This blog will cover all basic concepts of computer network from scratch. Anyone who doesn't even know a single word about networking can easily understand this blog.
I have made this blog with practical demonstration and tried to provide the best visualizations in the form of gifs so it will be fun to understand concepts of computer network.
After reading this blog you will understand what is a computer network, how it designs, how it works and much more. I have also shown how the actual internet works with a practical example.
Note: The things I have shown you below is all my years of understanding and experience as I am a CISCO Certified Network Administrator and also qualified Huawei certification so I have tried to explain each and everything as it happens in the industries.
So let's get started to increase our eductauion.....
Computer Network Definition
Simple definition: A computer network is a group of connected computers (nodes) whose primary task is to share resources. Connected nodes can share resources such as Internet access, printers, file servers, and others.
What is a Computer Network?
Now after seeing the definition let's discuss in detail what exactly is a Computer Networks.
When networking device such as laptops, computers, access points, printers etc. are connected to share resources over the network then we can say that a computer network is established. There are various examples of the networks but the most common one is the Internet which connects billions of people all over the world
I want to show you one practical example so that it will be easy to understand how the network looks and connected.
The connection between the computer can be made through wiring, simply via the Ethernet cable. Connections can also be wireless; you'll hear the term Wi-Fi to describe the information that is sent over radio waves.
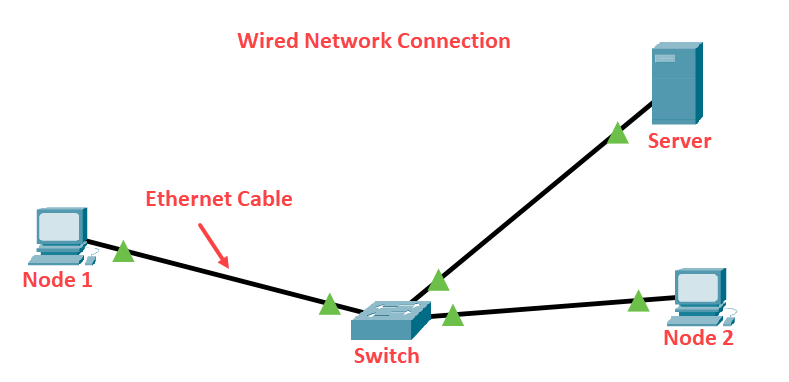
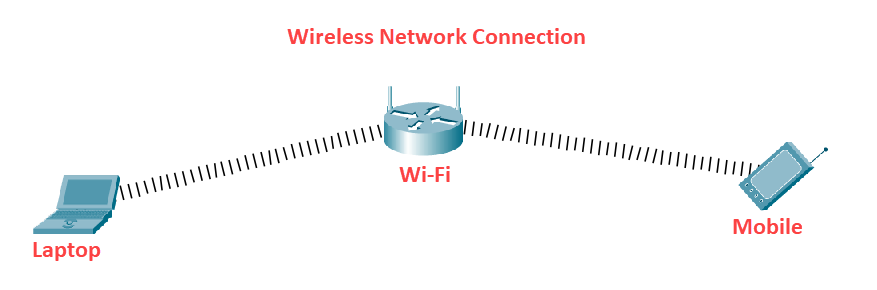
What Computer Networks Do?
The network is the most important thing. Do you ever think if the internet will go then what happens?
Internet is the network of networks i.e, a global network that connects every people all over the world. If you think sharing resources is the only work of a computer network then look at the below things that networks do.
- The biggest example nowadays is Work from home
- Communicating via email, video, instant messaging.
- Sharing device such as printers, scanners and photocopy machines.
- Sharing files such as video, images, documents etc...
- Taking remote connections
- Allowing network users to easily access and maintain information
- Mobile Networks Tower
- 5G, 4G technologies.
- Computer Labs in college, universities, enterprises, offices etc...
Important Terms and Concepts of Networking
Now we understand computer networks so let's see some basic key terminologies of networking before going to the depth of computer networks.
