Hello Cyber Learners,
In this blog, we will learn about what is phone hacking, How to know if your phone is hacked or not what to do if your phone is hacked. We will learn about mobile device security and various tips and tricks.
I have also shared a practical video demonstration on how to hack a phone or how hackers are hacking your phone with spy apps and social engineering.
Note: This blog is just for educational purposes so we know how hackers are hacking phones and what security measures we should take to prevent such attacks.
- What is Phone Hacking?
- What is Mobile Device Security?
- How to Hack a Phone?
- How to know if your Phone is Hacked or not?
- What to do if someone hacks your phone
- Tips and Tricks For Mobile Device Security
- Practical Demo on Phone Hacking
- Conclusion
What is Phone Hacking?
Mobile hacking refers to the practice of manipulating or exploiting security vulnerabilities in mobile devices such as smartphones or tablets, with the intention of gaining unauthorized access to data or functionality. This can include a range of activities such as intercepting communication, stealing personal information, infecting devices with malware, and bypassing security measures put in place by app developers or device manufacturers. Mobile hacking can be performed for both legitimate purposes such as security testing and malicious purposes such as stealing personal information or performing other illegal activities.
What is Mobile Device Security?
Mobile Device Security refers to the measure taken to protect mobile devices, tablets, smartphones, etc to protect from theft, unauthorized access, data loss, data breach and damage. Mobile device security also breaks down into several parts: physical security, network security, and operating system security.
Physical Security:- Physical Security refers to protecting the device from physical theft, and damage.
Network Security:- Network Security refers to protecting devices from unsecured wifi/network connections such as open networks.
Operating System Security:- This security refers to protecting the mobile device, and tablets from malware attacks, RAT, and other security threats.
How to Hack a Phone?
After learning about what is phone hacking and what is mobile device security I will show you how to hack mobile devices so, let's get started
So I am using a spy application named Spy Phone. You can download that application by clicking on Spy Phone
Step 1: So the hacker will get access to the victim's phone by a trick so this application can be installed.
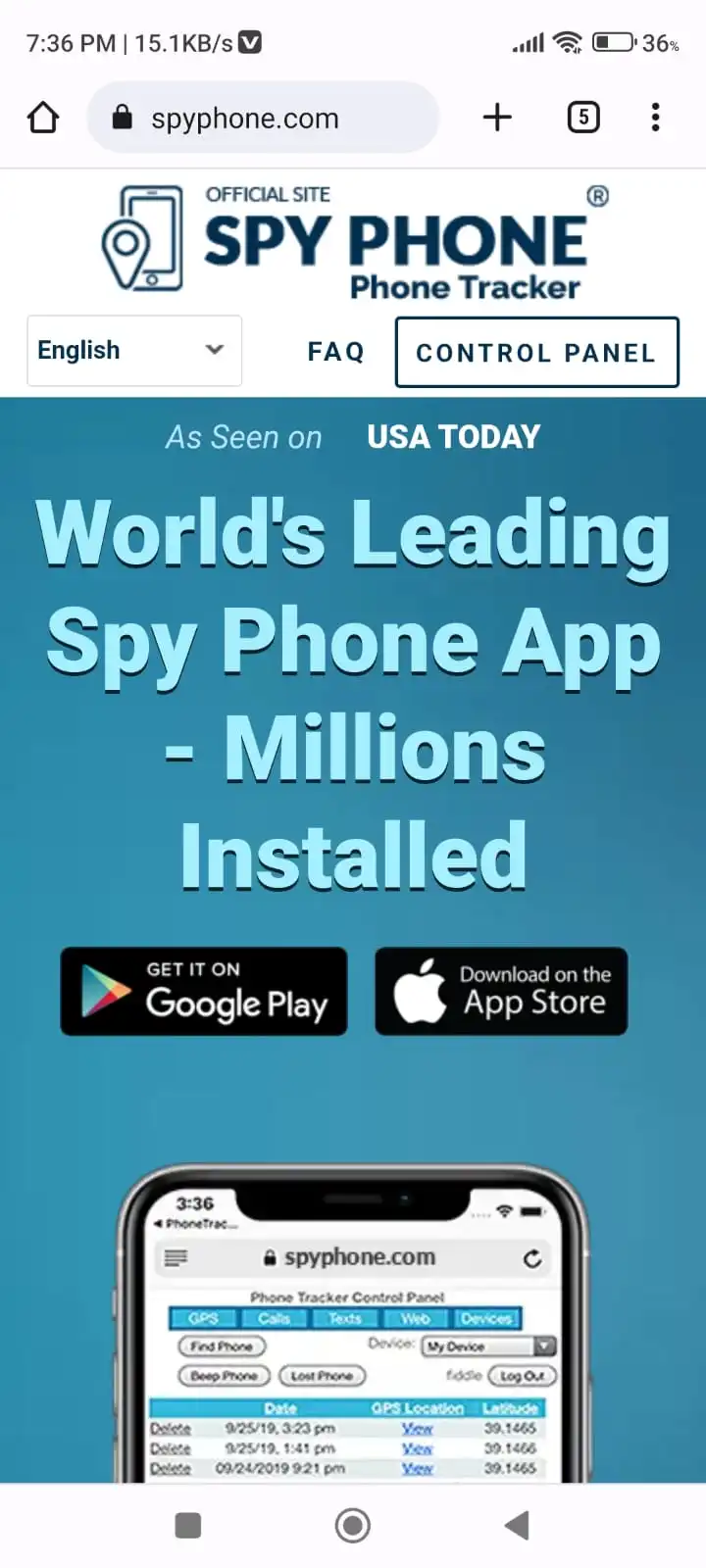
Step 2: Let's see how to get this app. So once you click the link you will reach the website where it will show apps for both Android and iOS so download according to your requirement You have to download the app on the victim's phone.
