Hello cyber learners,
Welcome back to my blog! In my previous post, I shared my experience with two powerful bug bounty OSINT tools that can help ethical hackers and security researchers in their information-gathering process. if you haven't read it, you can read it here OSINT Framework | OSINT for Bug Hunters [Practical Demo] Part 1
I will teach you everything about OSINT and intelligence gathering in this blog series. I will share some practical tools and tips on how a hacker or a government agent performs an OSINT investigation. also, we will discuss the OSINT Framework, some real-life OSINT investigations, and how you can protect your identity from these Open Source Intelligence Gathering tools and remain anonymous from the government.
if you don't know what is OSINT? and why we are using it. then you can start reading from my first blog: What is OSINT? | OSINT Framework | Tools for OSINT | Best OSINT Techniques
Today, I am excited to continue the series by introducing you to two more essential OSINT tools that you should add to your toolkit. Whether you are a beginner or an experienced professional, these tools can help you in discovering and analyzing valuable information that can lead to identifying potential vulnerabilities and threats. So, let's dive in!
- DNSdumpster
- How to Use the Mapping Tool of DNS Dumpster
- Practical Tips to use DNSdumpster Effectively
- Netcraft
- How to use Netcraft
- Conclusion
- Commonly Asked Questions
DNSdumpster
DNSdumpster is a free online tool that provides information about a target's domain name system (DNS) configuration. For bug hunters, DNSdumpster can be an extremely useful resource for conducting initial reconnaissance and gathering information about a target's network and systems.
Let's see how to use DNSdumpster.
For example, we need to investigate to collect information about tesla.com
Step 1: Go to DNSdumpster
Step 2: Search for tesla.com, check the same in the below screenshot.
As you can see results are in the below image, we got a lot of information.
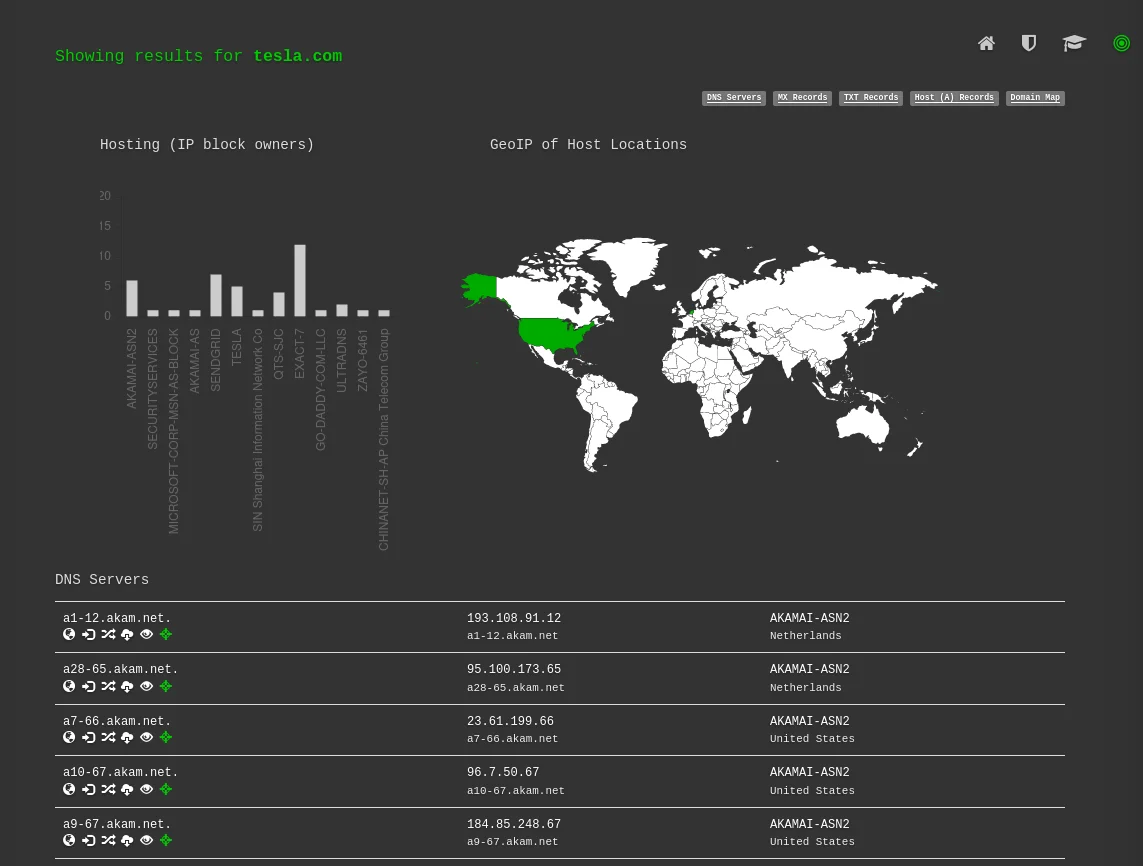
DNSdumpster also allows bug hunters to identify subdomains of a target's website, which can be valuable information for conducting a more thorough reconnaissance and identifying potential attack surfaces.
How to Use the Mapping Tool of DNS Dumpster
Go to the DNS Dumpster website and enter the target domain in the search bar. Click on the "Domain Map" tab to access the mapping tool.