IP address
Internet Protocol i.e, IP address is a 32-bit value that associate with all devices which are connected to the internet. This value looks like 192.168.1.1 and it is also known as the Logical Address
Ip address is of two types public and private where versions are IPV4 and IPV6 where IPV4 also further divided into classes Claas A, B, C and D. IP address is a vast topic so we will discuss that in another blog in detail.
Subnet Mask
It is also a 32-bit value that is used to divide a single network into two or smaller sub-networks that helps to improve the security and reduces the size of the network by minimizing the unused IP's. The representation of the subnet is like 255.255.255.0
Gateway
It is simply a door between two networks that are using different protocols. It also works as a door to the internet from your device that enables your computer to work on the internet. For example, if the gateway is not set on your computer then you will not able to use the internet on that system.
MAC address
Media Access Control i.e, MAC address is a physical address that is assigned to every device hardware by the manufacturer. It is associated with the Network Interface Card (NIC). It is a unique hexadecimal 48-bit address used to identifies the host and looks like 00-2A-4G-J1-BD-CR
Port
A port is a medium through which data is sent and received. There are 65,535 ports number are available but not all are in use. The most commonly used ports are 20, 21 used for file transfer protocol (FTP) 22 used for secure shell (SSH) 80, 443 used for HTTP, HTTPS respectively.
Nodes
Node is a word that is used to define any network device like a computer or server that transmit packets over the network.
Network packets
Basically, it is just data that is transmitted over the network via nodes.
ISP
It is nothing but just an Internet Service Provider i.e, A networking agency that provides internet services and assigns IP addresses to a specific device.
DHCP
Dynamic host configuration protocol is used to assigns dynamic IP addresses to hosts and is handled by Internet Service Providers.
Computer Network Components
I have used the term "networking device" most of the time above, but do you know what are those networking device or components?
Let's see some mostly used networking components that are used to create a basic computer network.
NIC
NIC stands for the network interface card that is a hardware component used to connect a computer with another computer onto a network It can support a transfer rate of 10,100 to 1000 Mb/s.
These cards are of two types
- Wired NIC: This card is present inside the motherboard that uses cables and connectors to transmit data. For example PC's
- Wireless NIC: The NIC have an antenna to obtain the connection over the wireless networks. For example, laptops.
Hub
A Hub is a hardware device that connects multiple nodes with itself so that communication can happen. So it's working is simple when computer requests data from a network, it first sends the request to the Hub and then Hub broadcast that request to the whole network. Now all device that are connected to Hub will check whether the request belongs to them or not. If not, the request will be discarded

But nowadays, the hub is not used because of its unavailability of storage memory and privacy issue, as we see the working of the hub and understand whenever you send any data to the network it will reach every computer that is connected to the hub and that is the reason it is not used now, also it is replaced by more advanced computer network device like Switches, Routers.
Switch
The purpose of the switch is also the same as the hub but its working is different and it also solved the problem that faced in hubs.
The switch has a memory that helps it to memorize and decides where the data will be transmitted and where not. It delivers the data to the right destination based on the physical address present in the incoming data. It does not broadcast the data to the whole network like the Hub. It is capable to identify the device to whom the data is to be transmitted.

Router
The router is a device that is used to connect different networks so that communication can happen. As names, it gives the routes to the packets based on information that is available on the routing table of the router. It defines the best and shortest path from the available paths for the transmission of the packet.