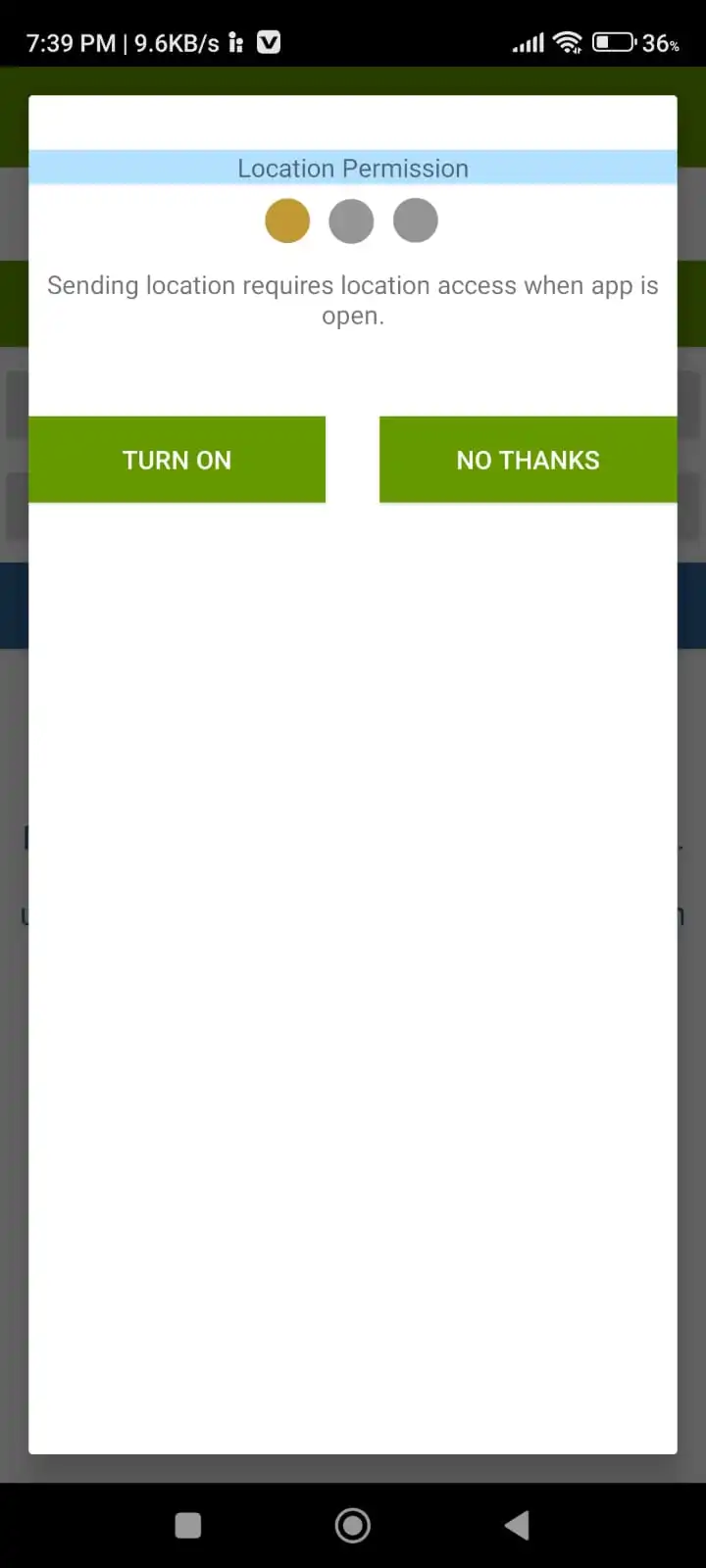
Step 3: After downloading, install the application and give all permissions to the app, you have to create an account also on that application. I have shown a screenshot below.
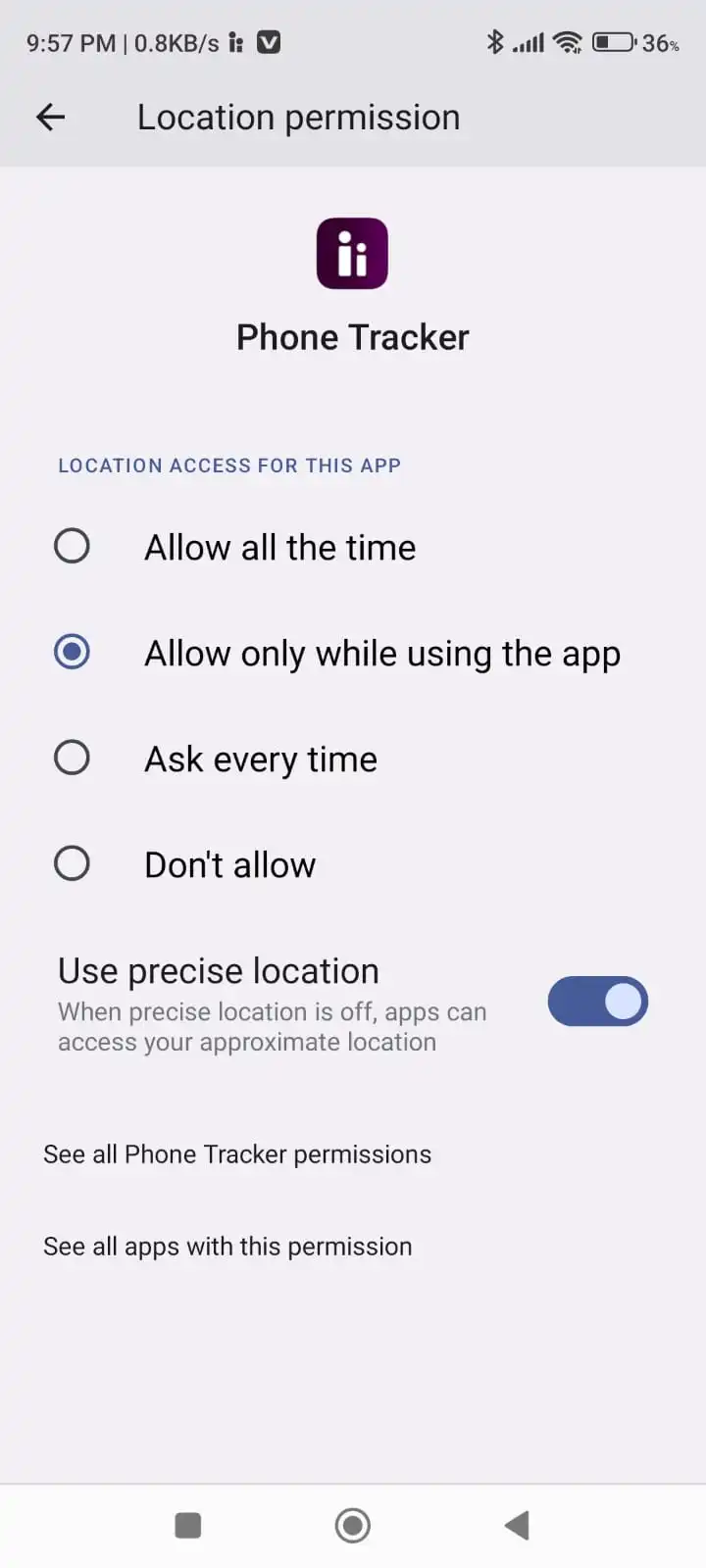
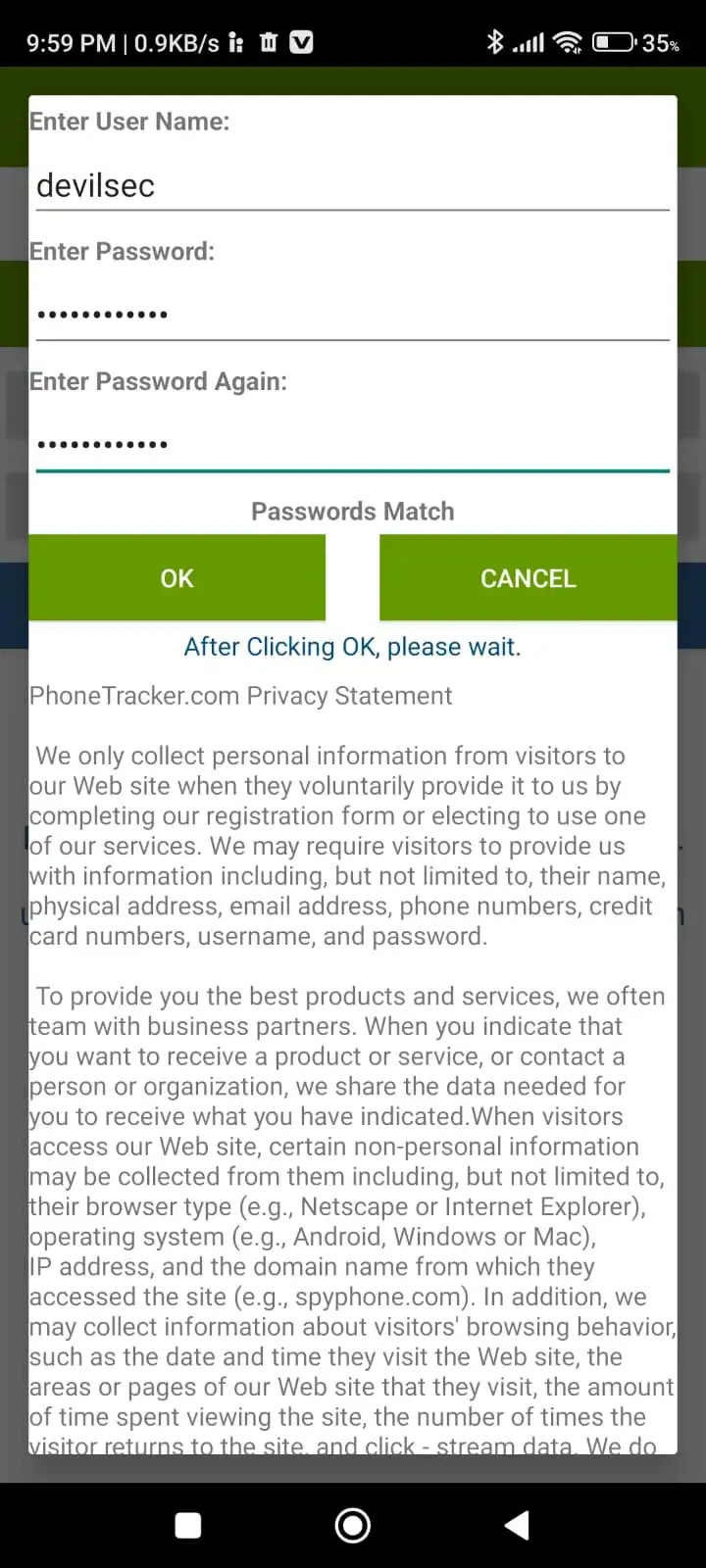
Step 4: Now all done, you can open the Spy Phone website from anywhere. Login to