Hello Cyber Learners,
Welcome to our website hacking blog series, where we will explore the fascinating world of website security and hacking. In this series, we will delve deep into the intricacies of how websites work and how hackers exploit vulnerabilities in websites to gain unauthorized access. this blog series is designed to cater to everyone interested in website hacking, from beginners to advanced security professionals.
In this blog, we will introduce you to the exciting world of website hacking and provide you with an overview of our entire series. We will start by discussing what website hacking is and why it's important to learn about it. We'll then guide you through the process of setting up the necessary tools and software required for website hacking. This includes installing Kali Linux, a popular operating system used for ethical hacking, and other tools such as Burp Suite, nikto, and sublister. Once we have everything set up, we'll give you a brief overview of what to expect in the rest of the series.
- What is Website Hacking?
- What is Bug Bounty?
- Types of Website Hacking
- Requirements for Website Hacking
- Web Application Penetration Testing Lab Setup
- Tools Required for Website Hacking
- Implications of Website Hacking
- Practical Examples
- Conclusion
- Commonly Asked Questions
What is Website Hacking?
Website hacking refers to the process of exploiting vulnerabilities in a website's code or infrastructure to gain unauthorized access or control. It can be used for various malicious purposes, such as stealing sensitive information, defacing websites, distributing malware, or launching denial-of-service attacks.

Website hacking has become a significant threat to online security in recent years. Hackers use various techniques to exploit vulnerabilities in websites to gain unauthorized access and steal sensitive information.
What is Bug Bounty?
A bug bounty is a program offered by companies to encourage security researchers or ethical hackers to find and report vulnerabilities in their websites or software. The objective of these programs is to identify security flaws and fix them before they can be exploited by malicious actors. These programs offer rewards to individuals who discover vulnerabilities, ranging from recognition to monetary compensation.
Bug bounty programs are a proactive approach to cybersecurity, as they allow companies to identify and fix vulnerabilities before they are exploited by attackers. By encouraging researchers to report vulnerabilities, companies can ensure that their websites and software are secure and reliable. To read more about this topic, you can visit my blog post on OSINT Framework | OSINT for Bug Hunters [Practical Demo] Part 1

Bug bounty programs have gained popularity in recent years, with major companies such as Google, Microsoft, and Facebook offering them. The rewards offered by these companies range from a few hundred dollars to tens of thousands of dollars, depending on the severity of the vulnerability. Some companies even offer recognition or job offers to researchers who find significant vulnerabilities.
Types of Website Hacking
There are several types of website hacking techniques that hackers use to exploit vulnerabilities in websites. we can divide all techniques into three parts:
1. Server-side attacks: Server-side attacks are targeted at the server-side components of a web application.

These attacks aim to exploit vulnerabilities in the server's software, configuration, or operating system to gain unauthorized access, steal sensitive data, or execute malicious code. Some common server-side attacks include:
- SQL injection
- Authentication Vulnerabilities
- Directory Traversal
- Command Injection
- Business Logic Vulnerabilities
- Information Disclosure
- Access Control
- File Upload Vulnerabilities
- Server-side Request Forgery (SSRF)
- XXE Injection
- NoSQL Injection
- GraphQL Injection
- LaTex Injection
2. Client-side attacks: Client-side attacks target the end-users web browser or device to execute malicious code, steal sensitive data, or gain unauthorized access.

Some common client-side attacks include:
- Cross-Site Scripting(XSS)
- Cross-Site Request Forgery(CSRF)
- Cross-Origin Resource Sharing(CORS)
- Clickjacking
- DOM Based Vulnerabilities
- WebSockets
- HTML Injection
- Open Redirect
- Session Hijacking
- Parameter Tampering
3. Advanced attacks: Advanced attacks are complex and sophisticated attacks that use multiple techniques and exploits to gain access to a web application.
