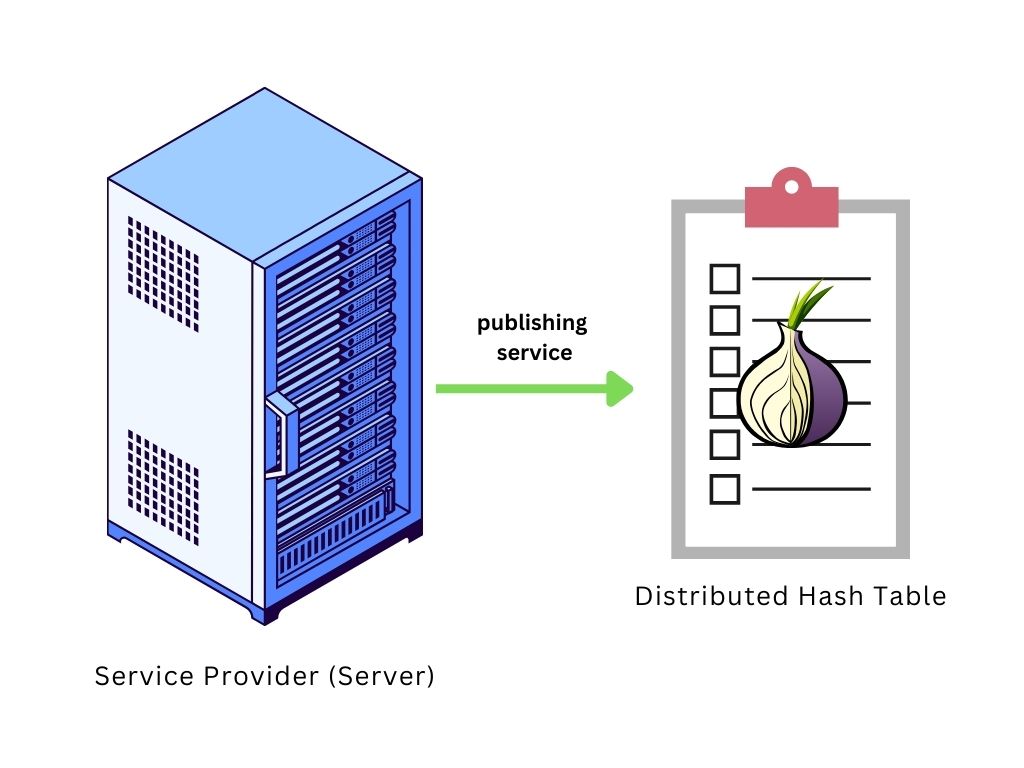
2. Client Lookup: On the client side, When a user wants to access the .onion service, their Tor client retrieves the service descriptor using the .onion address.