the website with the same credentials that you created during the installation of the app on the victim's phone.
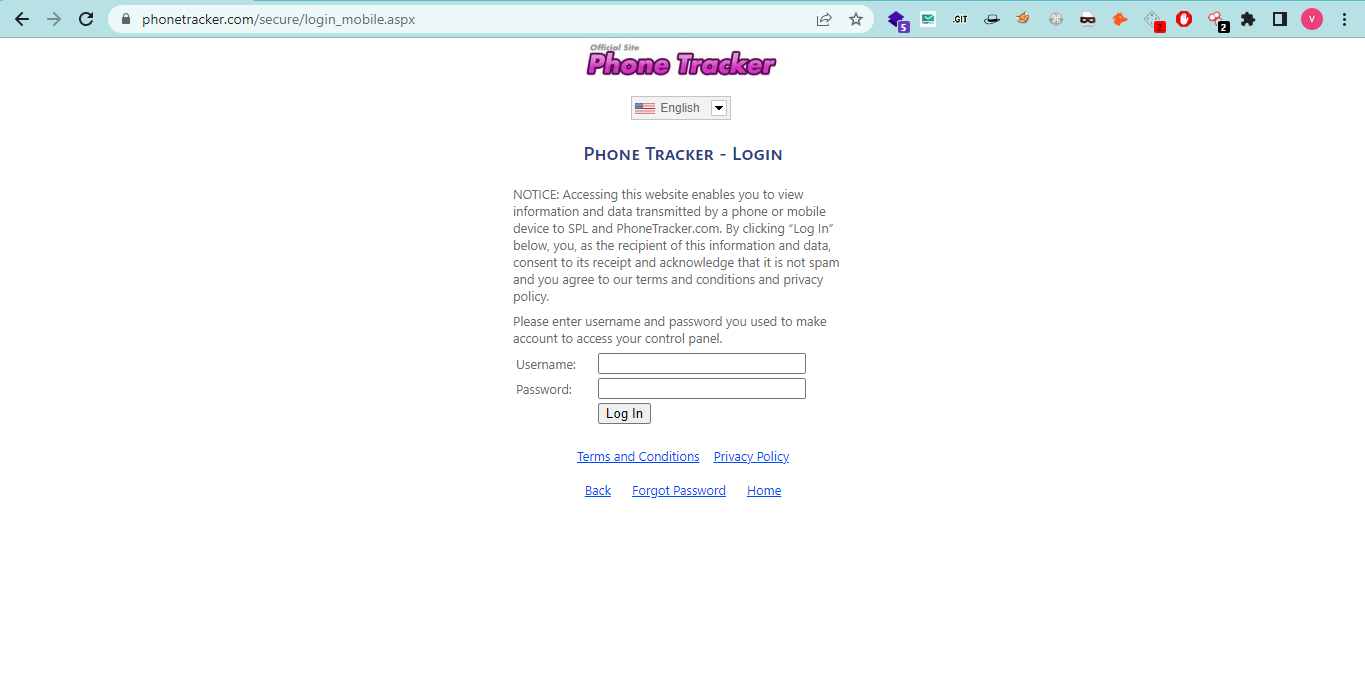
Step: 5: After login into your account you can see his/her GPS location, contact list and all the things that are present on the victim's phone.
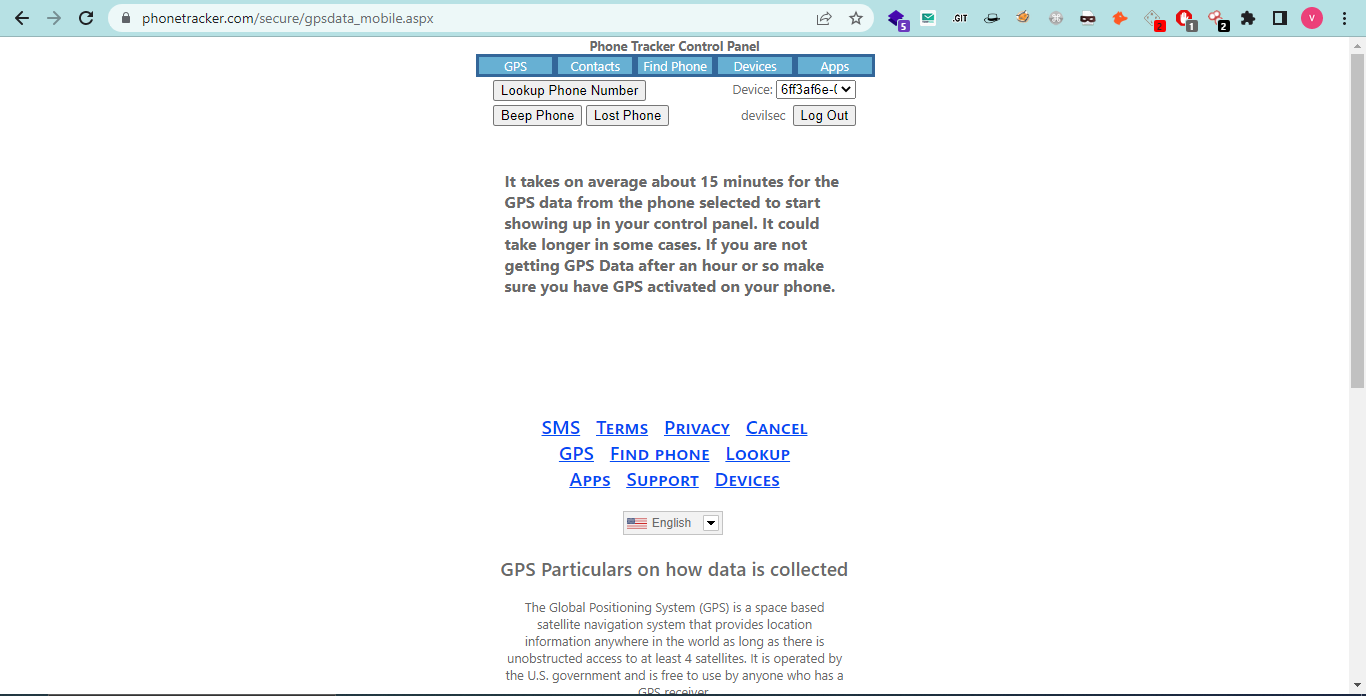
How to know If Your Phone is Hacked or Not?