Some common advanced attacks include:
- Insecure deserialization
- Server-Side Template Injection (SSTI)
- Web Cache Poisoning
- HTTP Host Header Attack
- HTTP Request Smuggling
- OAuth Authentication
- JWT Tokens Vulnerabilities
- Prototype Pollution
- LDAP Injection
- CRLF
- CSV Injection
- Crypto Bugs
- API Key Leaks
- Amazone S3 Bucket Bugs
- DNS Rebinding
- Insecure Management Interface
- Java RMI
- Race Condition
- SAML Injection
- Type Juggling
- Tabnabbing
- Web Sockets
- XPATH Injection
- XSLT Injection
This is just a small list, there are many bugs still left. we will cover them one by one in this blog series.
Requirements for Website Hacking
Before moving further, let's install some tools which are required in web application pen testing.
Kali Linux
Kali Linux is a specialized operating system developed for penetration testing and ethical hacking purposes. It is an open-source distribution based on Debian and includes a wide range of tools and frameworks that are useful for various hacking techniques, including web hacking. The system includes tools for reconnaissance, vulnerability scanning, exploitation, and post-exploitation, among other things.
Kali Linux is an essential tool for web hacking and bug bounty, and it's important to get it set up correctly before you begin your journey. So, if you're unsure of how to install Kali Linux, head over to my blog post How to Install Kali Linux [Step by Step Installation Guide] and follow the instructions. With Kali Linux installed, you'll be ready to start learning and practicing your web hacking skills.
Pen-test Lab Setup
As you start your journey into the world of website hacking, it's important to have a safe and legal environment to test your skills and techniques. for this blog series, we will use many labs, some are online and some are hosted on your local machine. installing them one by one will take a lot of time, also you will face many errors.
To help you with this, I provided the pentest lab installing script. After you install Kali, you can use this script to set up intentionally vulnerable websites so you can safely practice your hacking skills on. These websites have known vulnerabilities that can be exploited to gain unauthorized access, steal data, or execute malicious code. By practicing on these pentest labs, you can hone your skills and learn about different hacking techniques without worrying about breaking any laws or harming real websites.
Adrishya-labs
Adrishya-lab is an easy-to-install script for pentest labs. it's basically a bash script to manage web apps using docker and hosts aliases. Made for Kali Linux, but it should work fine with pretty much any Linux distro. in this tool, we can install a total of 10 vulnerable web applications, and it will host each one on your localhost with different IPs and ports.
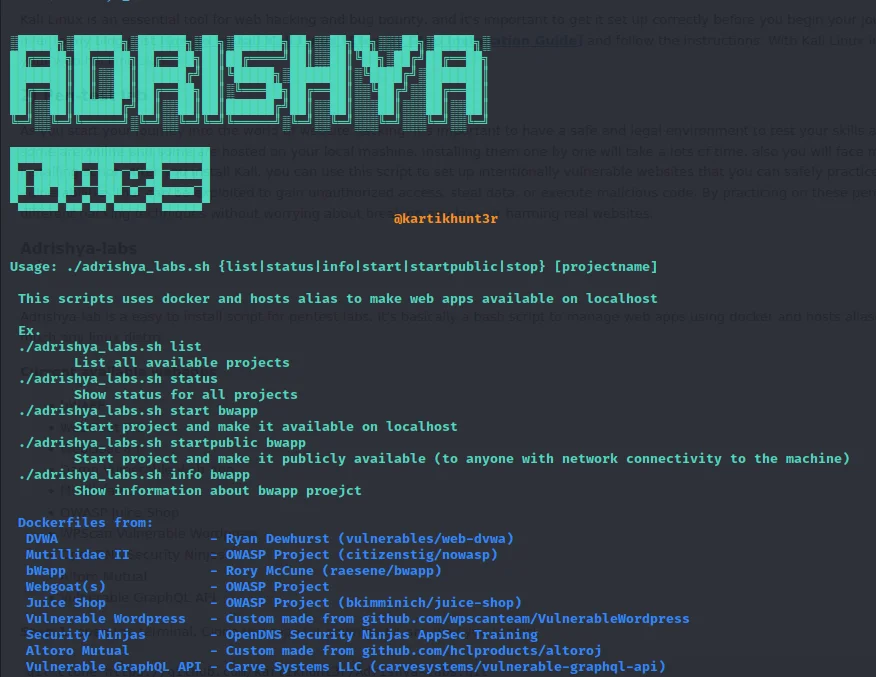
Adrishya Labs includes the following vulnerable webapps:
- bWAPP
- WebGoat 7.1
- WebGoat 8.0
- Damn Vulnerable Web App
- Mutillidae II
- OWASP Juice Shop
- WPScan Vulnerable WordPress
- OpenDNS Security Ninjas
- Altoro Mutual
- Vulnerable GraphQL API
Web Application Penetration Testing Lab Setup
So If you have an installed Linux we can start the lab setup with the installation of Adrishya labs.