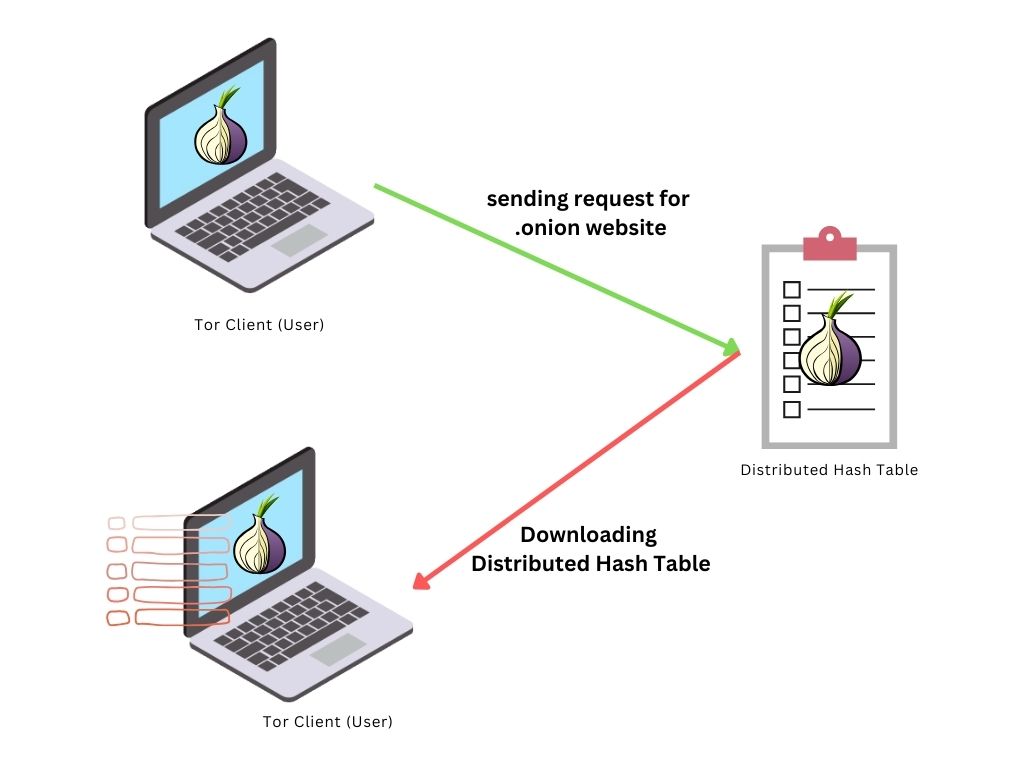
3. Rendezvous Point Selection: The user's Tor client(Tor browser) selects a Tor node to act as a rendezvous point.
Also, it sends a "rendezvous message" from the Distributed Hash Table (Which it downloaded in 2nd step) to the onion service, to inform it of the selected rendezvous point.
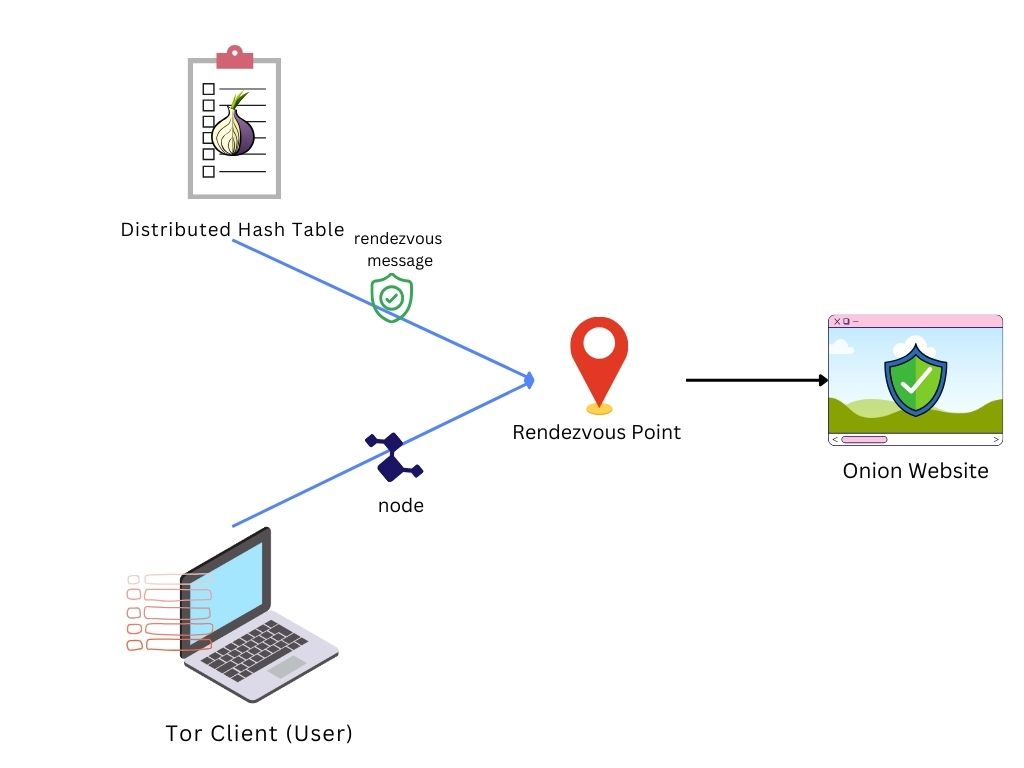
4. Secure Connection: The .onion service then establishes a circuit to the rendezvous point, and the user's client does the same. Both circuits meet at the rendezvous point, allowing secure and anonymous communication between the user and the .onion service.