Now let's check if your phone is hacked or not. Below I have mentioned a few signs or indicators that can help you identify if your phone is under attack.
Unusual Behaviour: If your phone is getting slow suddenly or often switching off or on automatically then it is a sign of unusual behaviour. It may also be a software issue, so let's identify what exactly it is.
Low storage on your phone can be the first reason you need to clean unwanted applications and files and try to reduce phone storage. Once done restart your phone and your phone now should be better.
You can also try to reset your phone but make sure you're backed up your data.
How did this happen: If you downloaded any app from any unknown website then there is a higher chance that the app was already infected by trojan or RAT. Unusual behaviour has happened when the attacker is controlling your device, but it is not necessary that if any unusual activity is happening that means your device is hacked, it may be due to software incompatibility or UI not responding as per the function defined.
Security Tip: Always try to install apps from the official website or Playstor/Appstore.
Battery Drain: If your mobile battery is suddenly getting drained for a few days then you might be under attack. Maybe your phone battery health is not good so let's identify what is the exact cause.
Hardware: Maybe our battery health is not good. If you want to check the battery hardware status you can download the Battery Monitor Application from the Play Store.
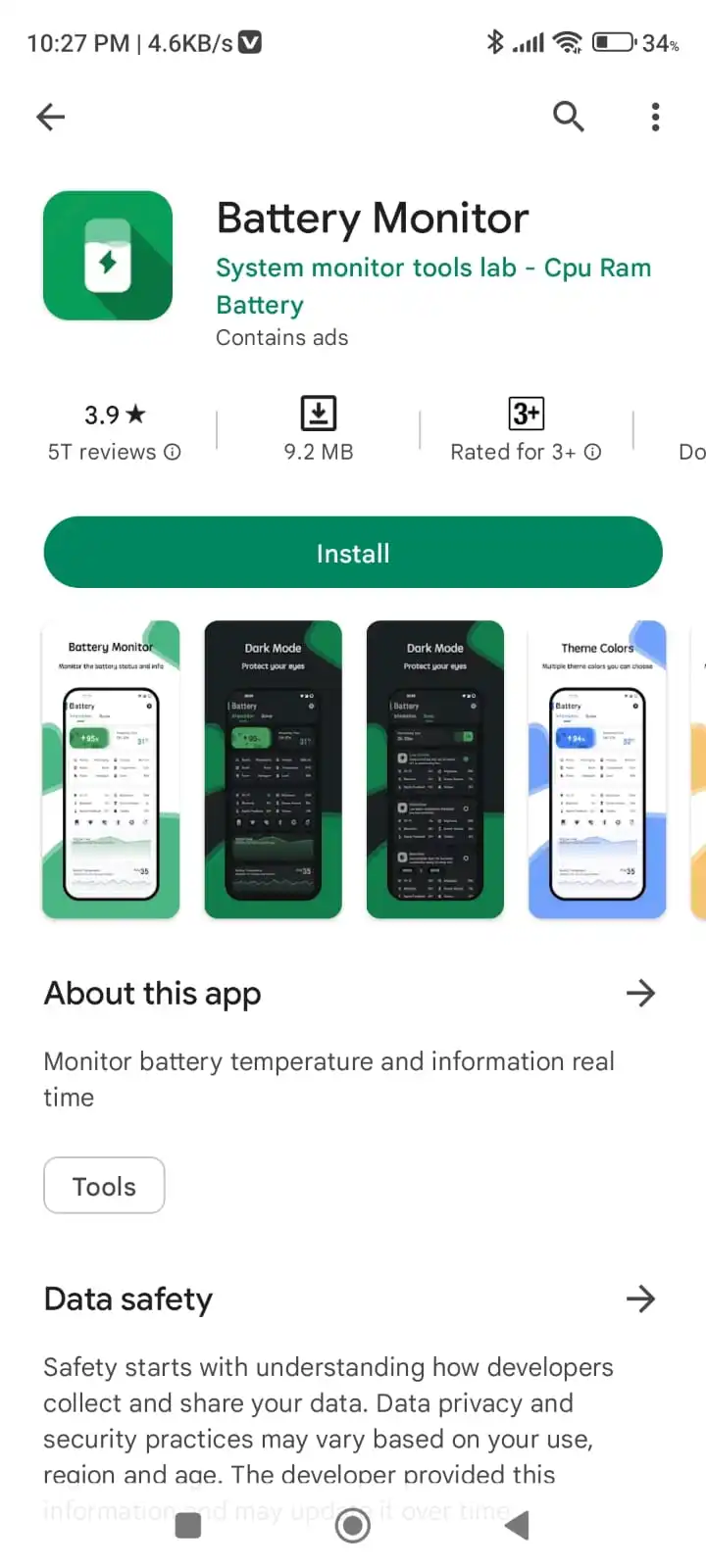
After downloading, open the application where you will see the battery status, in my case it is good but in your case, it may be different. If the battery status is not good then you have to change the battery. See the below screenshot for more reference.