Step 1: Open the terminal, Clone this repo. (or download it any way you prefer)
git clone https://github.com/kartikhunt3r/Adrishya-labs.git
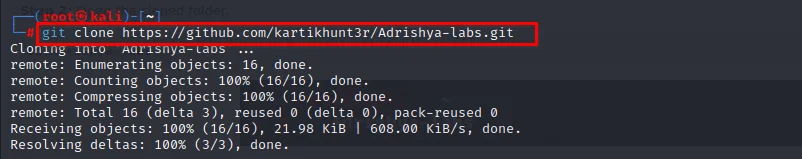
you can see download is started after running the command.
Step 2: Open the cloned folder.
cd Adrishya-labs

Step 3: Install Docker.
sudo apt install docker.io
Question: What is Docker and why we are using it?Ans: Docker provides an efficient way to package and distribute applications, enabling developers to build and deploy their applications quickly and consistently across different environments, such as development, testing, and production.Hosting a web pen test lab environment is a challenging task, especially when dealing with various operating systems, software versions, and dependencies. with my personal experience, it is a headache for bigginers who dosen't know much about web servers. Docker can help simplify this process and provide a flexible, portable, and scalable solution. By leveraging Docker, we can create isolated containers that contain all the necessary tools, libraries, and configurations for our pen test lab environment, without worrying about compatibility issues or conflicts.
Now our installation is complete.
Now, you can install any of these labs.
For example, I am installing bwapp.
./adrishya_labs.sh start bwapp
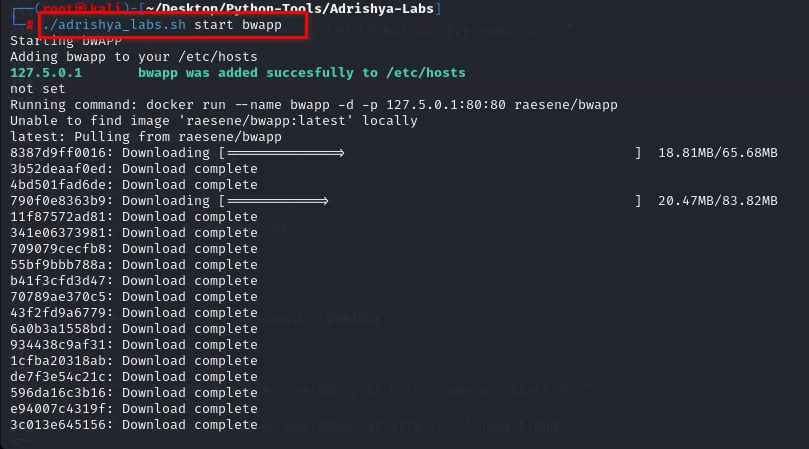
This will add bwapp to hosts file and run the docker mapped to one of the localhost IPs. That means you can just point your browser to http://bwapp and it will be up and running.