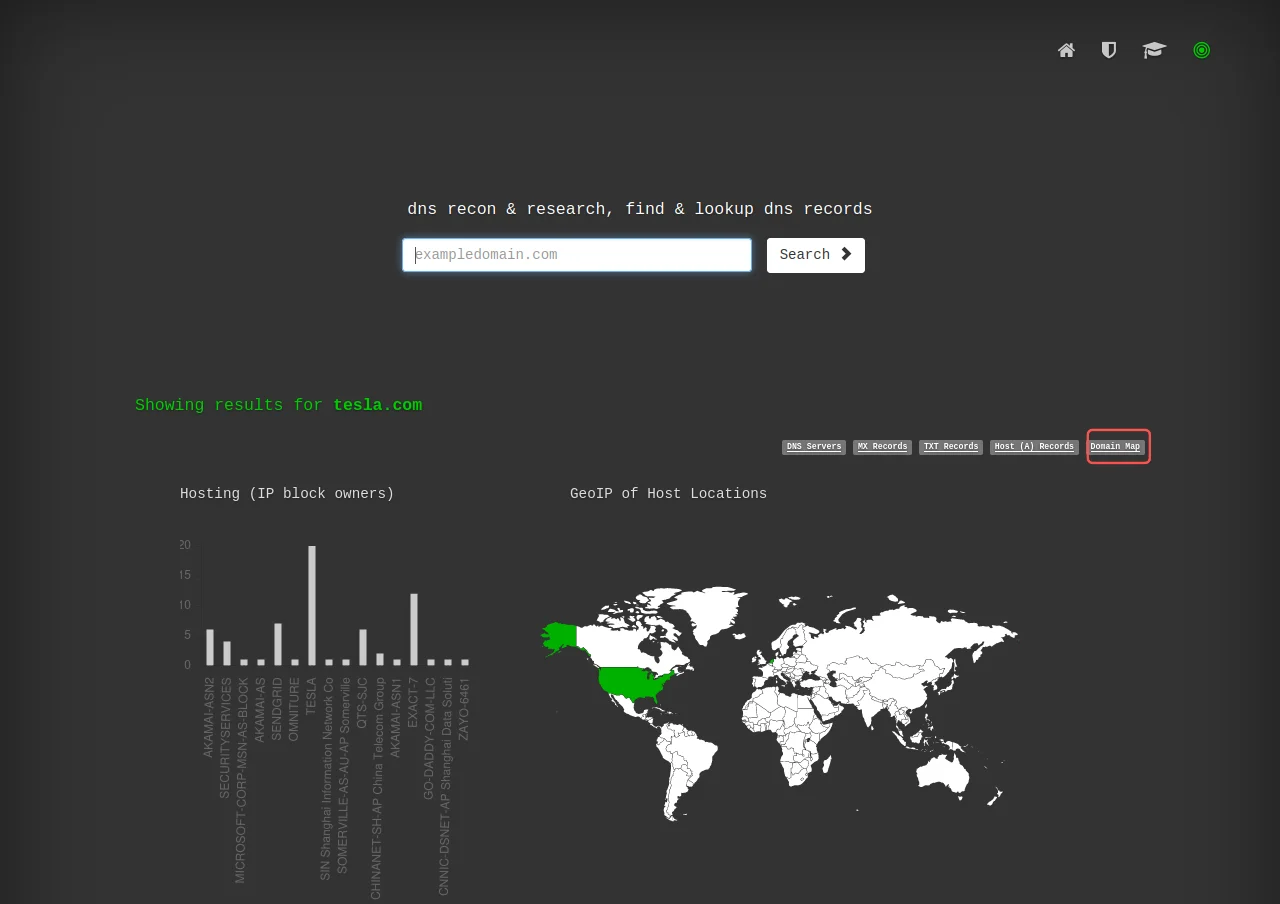
This tool also allows you to download results as .xlsx or view the graph as. HTML
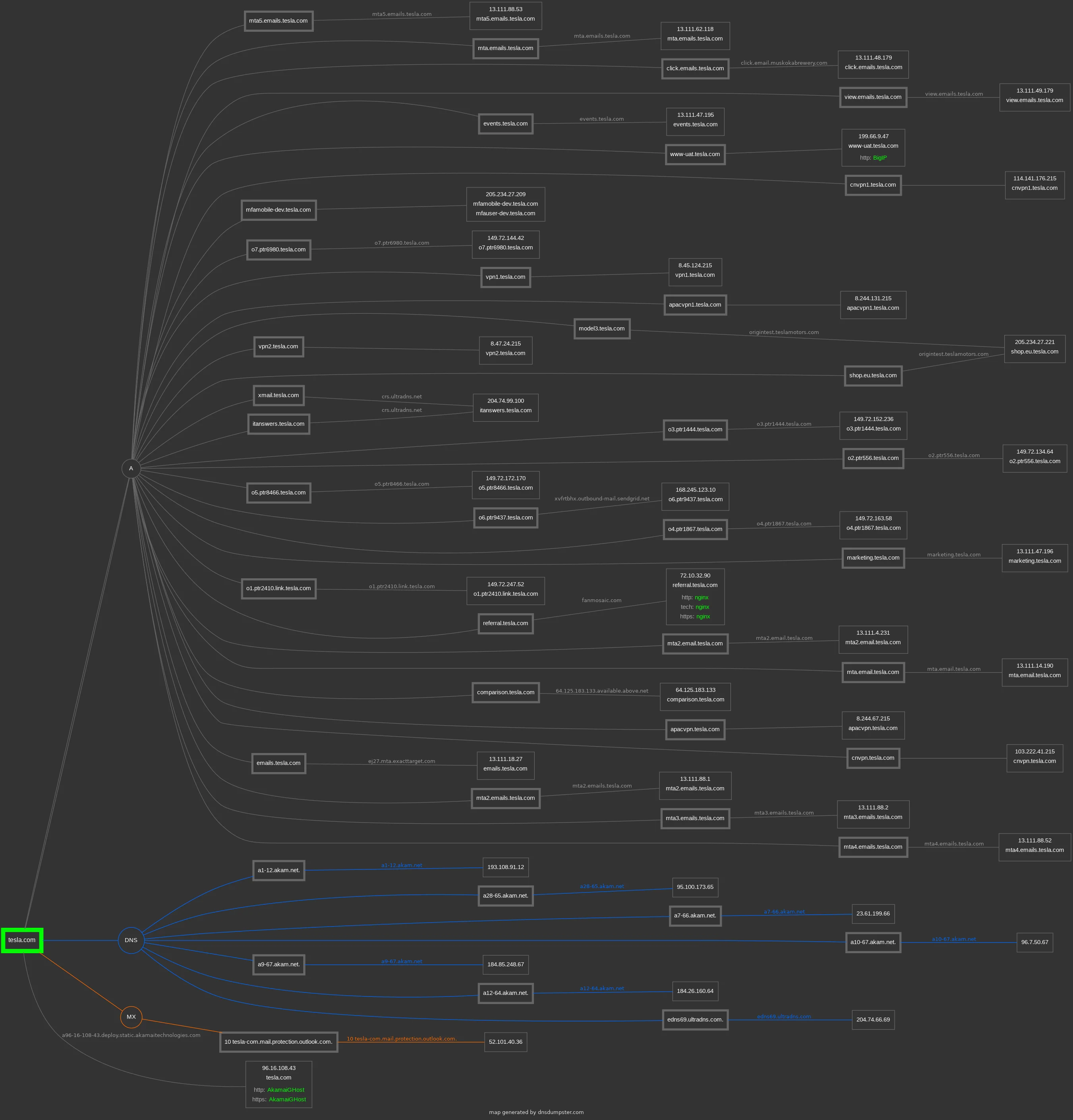
The mapping tool will display a graph that shows the relationships between subdomains and IP addresses for the target domain. The nodes in the graph represent subdomains, while the edges represent connections between subdomains and IP addresses.