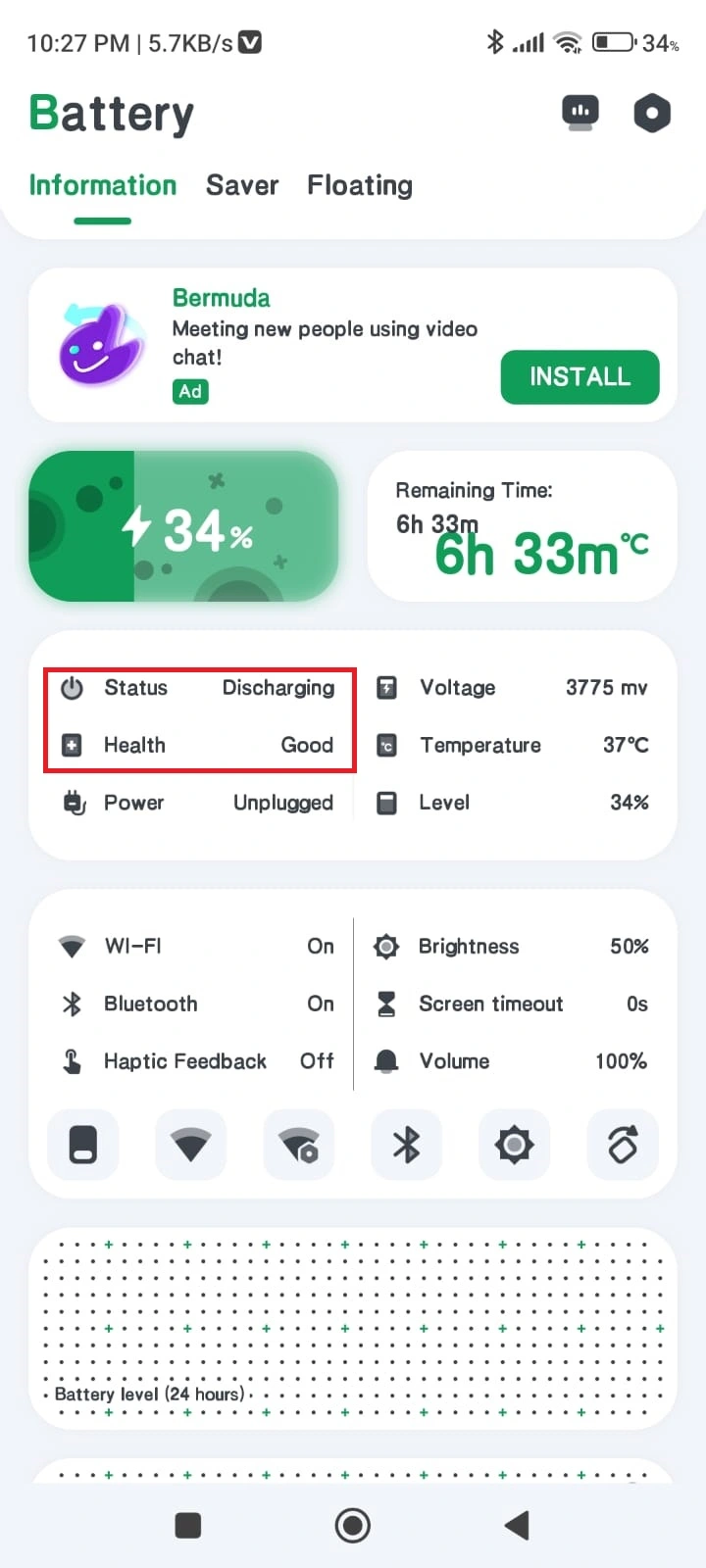
Software: If your battery health is showing good then it is the case where the unwanted application is consuming power. Let's see how to check.
Go to the Mobile Setting.
Search Battery usage then select the battery option
Now you can see which app uses how much battery. In my case, Instagram is using the maximum amount of battery.
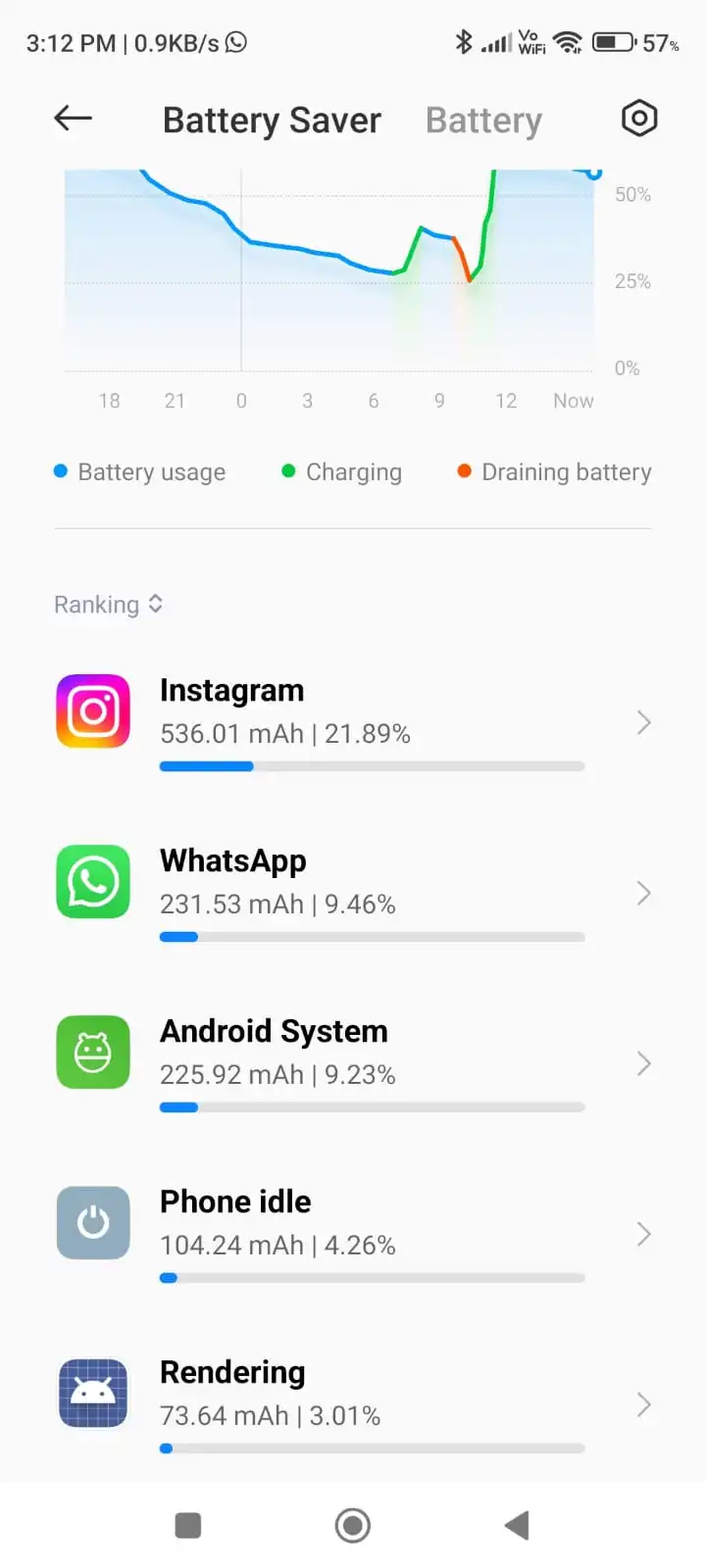
If you found any known application is using battery like in my case it is Instagram then it is your decision whether you want to stop using that application or reduce the usage. If you found any unknown application then you should just uninstall it because it is a sign of phone hacking.
How did this happen: You are using your phone a lot, maybe your phone battery health is not good, and maybe an unwanted application is consuming the battery.
Security Tip: Always keep checking on batter usage and uninstall unknown applications.
Pop-Ups: If you are getting strange pop-ups like "RAM is full or a new update is available for your phone" on your mobile screen there is a higher chance that your mobile is infected by adware malware. Maybe your phone has pre-installed bloatware apps let's analyze if is it really infected or not.
There are two main reasons for Pop-Ups first is bloatware application (the application which comes already installed when you purchased the phone) and the second is due to adware. First of all, you have to scan the phone with an inbuilt anti-virus scanner, in my case I will use my device's inbuilt anti-virus scanner for scanning.