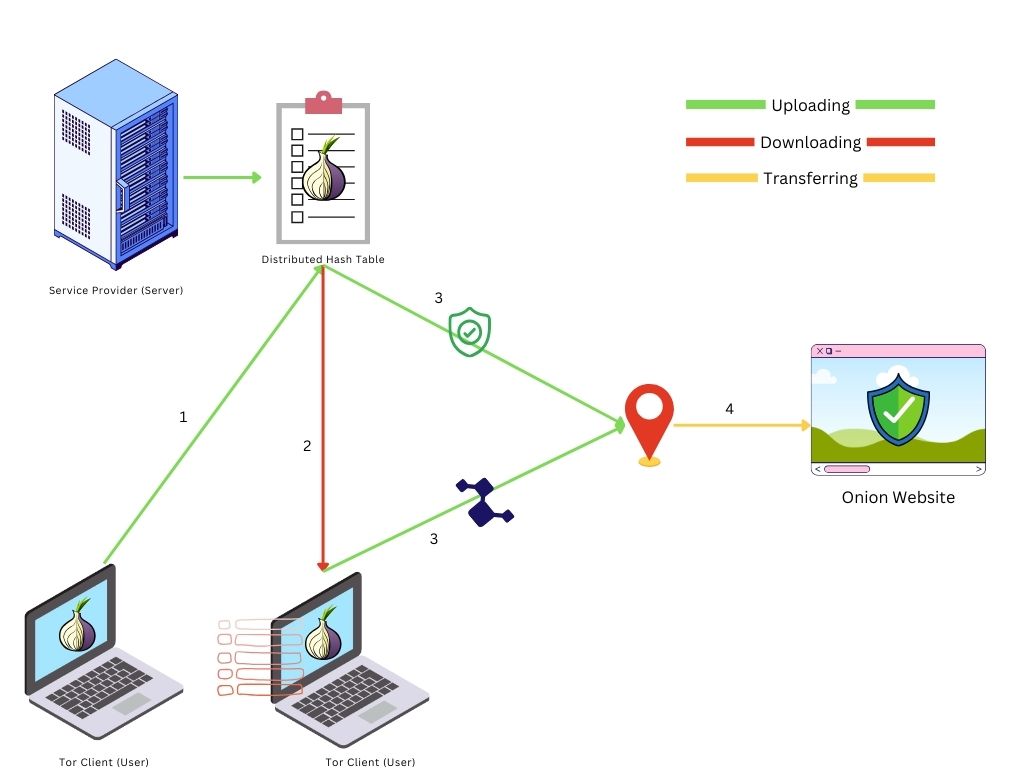
This process ensures that the actual IP addresses of the user and the .onion service remain unknown to each other, maintaining anonymity.
Now, let's understand some key encryption algorithms used by Tor.
Which encryptions are used by Tor?
Tor employs a variety of encryption algorithms throughout its network to ensure secure and private communication.
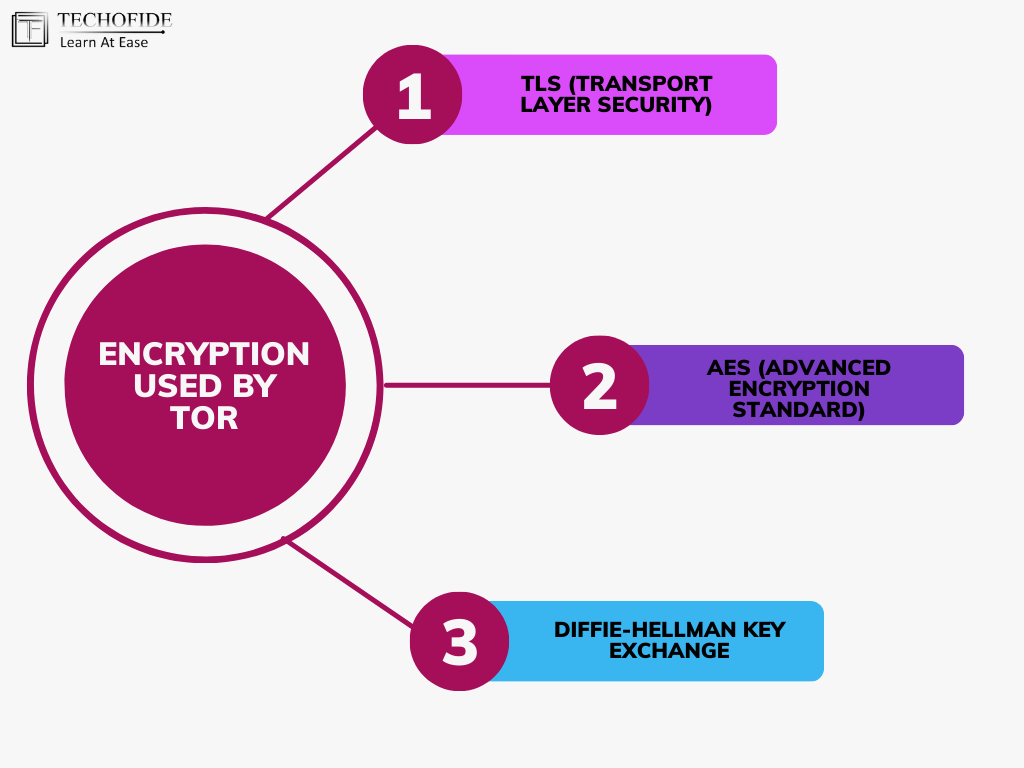
The primary encryption used for the layered encryption (or onion routing) process includes:
TLS (Transport Layer Security): For securing connections between Tor nodes. TLS is not specific to Tor; it's widely used on the internet for securing web traffic.