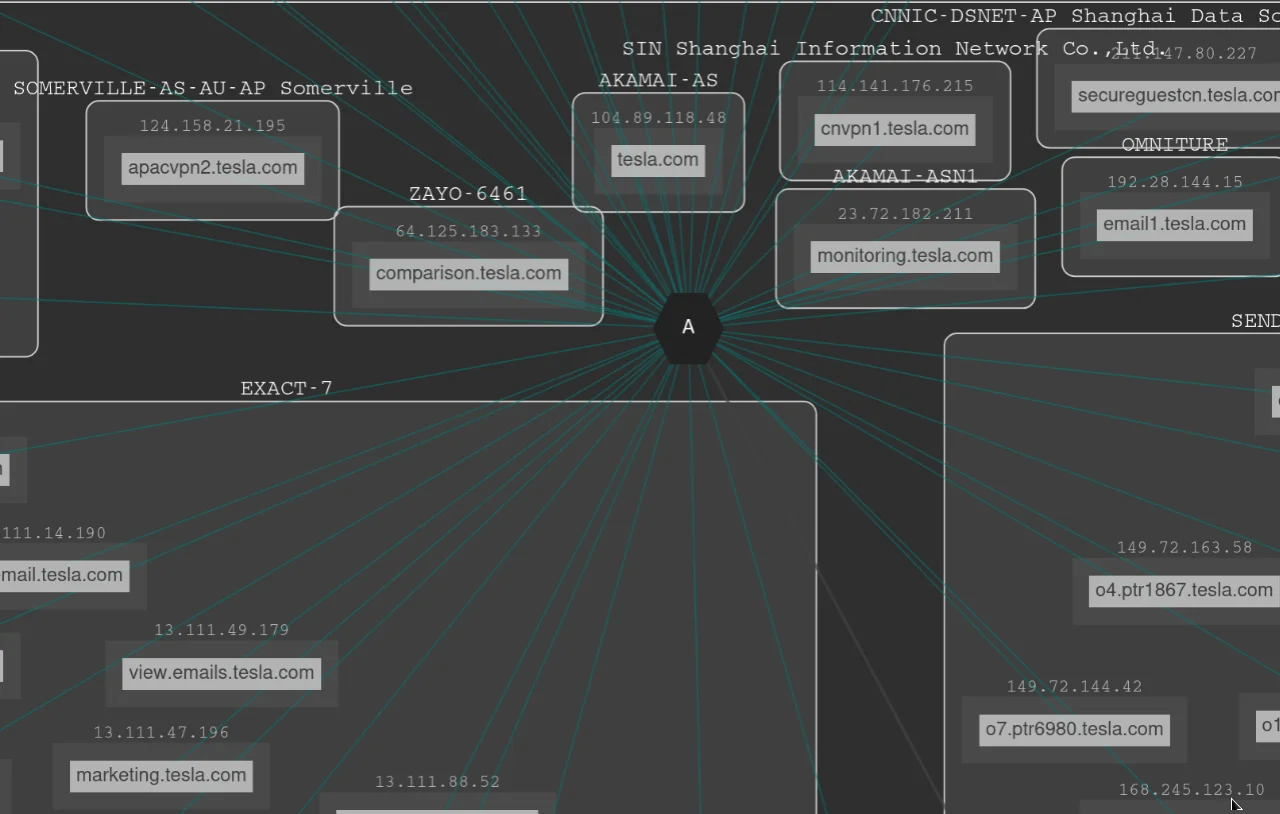
You can click on individual nodes in the graph to view more information about the corresponding subdomain, including its IP address, DNS record, and other details.
As you can see in the screenshots when I clicked on the node (click.emails.tesla.com) it shows me the IP address.
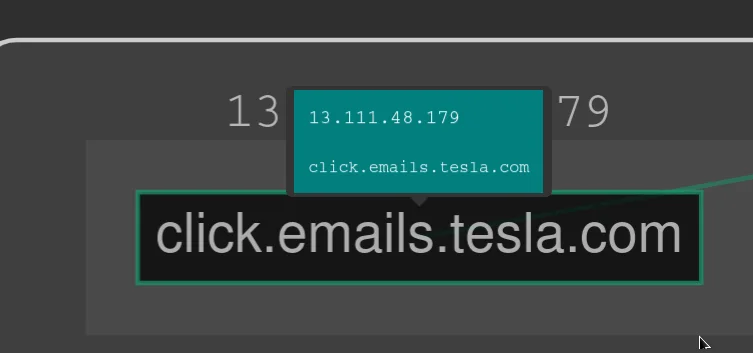
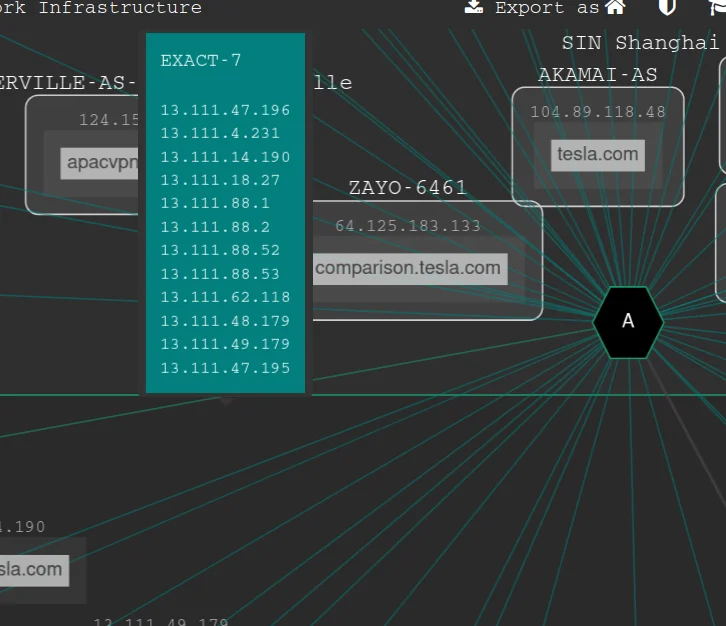
You can also use the search bar at the top of the mapping tool to search for specific subdomains or IP addresses.