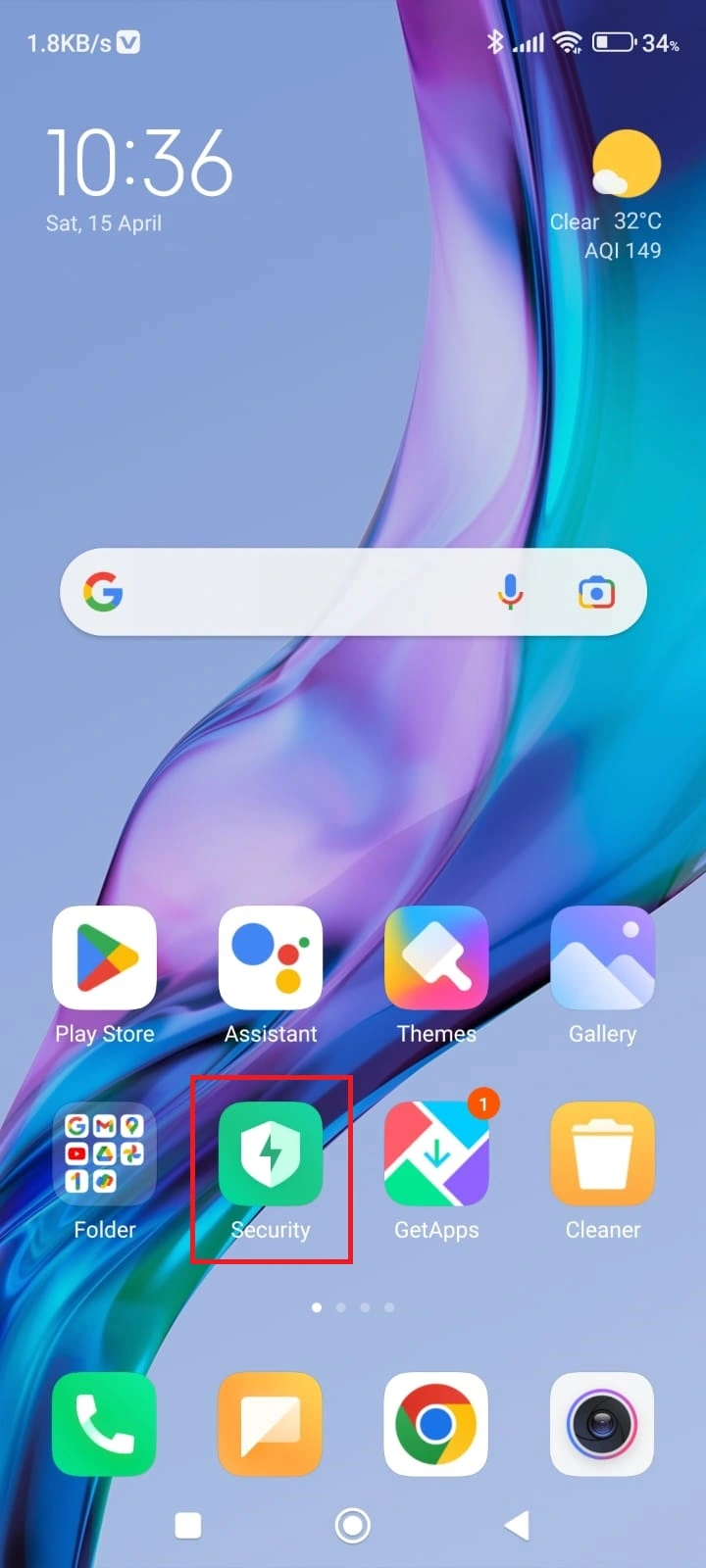
As you can see after scanning my device everything is good there is no adware.
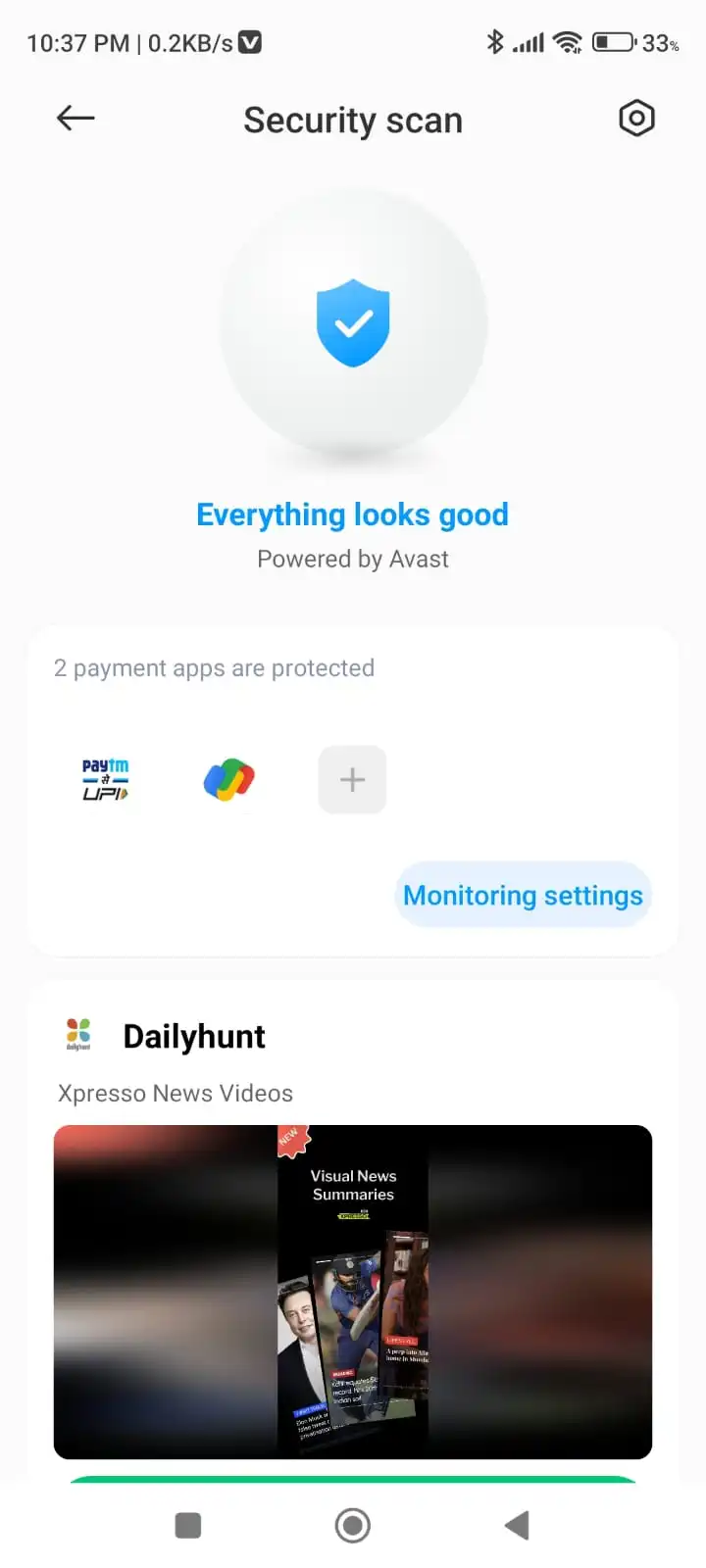
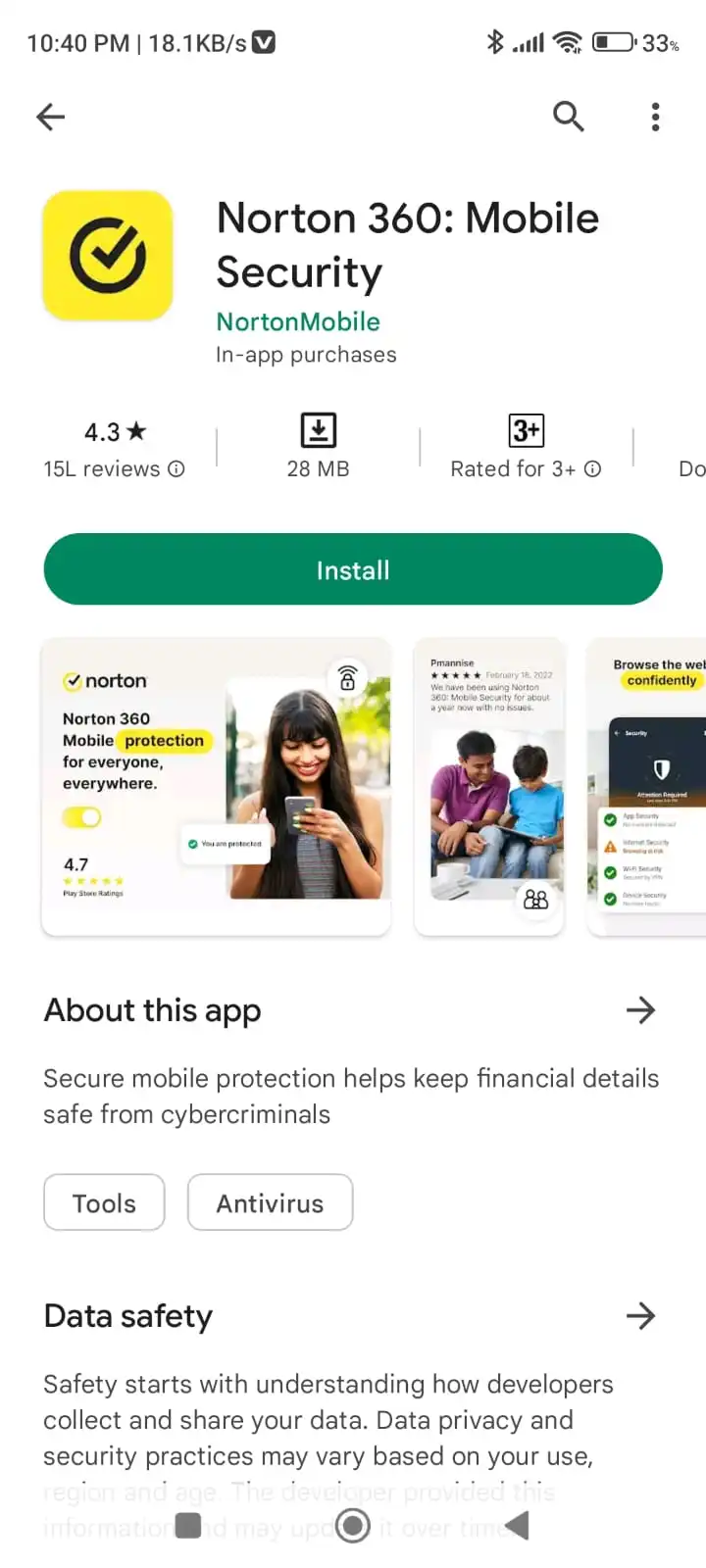
If your mobile device has no inbuilt anti-virus scanner then you can download Norton Security from Play Store/ App store
After scanning if still pop-ups occur it means that pop-ups are occurring due to a bloatware application.
pop-ups may occur due to bloatware apps ( those apps which are useless and pre-installed and you can't delete them). for example:- In Redmi Phone there is Mi Pay. You can force stop that application. Long press on that application > App info > Force Stop
How did this happen: This happen because of adware that you might be accidentally installed while downloading songs, games, files and pictures from your browser. It also may be because of bloatware applications.