AES (Advanced Encryption Standard): Often used for the symmetric key encryption of data packets as they traverse the Tor network. AES is known for its speed and security, making it suitable for Tor's purposes.
TLS and AES are both used in many regular activities online, like when you log in to your email, shop online, or even use social media. It's what keeps your information safe and secure while you're browsing the web or sending messages.
Diffie-Hellman Key Exchange: Used for securely exchanging cryptographic keys over a public channel. This is part of the process for establishing encrypted connections between nodes.
So, now you know how Tor connection works, which encryptions Tor uses and how all IPs involved in this process remain anonymous. Let's explore a few more common queries:
1. Where does these IPs comes from?
2. Does Tor have a database of these fake IPs?
3. Are they using their user’s Ips?
4. Will my ip get blacklisted if I use Tor?
let’s understand all this in detail.
The Process of Randomizing IPs and Tor Circuits
Tor achieves IP anonymity by dynamically creating circuits through the Tor network. These circuits are random paths that each data packet travels through, making it nearly impossible to trace back to the original user. A Tor circuit typically lasts for about 10 minutes before a new one is established, further enhancing anonymity.
Tor employs several measures to prevent IP addresses from being traced back to users, ensuring a high degree of anonymity and privacy. Here's an overview of the key mechanisms in place:
Randomized Path Selection
When a user connects to the Tor network, their client software (Tor Browser) builds a circuit through the network, selecting nodes at random. This circuit consists of an entry node, one or more middle nodes, and an exit node.
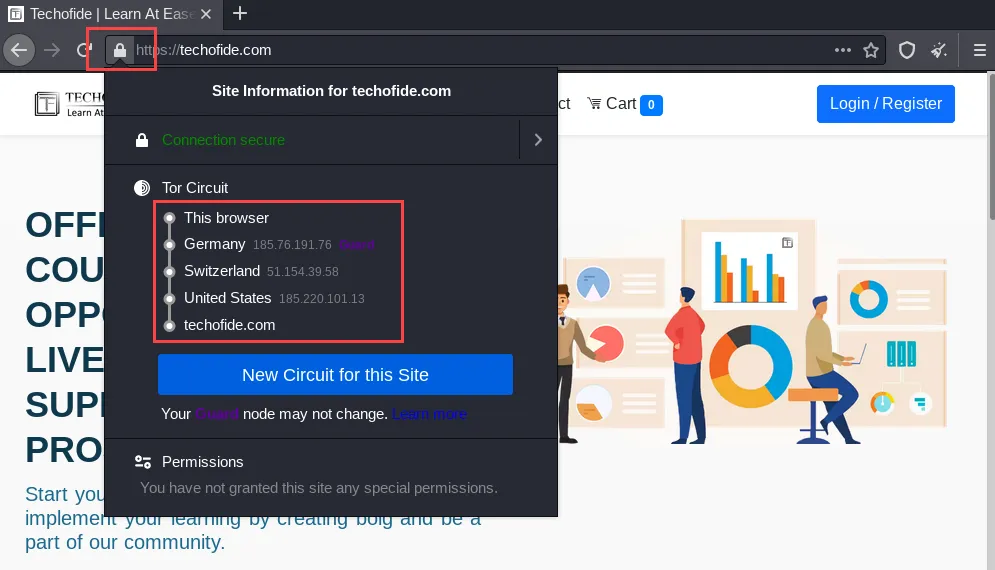
These circuits are temporary and change periodically (every 10 minutes by default), or when starting a new browsing session. This frequent change of paths further complicates any attempt to trace the activity back to a user.