If you want a report of your search then you can export the mapping data to a CSV file by clicking on the "Export" button at the top of the mapping tool. Shown same in the below screenshot.
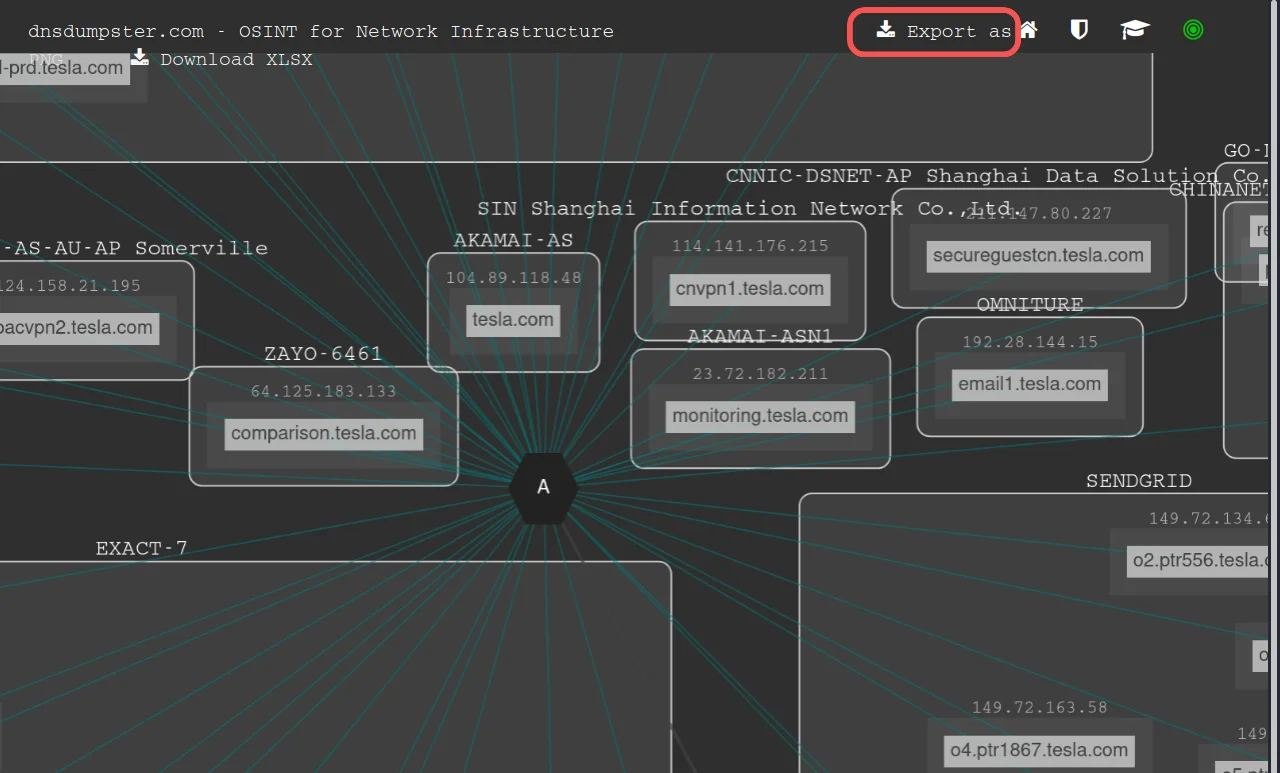
By using DNSdumpster, bug hunters can map out a target's network, including information about the target's DNS servers, mail servers, and other systems that are connected to the network.
Now I have shown you how you can use DNSdumpster, Let's see how I use it.
Practical Tips to use DNSdumpster Effectively
Below are my recommendations or tips that I experienced after using this tool in my bug-hunting journey.
- Research the target: Start your research by gathering information about the target domain and its subdomains to create a comprehensive list.
- Map the subdomains: Use DNS Dumpster's subdomain mapping tool to identify all the subdomains associated with the target domain.
- Use Reverse DNS Lookups: Reverse DNS lookups can help you identify IP addresses associated with subdomains, which can lead to further information and attack vectors.
- Utilize Tools: DNS Dumpster also provides tools for analyzing IP addresses, such as ping and traceroute, which can help you gather more information about the target.
- Monitor for Changes: Regularly monitor the target's subdomains for changes, such as new subdomains appearing or changes to IP addresses, as this can indicate new attack vectors.
- Check for open ports: Use tools such as Nmap to check for open ports on subdomains and IP addresses, as these may indicate potential vulnerabilities. Nmap is another tool that is used to scan the ports and vulnerabilities of the target, if you don't know what is Nmap and how to use it then you can check my blog on How to use the Nmap tool
Question: How do I hide a subdomain from dnsdumpster.com?
Ans: To hide a subdomain from being shown on dnsdumpster.com or similar tools, you need to prevent the subdomain from resolving to an IP address. Here are a few steps that you can take:
- Remove the A record: The A record is the DNS record that maps a domain or subdomain name to an IP address. If you remove the A record for the subdomain, it will no longer resolve to an IP address and will not be shown on dnsdumpster.com.
- Use a CNAME record: You can create a CNAME record for the subdomain that points to a non-existent domain name. This will cause the subdomain to resolve to an error page and not an IP address, making it less likely to be shown on dnsdumpster.com or other reconnaissance tools.
- Use DNSSEC: DNSSEC is a security extension to the DNS protocol that helps to prevent tampering with DNS records. By enabling DNSSEC on your domain, you can help to secure the DNS information for your subdomain, making it more difficult for reconnaissance tools like dnsdumpster.com to uncover.
It's important to note that while these steps can help to hide a subdomain from dnsdumpster.com, there is no guarantee that the subdomain will be completely hidden from all reconnaissance tools or that it will be completely secure from all forms of attack.
Netcraft
Netcraft is a powerful tool that provides a wealth of information about a target's website, network, and systems. For bug hunters, Netcraft can be an invaluable resource for conducting initial reconnaissance and gathering information about a target's environment.
Netcraft provides detailed information about the target's website, including the web server software, programming language, and operating system. This information can be used to identify potential attack surfaces and to determine the target's security posture. it also provides information about the target's hosting provider, including its name, location, and IP address. This information can be used to identify potential attack surfaces and to determine the target's security posture.