Security Tip: Always download your stuff from official websites. Try to download applications only from Play Store/ App Store. Uninstall unwanted applications and force-stop the applications that you are not using.
Data Usage: If your data is getting finished very fast than your usual day then it is a sign of suspicious activity which means maybe some application on your device is using your data without your consent. Maybe applications are getting updated in the background and cloud backups are automatically initiated let's figure out what is the exact cause.
Let's check which application is consuming higher data. Go to the mobile device setting
Search data usage
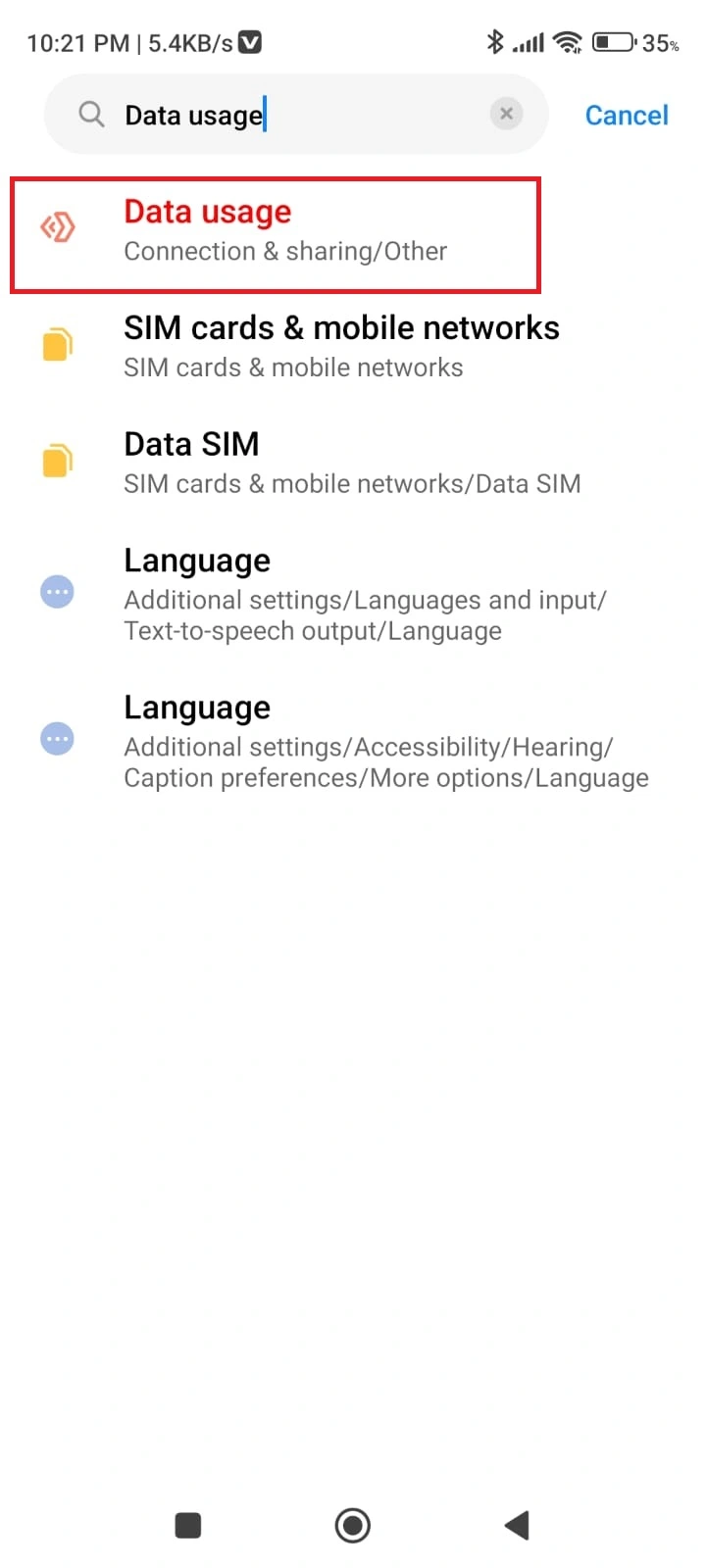
You can see in my case Instagram is using heavy data, in your case application may be different.