No Direct Connection
By routing the user's internet traffic through multiple nodes (at least three), Tor ensures that there is no direct connection between the user's computer and the internet resource they are accessing. This prevents external observers from easily linking an action on the internet back to the user.
Use of Bridges and Pluggable Transports
- Bridges: For users in regions where Tor is blocked or monitored, Tor provides "bridges," which are unpublished entry nodes not listed in the main Tor directory. This makes it harder for governments or ISPs to block access to the Tor network.
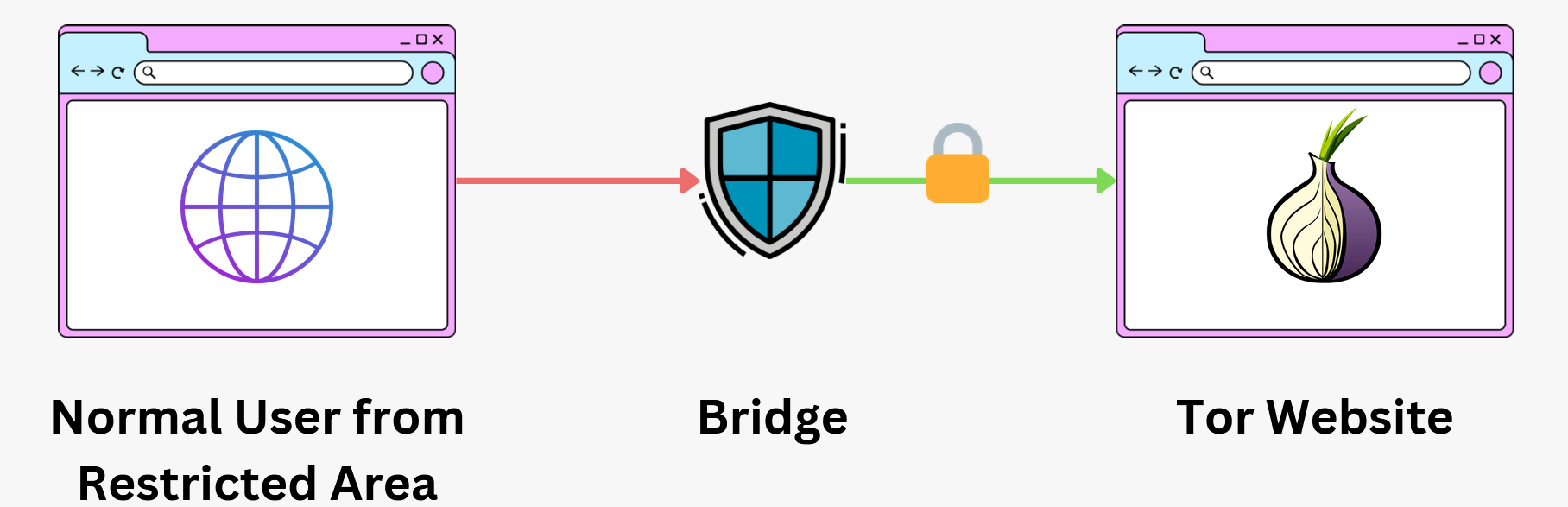
- Pluggable Transports: These are techniques that disguise Tor traffic to look like regular internet traffic, helping users bypass censorship and deep packet inspection (DPI) that could identify and block Tor usage.
So, now we know how Tor randomize IP addresses. but you might have more queries like:
1. How does it create an IP chain from these IPs?
2. How does it pass our request from these random IPs?
Let's understand it in detail.
Nodes and Network Structure in the Tor Network
The Tor network is made up of thousands of volunteer-run servers, known as nodes.