Netcraft can also provide information about the target's SSL certificate, including the certificate's expiration date and the certificate authority that issued it. This information can be used to detect SSL vulnerabilities, such as expired certificates or certificates that have been issued by untrusted authorities.
How to use Netcraft
I am not just going to share only how to use Netcraft but also share how bug hunters are using it to speed up the information-gathering part.
let's again try to get information on tesla.com
Identify the hosting provider and IP address
The first thing a bug hunter can do is to use Netcraft to identify the hosting provider and IP address of a website. This can be done by following these steps:
Step 1) Go to the Netcraft website and select "Site Report" from the top navigation menu. Refer to the exhibit.
Step 2) In the "URL or IP address" field, enter the website's URL. Let's use tesla.com for this example.
Step 3) Click on the "Search" button to generate the site report.
On the site report page, scroll down to the "Hosting History" section. This section will show the hosting provider and IP address of the website.
Like professional bug hunters, let's see an alternative and easy way to do it.
You can do the above steps by searching a single query on your web browser. Below you can see the query
To use a query string for this task, bug hunters can use the following URL:
https://sitereport.netcraft.com/?url=[WEBSITE_URL]
For example, to search for the hosting provider and IP address of Tesla, the query string would be:
https://sitereport.netcraft.com/?url=tesla.com
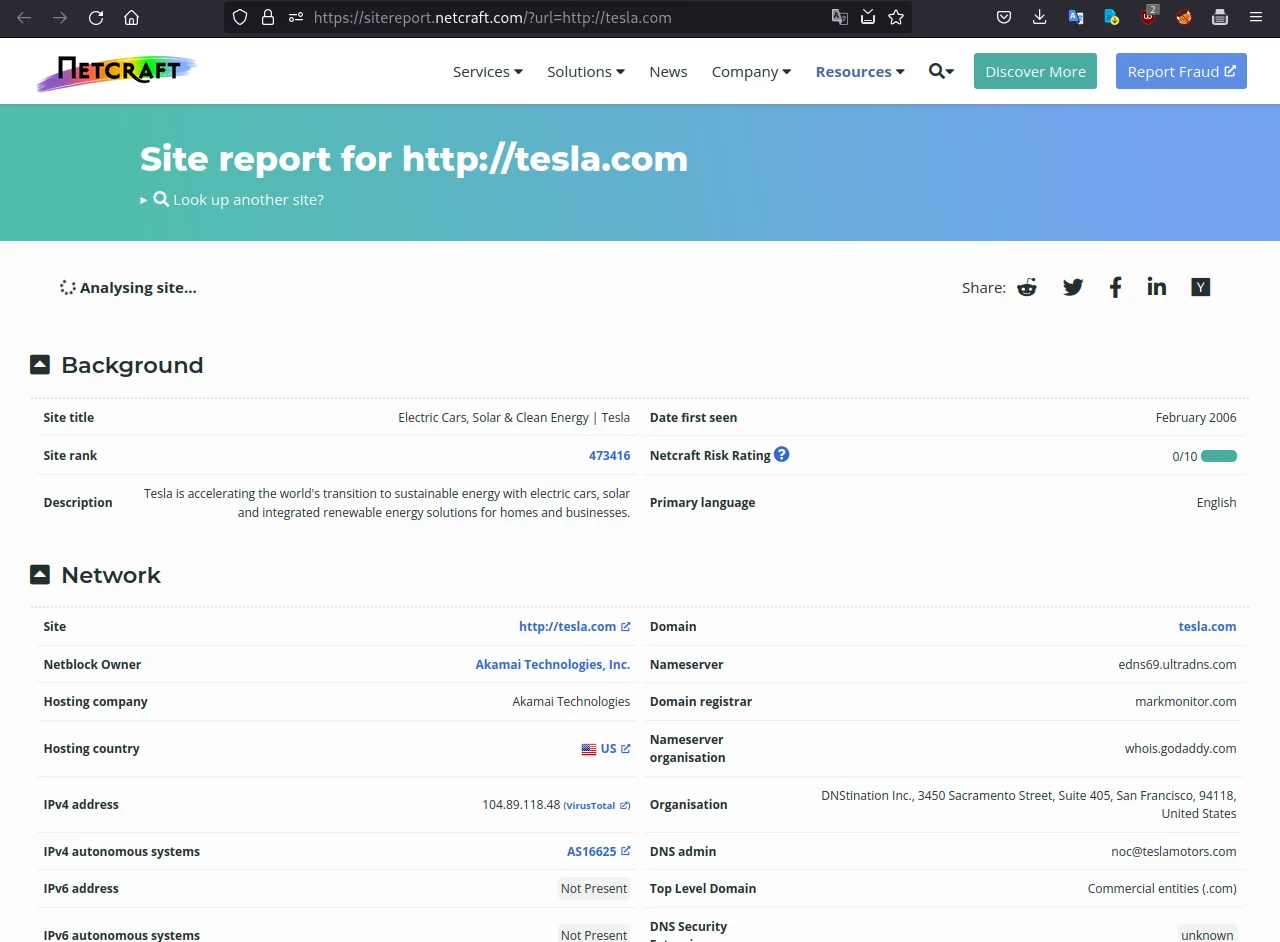
As you can see in the above screenshot, I have searched that query and gotten the results. This will provide information about the hosting provider and IP address of the website, along with additional details like domain history, SSL certificate information, and DNS data.
Look for old or unused subdomains
The second thing a bug hunter can do is use Netcraft to search for old or unused subdomains.
Note: Now I will only show you the direct queries that you can use to find results. You can also use the GUI pattern that I have shown in the above part.