If the application is known by you then it is good, if it is used by the unknown application then uninstall the application from your mobile device.
How did this happen: This will happen if you download or upload anything, or maybe any unknown process which is running in the background and send all your data to the attacker.
Security Tip: Do not give unnecessary permission to any application. Always check unknown applications are deleted from your phone.
Unusual applications: Did you see some pictures in your gallery that you do not capture? Maybe you observed sometimes unusual notifications or any application that you are not using but are still on your phone. If you are ignoring such things then you are at higher risk. Maybe those applications are installed by someone else or pre-installed in your phone let' 's see what exactly it is.
Here are some steps where you can see all apps if it is hidden you can find them easily, Go to the settings > search apps > Choose installed apps > check which app is installed by you and which is not.
Security Tip: Maybe there is an unknown application but before deleting it you can once Google it to know what exactly that app does.
So, we have discussed the common signs. I have tried to cover all but there are some other signs as well. It is difficult to cover all so my recommendation is to always keep your phone clean every week and always observe your phone behaviour.
What to do if someone hacks your phone
If you suspect your phone is hacked, you must follow the steps below.
There might be different conditions or scenarios for every individual so follow according to your phone condition.
My phone is working properly: If you figure out that your phone is hacked but still you have access to your phone and everything is working properly then you can just install the spy app. If it's not getting uninstalled then just reset your phone.
My phone is locked: If your phone is hacked and your mobile device is locked and you are not able to unlock then you have to reset your mobile. So press and hold the power button for 10 seconds your phone will turn off, then press the volume down (-) and the power button together for 3 seconds and select wipe your phone or factory reset. If you are facing difficulty then just visit a nearby local mobile repair shop.
My phone is stuck or hang: If your mobile device is stuck or hang then first you have to turn off your phone, which you can do by holding the power button for 10 seconds. Sometimes device UI is not working properly and a heavy task is running in the background so restarting the phone can close those stuff and make your phone work. If it still hangs or is stuck in the boot hen visit the authorized service centre.
Some initial steps to safe your data and phone if it's hacked.
- First of all, just turn on your flight mode, and turn off your mobile data, it will immediately disconnect your phone from the internet and nothing will be accessed remotely by anyone. If any files were getting shared then it will also stop.
- After that you have to go to the phone history or battery management section, if there is an app it will show you how much battery that app use on the basis of usage you can identify which is the malware, and delete the particular app.
- Just clean your phone with your mobile antivirus.
- Keep your mobile backup ready because it needs any time.
- Do a Factory reset of your phone it will restore the phone to its previous and original state.
Tips and Tricks for Mobile Device Security
After learning about what is Phone hacking and how to know if your phone is hacked or not. There are several steps through which you can safe your device.
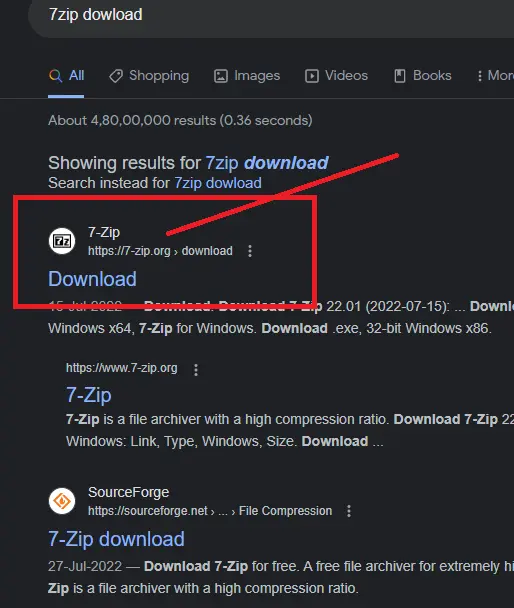
- Download files and applications from the official website. As you can see I am downloading the 7-Zip application from its own official website.
- Try to avoid clicking an unknown or short link. If you receive any short link in your mail or on WhatsApp don't click on the short link, because the short link may be malicious which is very dangerous for you. This is how short links look https://bit.ly/407tr5r
- Delete unnecessary files from your phone.
- Don't give your phone to anyone.
- Update your phone software because it will help you to be safe from mobile hacking at some point in time.
- Do not use open/public wifi it will lead to data breaches always use VPN when you are using public wifi.
- Do not save the password in your browser.
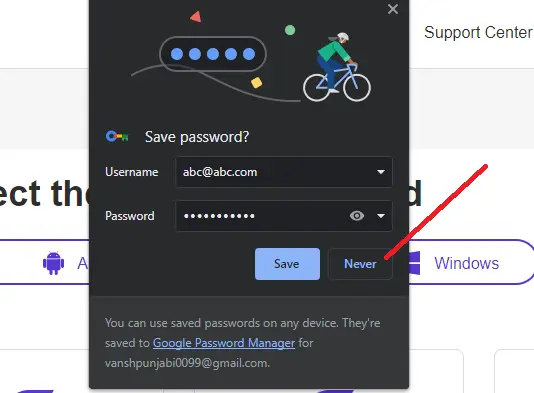
So, these are some simple and basic tips which will help you to secure yourself from hackers.
Practical Demo on Phone Hacking
In this video, I have demonstrated how hackers use their social engineering skills to hack someone's phone. This is just to tell you how hackers are performing this and what things you need to take care of for your mobile security.
We are not promoting any illegal activity, anything done by you is only accountable to you not to Techofide.
Conclusion
Phone hacking is a serious threat to our digital privacy and security. Hackers can gain access to personal and sensitive information stored on our devices. Prevention is key, and we should take necessary measures such as using strong passwords, avoiding public Wi-Fi, and keeping our devices up-to-date. However, despite our best efforts, we can never guarantee complete protection against phone hacking. Therefore, it is important to remain vigilant and practice safe digital habits to minimize the risk of falling victim to phone hacking attacks.
Also Read
- What is Packet Sniffing? | How to Perform Packet Sniffing | Practical Demo on Wireshark
- What is Digital Forensics | How to Use Digital Forensics Tools
- What is Digital Forensics | Practical Demo on Volatility
- What is Metasploit Framework | What is Penetration Testing | How to use Metasploit
- How to Install Metasploit on Windows and Linux | [Step by Step Guide]
- Advanced SQL Injection Attack (SQLi) | Blind SQL Injection And Prevention
- What is Burp Suite | How to use Burp Suite | Burp Suite Tutorial for Beginners
- Basics of Website Hacking | How The Internet Works? | Beginners Guide
- How to Install Kali Linux Step By Step Guide
- Linux Commands | Linux Commands Cheat Sheet