Use the startpublic command to bind the app to your IP
./adrishya_labs.sh startpublic bwapp
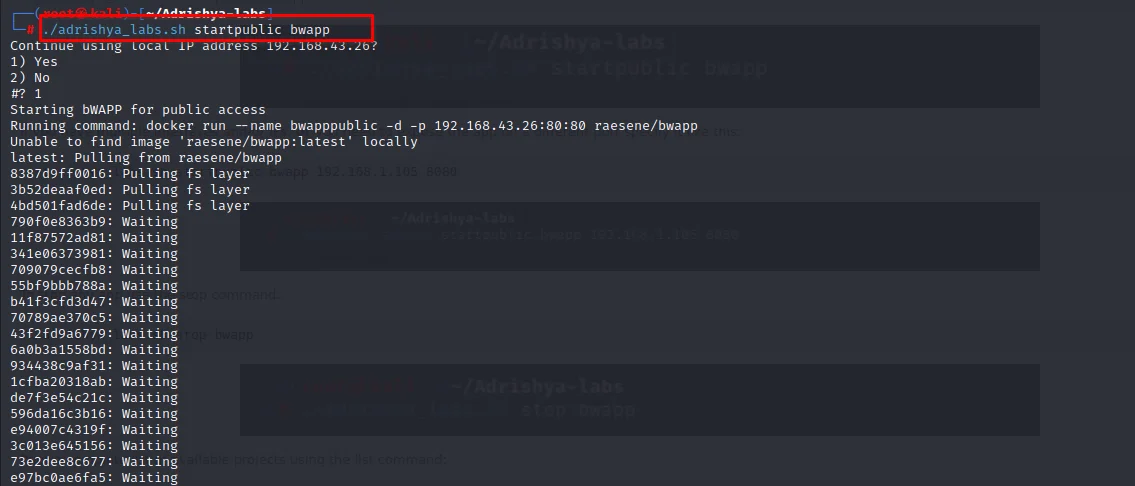
If you have multiple interfaces and/or IPs, or you need to expose the app on a different port specify it like this
./adrishya_labs.sh startpublic bwapp 192.168.1.105 8080
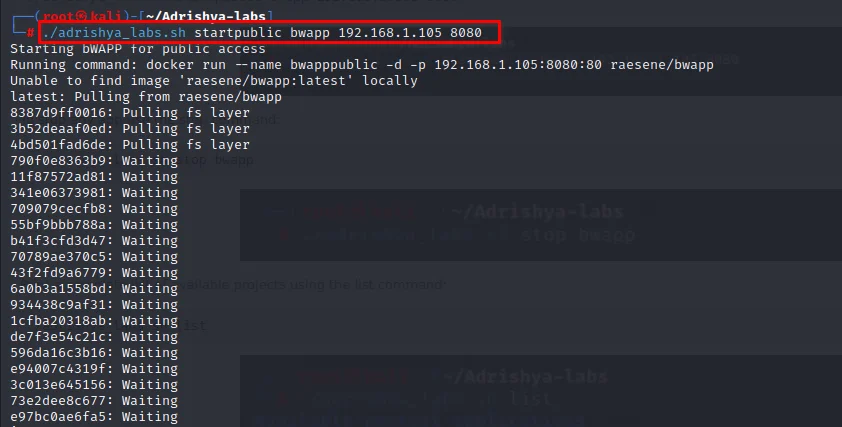
To stop any app use the stop command
./adrishya_labs.sh stop bwapp
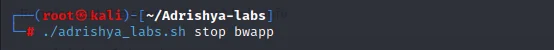
Print a complete list of available projects using the list command
./adrishya_labs.sh list
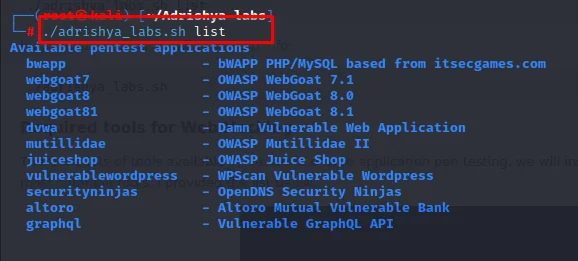
Running just the script will print help info
./adrishya_labs.sh
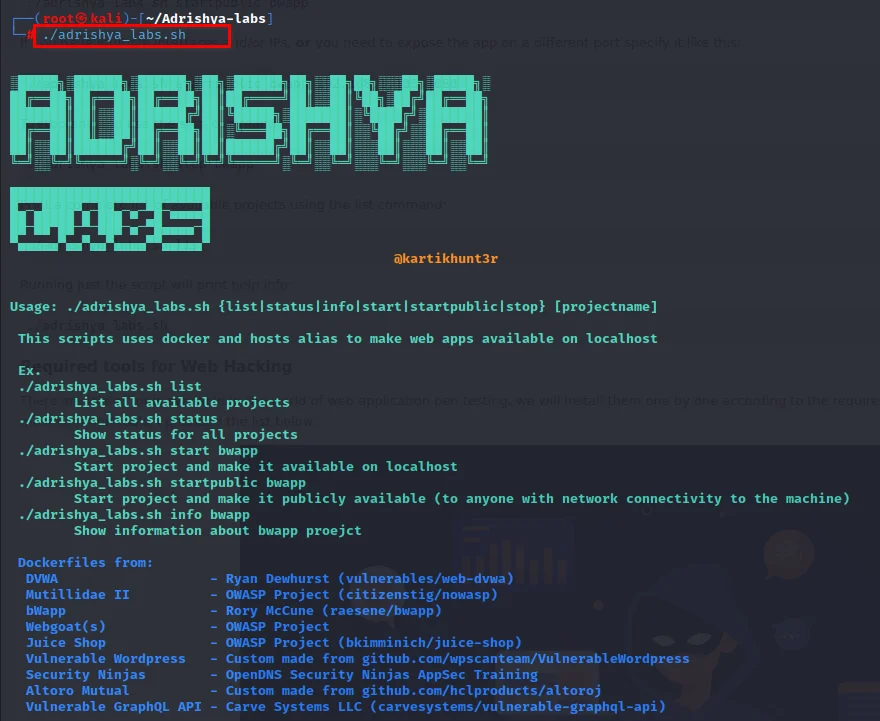
Tools Required for Website Hacking
There are lots of tools available in the world of web application pen testing, we will install them one by one according to the requirements in this series, but for now, you have to install some most common tools, I provided the list below.

- Burpsuite: A popular web application testing tool used for analyzing and manipulating HTTP traffic. for more information, you can read our blog on this: What is Burp Suite | How to use Burp Suite | Burp Suite Tutorial for Beginners
- Weevly: A tool used for web application security testing, to make php web shells and reverse proxy shells.
- Nikto: A web server scanner designed to identify vulnerabilities and potential security issues.
- Sublister: A Python-based tool used to enumerate subdomains for a given domain, allowing for reconnaissance during the information-gathering phase of web hacking.
- MassDNS: A high-performance DNS stub resolver that can be used for reconnaissance and enumeration of subdomains.
- Photon: A tool used for web application discovery, which uses various techniques to crawl and extract data from websites.
- Subfinder: A subdomain discovery tool that uses various techniques to gather information about subdomains.
- Smuggler: A tool used for detecting and exploiting HTTP request smuggling vulnerabilities in web applications.
- VSCode: A popular code editor that can be used for scripting and automation during web application testing and penetration testing.
If you installed Kali Linux already, then you will get burpsuite, weevly and nikto pre installed in it.
Browser extensions:
- FoxyProxy: A tool used to easily switch between different proxy servers for web traffic. read more ...
- NoScript: A security tool used to block JavaScript, Java, and other executable content on websites to prevent potential security risks.
- uBlock Origin: A lightweight ad blocker and privacy tool that can block unwanted content and improve website loading times.
- Cookie AutoDelete: A privacy tool used to automatically delete cookies when a website is closed, helping to protect against tracking and other security risks.