To search for old or unused subdomains use the below query string.
https://searchdns.netcraft.com/?restriction=site+contains&host=[WEBSITE_URL]
For example, to search for subdomains of Tesla, the query string would be:
https://searchdns.netcraft.com/?restriction=site+contains&host=tesla.com
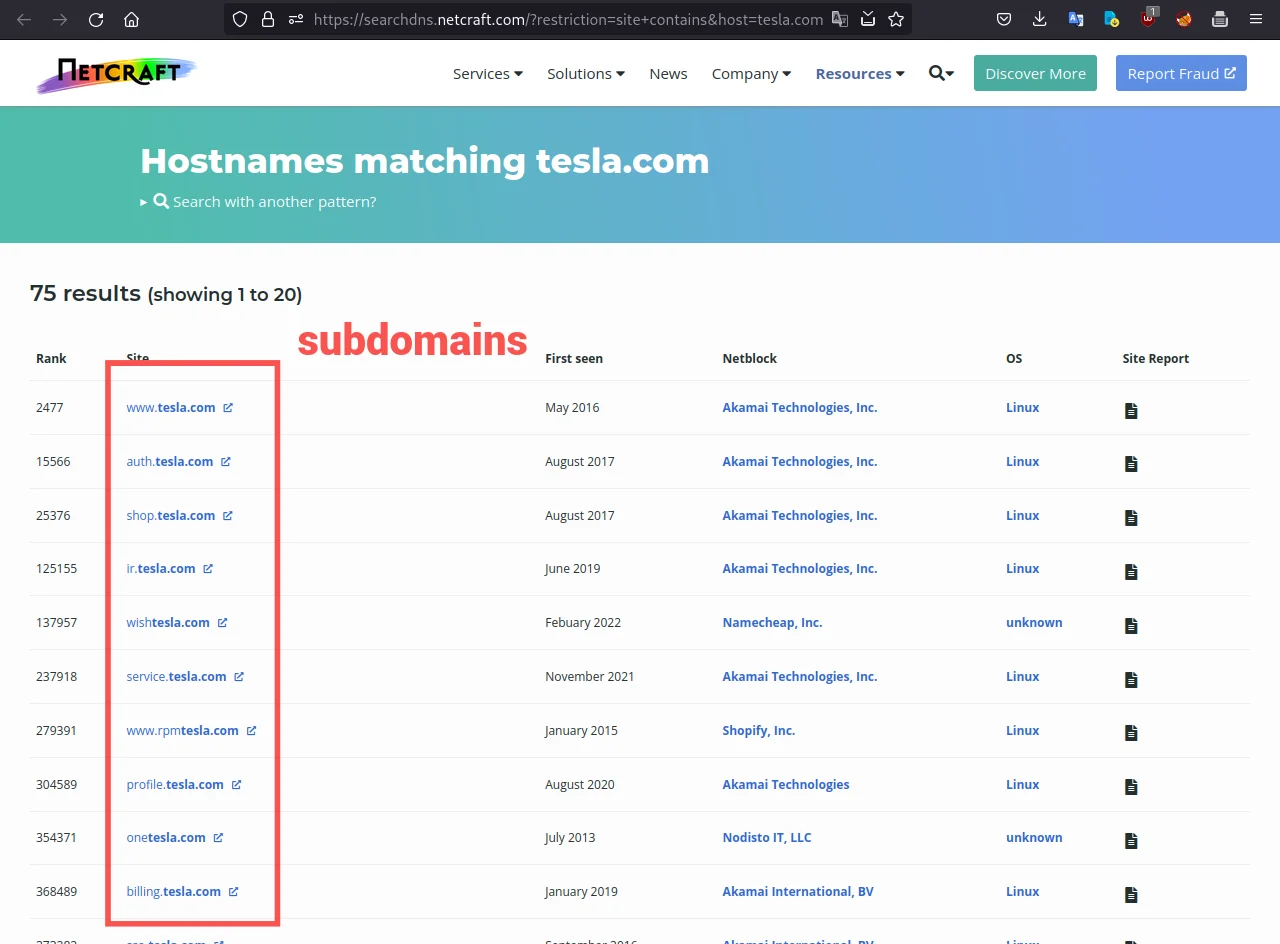
As you can see on the above snapshot it is providing a list of subdomains associated with the website, along with additional information about their IP addresses and web server technologies.
Query to enumarate all subdomains:
https://searchdns.netcraft.com/?host=*.tesla.comWhen you visit this URL, the Netcraft DNS search tool will display a list of all subdomains of the "tesla.com" domain that have been found in the Netcraft database. This can include both active and inactive subdomains, as well as subdomains that may no longer be in use. The results can be sorted by various criteria, such as the number of IP addresses associated with each subdomain or the date that each subdomain was last seen in the Netcraft database.
By using this query, bug bounty hunters and security professionals can quickly identify subdomains that are associated with a target domain, which can be useful for identifying potential attack vectors and vulnerabilities. Additionally, this information can be used to prioritize further reconnaissance activities, such as identifying web applications, email servers, or other systems that may be associated with specific subdomains.