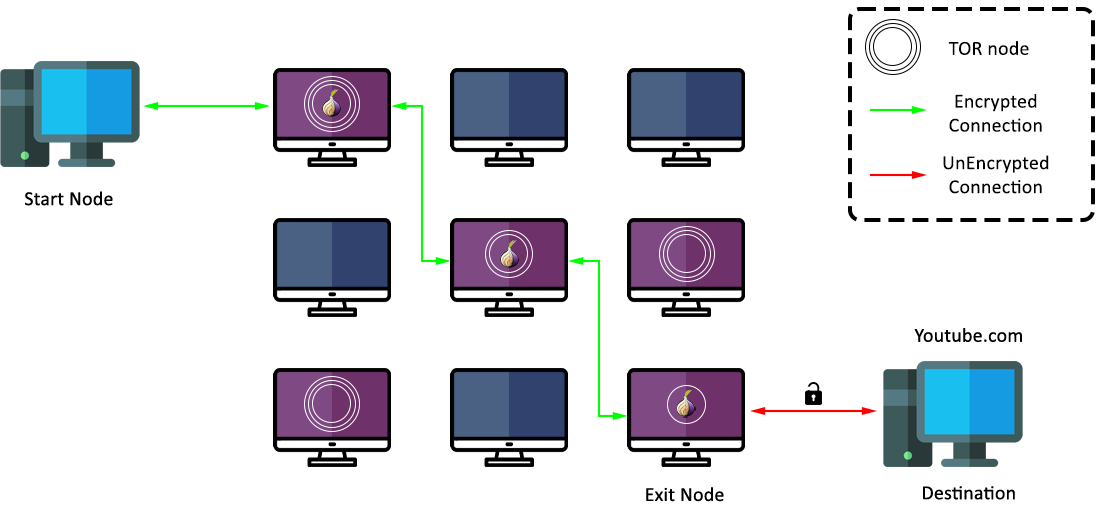
These nodes are the unsung heroes, ensuring your online activities remain private and secure. There are four main types of nodes in the Tor network:
1. Bridge Nodes: These are the undercover agents of the Tor world. Bridge nodes help users in regions where Tor is blocked to access the network undetected. They're not listed publicly, making it harder for censors to block them. These are only available in countries that blocked Tor.
2. Guard (Entry) Nodes: Think of guard nodes as the trusted gatekeepers of your Tor journey. When you start using Tor, your connection is first routed through a guard node. It's like entering a secure, secret tunnel. Your computer knows this node, but it doesn't know where you're headed next.
3. Middle Nodes: After the guard node, your connection hops to one or more middle nodes, also known as relays. These nodes pass your encrypted data around the globe, making it increasingly difficult for anyone to trace your steps.
4. Exit Nodes: The final leg of the journey. Exit nodes are where your connection leaves the Tor network and reaches the open internet. It's like stepping out of the secret tunnel into the destination you wanted to visit, but without leaving any footprints.
The strength of the Tor network lies in its diversity and global spread. With nodes located all around the world, Tor can route your data through multiple countries, adding layers of complexity to the tracking process. This geographic distribution also helps in balancing the load, ensuring no single node becomes a bottleneck.
The diversity in node types and locations makes it challenging for governments or organizations to block or control the network. It's like playing a global game of hide and seek, where Tor users have the upper hand.
Conclusion
We explored the fascinating world of Tor, learning how it keeps our internet activities private and secure. Tor creates special addresses called .onion addresses and mixes up our IP addresses to protect our privacy online.
Stay tuned as we uncover more secrets about how Tor works to keep us safe online.
Commonly Asked Questions
Q1. How are .onion addresses generated, and can they be traced back to their origin?
Ans. Onion addresses are derived from public keys and are designed to be untraceable. While they provide a level of anonymity, it's important to remember that no system is entirely foolproof.
Q2. Will using Tor result in my IP address getting blacklisted?
Ans. Tor employs randomized IP addresses and circuits, making it difficult for websites to identify and blacklist individual users. However, some services may choose to block Tor exit nodes to prevent abuse.
Q3. Why is Tor allowed in countries like Russia, China, and North Korea? Can't governments ban Tor IPs?
Ans. Tor's decentralized nature and use of bridges and pluggable transports make it challenging for governments to block entirely. While some countries may attempt to restrict access, Tor's global network of nodes allows users to circumvent censorship efforts.
Related Blogs
- What is the Dark Web | Is the Dark Web Illegal? - An Introduction
- What is Tor | How to Use Tor Browser?
- Vulnerabilities in Tor | Is the Tor Browser Safe?
- OWASP ZAP | A Powerful Web Application Security Testing Tool
- What is Wireshark | How to Use Wireshark [Practical Demo]
- How to Install Kali Linux Step-By-Step Guide
- What is Computer Network | Basics of Networking [With Practical Examples]
- Types of Network Topology with Network Topology Diagram | Techofide
- What is DoS Attack | How to do Denial of Service Attack [Practical Demo]
- Nmap Commands | How to Use Nmap Tool
- Linux Commands | Linux Commands Cheat Sheet
- What is OSINT? | OSINT Framework | Tools for OSINT | Best OSINT Techniques