- User-Agent Switcher: A tool used to modify the browser user-agent string, allowing for more advanced web application testing and bypassing certain security measures.
- Wappalyzer: A web application analysis tool used to identify the technologies and frameworks used by websites.
- Tamper Data: A tool used to intercept and modify HTTP/HTTPS requests and responses, allowing for more advanced web application testing.
- HackBar: A web security tool used to perform various security-related tasks, such as encoding and decoding text, hash cracking, and XSS testing.
once you have installed all this, you are good to go.
Implications of Website Hacking
Website hacking can have severe implications for both individuals and organizations. Here are some of the most significant implications of website hacking:
- Data Theft: Hackers can steal sensitive information, such as personal data, financial information, or trade secrets, through website hacking.
- Reputation Damage: A successful website hack can damage an organization's reputation and erode customer trust, leading to lost business.
- Legal and Financial Consequences: Organizations that fail to protect their websites from hacking may face legal and financial consequences, such as fines, lawsuits, or loss of revenue.
Practical Examples
To help you understand website hacking in real-world scenarios, here are some practical examples of website hacks:
Equifax Data Breach: In 2017, Equifax, a credit reporting agency, suffered a massive data breach that exposed the personal information of over 147 million people. Hackers exploited a vulnerability in Equifax's website to access sensitive data, including social security numbers, birth dates, and credit card numbers.
eBay Data Breach: In 2014, eBay suffered a data breach that exposed the personal information of over 145 million users. Hackers used stolen employee login credentials to access eBay's network and steal sensitive data.
Conclusion
In conclusion, website hacking is a serious and complex issue that can have severe consequences for individuals and organizations. In this blog, we provided an overview of website hacking, including the different types of attacks and their implications. We also highlighted the importance of ethical hacking and the need for professionals to continuously improve their skills to stay ahead of cyber attackers.
Our blog series will cover all aspects of website hacking, including practical examples and step-by-step guides to exploit vulnerabilities. We will also provide you with a safe and legal environment to practice your skills using intentionally vulnerable websites.
We hope this blog has provided you with a good introduction to website hacking, and we invite you to join us on this journey to learn more about this fascinating and important topic.
Commonly Asked Questions
Q1. What is difference between bug bounty and web hacking?
Ans. Bug bounty programs are initiatives offered by companies and organizations that encourage security researchers and ethical hackers to report vulnerabilities or bugs in their software or web applications. These programs typically offer monetary rewards to individuals who successfully identify and report security flaws that could potentially be exploited by malicious attackers.
On the other hand, web hacking is the practice of attempting to exploit vulnerabilities or weaknesses in web applications or websites with the goal of gaining unauthorized access or performing unauthorized actions. Web hacking can be performed by both ethical hackers and malicious attackers, and it can be used to steal sensitive information, hijack user accounts, or execute other malicious activities.Q2. What is web application VAPT?
Ans.Web Application VAPT stands for "Vulnerability Assessment and Penetration Testing" of a web application. It is a security testing process performed on a web application to identify vulnerabilities and security weaknesses that can be exploited by attackers to gain unauthorized access or steal sensitive information.
Related Blogs
- What is OSINT? | OSINT Framework | Tools for OSINT | Best OSINT Techniques
- OSINT Framework | OSINT for Bug Hunters [Practical Demo] Part 1
- OSINT Framework | OSINT for Bug Hunters [Practical Demo] Part 2
- What is Smurf Attack? | What is the Denial of Service Attack? | Practical DDoS Attack Step-By-Step Guide
- What is DoS Attack | How to do Denial of Service Attack [Practical Demo]
- What is Packet Sniffing? | How to Perform Packet Sniffing | Practical Demo on Wireshark
- What is Metasploit Framework | What is Penetration Testing | How to use Metasploit
- How to Install Metasploit on Windows and Linux | [Step by Step Guide]
- How to Use Metasploit | Metasploit Commands | Metasploit Tutorial