Identify the web server technology
The third thing a bug hunter can do is to use Netcraft to identify the web server technology used by a website.
To use a query string for this task, bug hunters can use the following URL:
https://sitereport.netcraft.com/?url=[WEBSITE_URL]&tbl=server
For example, to search for the web server technology used by Tesla, the query string would be:
https://sitereport.netcraft.com/?url=tesla.com&tbl=server
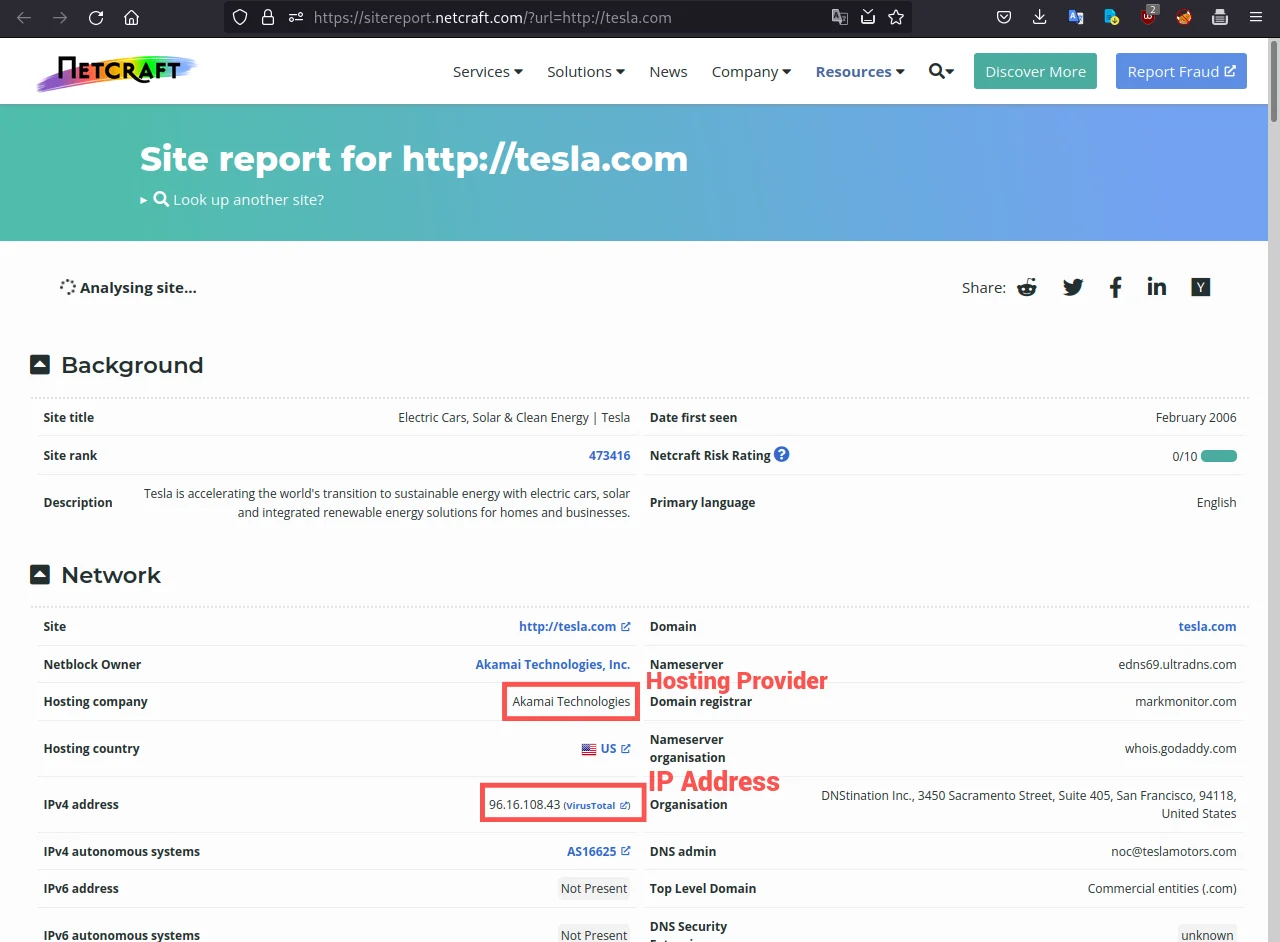
Now see the results on the above screenshot which is providing information about the web server technology used by the website, along with additional details like the operating system, scripting language, and server software.
Check for phishing sites
To check for phishing sites, bug hunters can use the following query string:
https://sitereport.netcraft.com/?url=[WEBSITE_URL]&tab=phishing
For example, to search for phishing sites associated with Tesla, the query string would be:
https://sitereport.netcraft.com/?url=tesla.com&tab=phishing
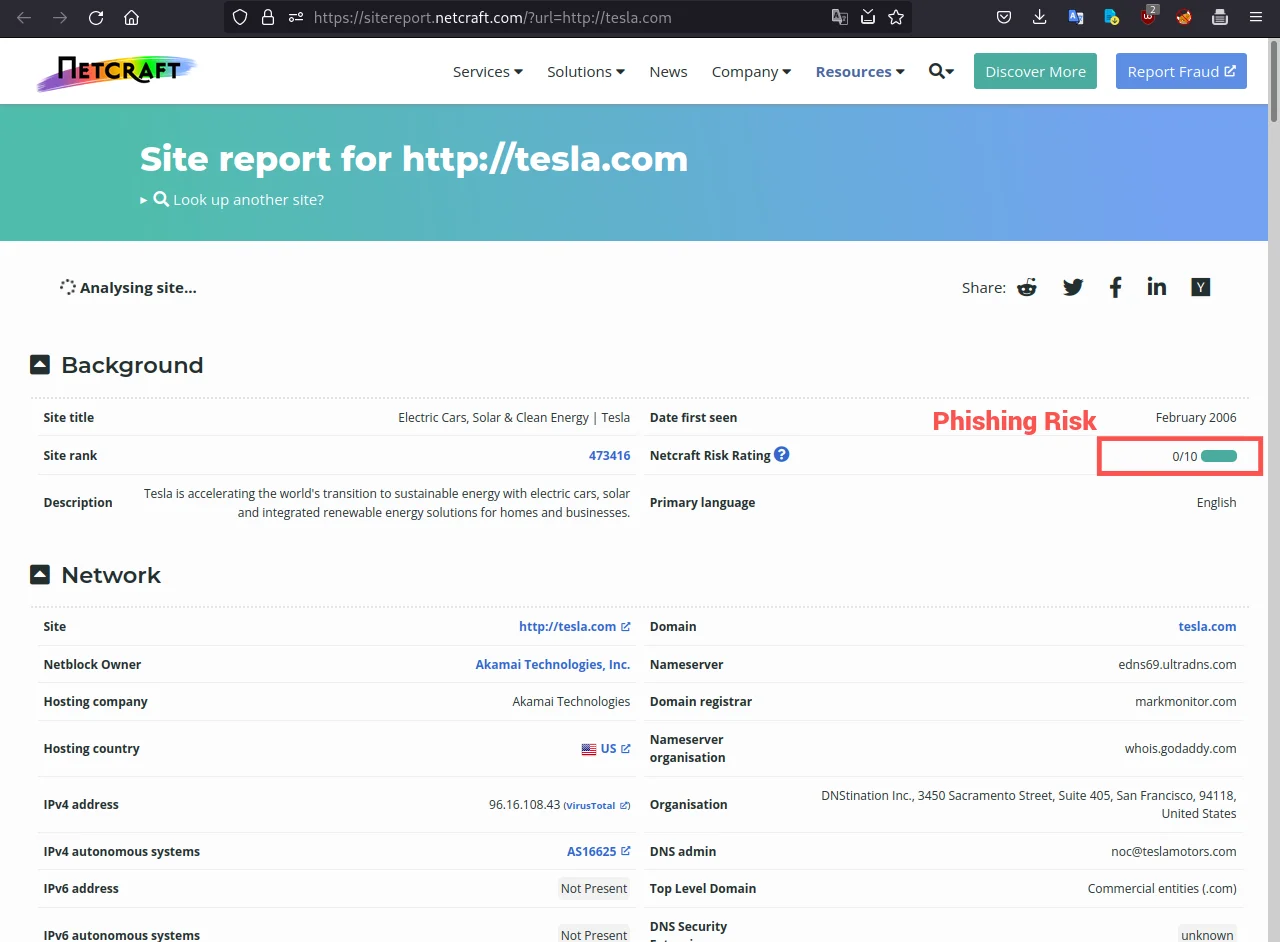
You can see on the above screenshot we found 0 phishing websites so basically, this query will provide information about any known phishing sites associated with the website, along with additional details like the hosting provider and IP address.
Find competitors
Sometimes you have to search for competitors of your target, or maybe for your own website. Netcraft will also be helpful in that situation.
Let's see how to research competitors. Use the below query.
https://www.netcraft.com/search/?q=neighbours:[WEBSITE_URL]
For example, to search for competitors of tesla.com, the query string will be:
https://www.netcraft.com/search/?q=neighbours:www.tesla.com
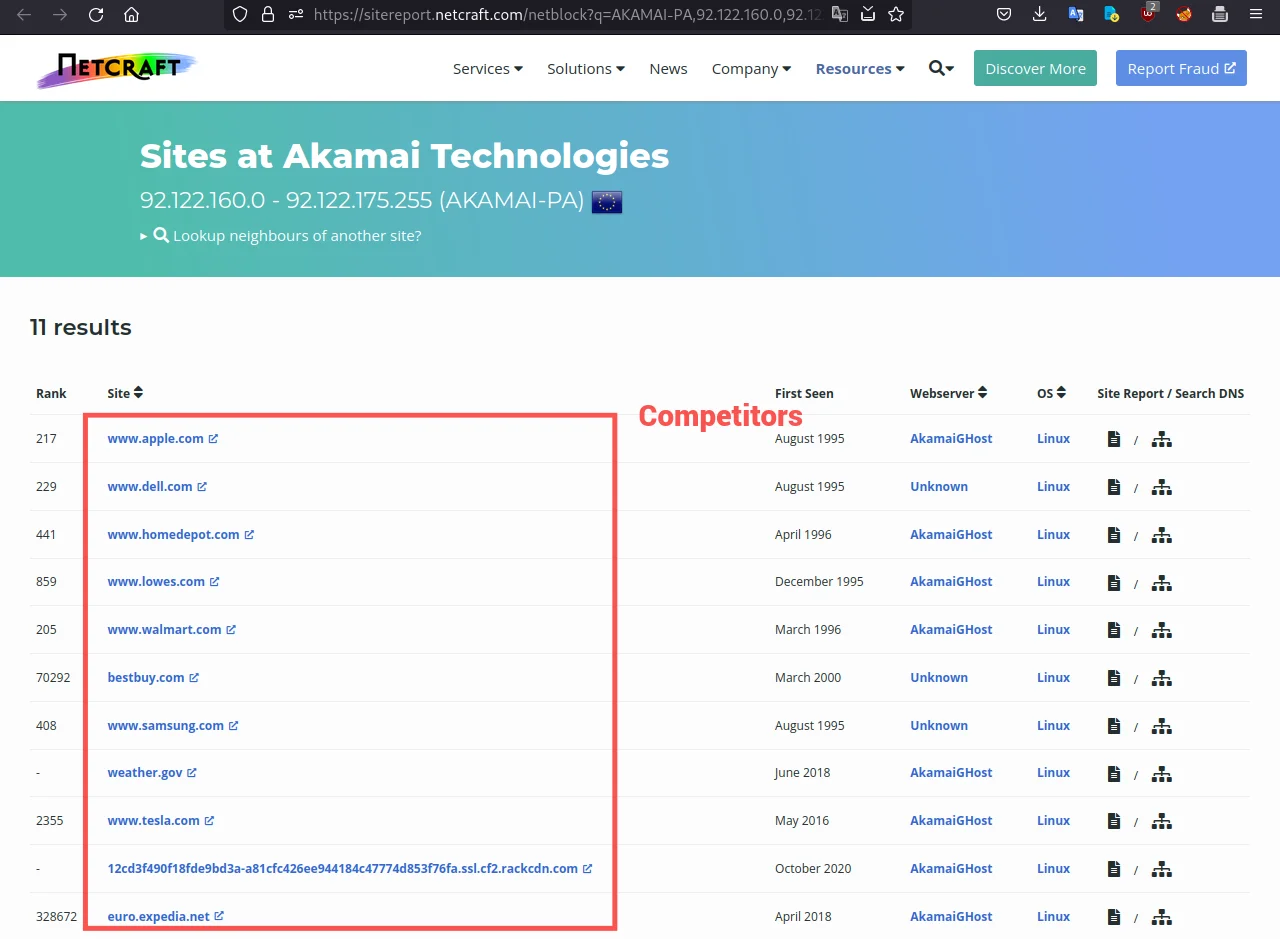
This will provide information about all competitors of the website, along with additional details like their webservers and OS.
Conclusion
In this blog, we explored two powerful OSINT tools, DNS Dumpster and Netcraft, that can help bug hunters discover valuable information about a target. We learned how DNS Dumpster can be used to search for DNS records and subdomains, while Netcraft can be used to identify the hosting provider, IP address, and web server technology used by a website. In the next blog, we will cover two more OSINT tools that can help bug hunters in their quest to find vulnerabilities and security flaws in systems. So, stay tuned for more tips and tools to help you in your bug bounty-hunting journey!
Commonly Asked Questions
Q1. Is OSINT a reconnaissance?
Ans. Yes, OSINT can be considered a form of reconnaissance, as it involves gathering information and intelligence about a target using publicly available sources. OSINT is often used in the early stages of reconnaissance, as it can help to identify potential attack vectors and vulnerabilities in a target's security posture. OSINT can provide valuable insights into a target's infrastructure, personnel, policies, and operations, which can be used to inform further reconnaissance activities or to plan targeted attacks.
Q2. What is the use of open source intelligence and passive reconnaissance?
Ans.By using OSINT and passive reconnaissance, attackers and security professionals can gather information about a target without raising any alarms or leaving any traces. This can make it easier to identify weaknesses in a target's security posture and to plan targeted attacks that are more likely to succeed. Overall, the use of OSINT and passive reconnaissance is a critical component of many security assessments, including bug bounty programs, penetration testing, and red teaming exercises.
Related Blogs
- What is OSINT? | OSINT Framework | Tools for OSINT | Best OSINT Techniques
- OSINT Framework | OSINT for Bug Hunters [Practical Demo] Part 1
- What is Smurf Attack? | What is the Denial of Service Attack? | Practical DDoS Attack Step-By-Step Guide
- What is Packet Sniffing? | How to Perform Packet Sniffing | Practical Demo on Wireshark
- How to Install Kali Linux Step-By-Step Guide
- How to Become an Ethical Hacker | Techofide