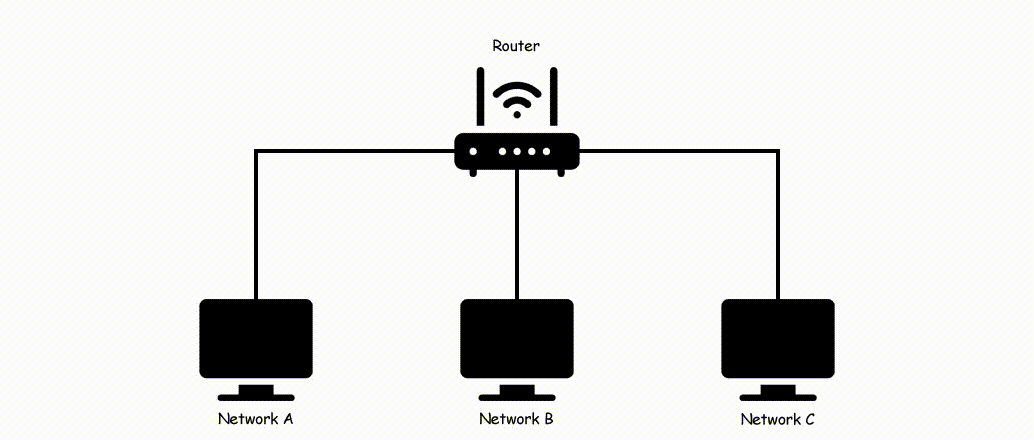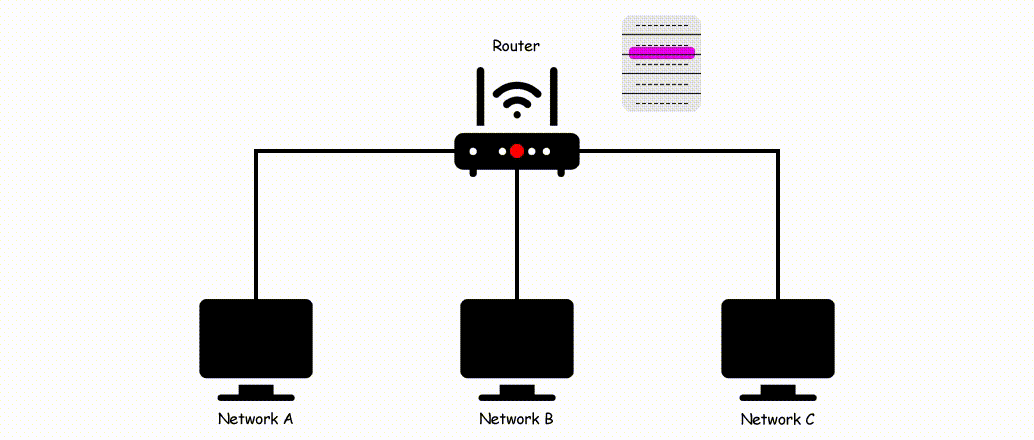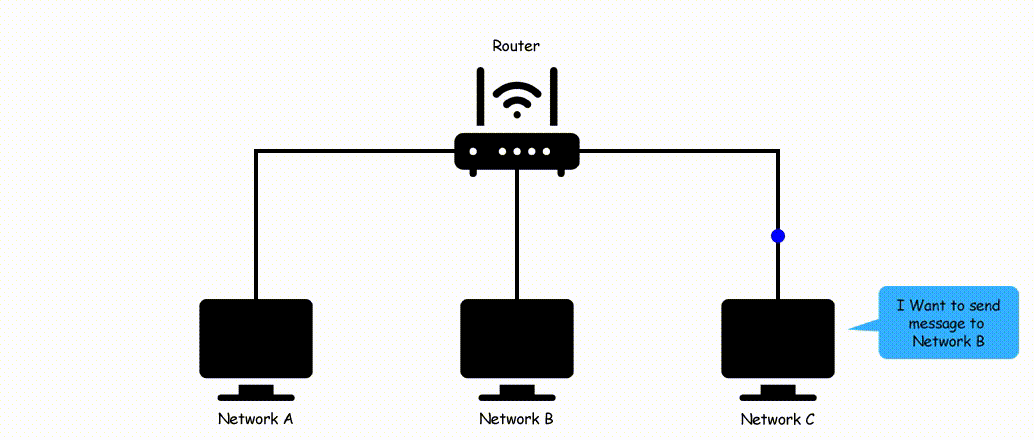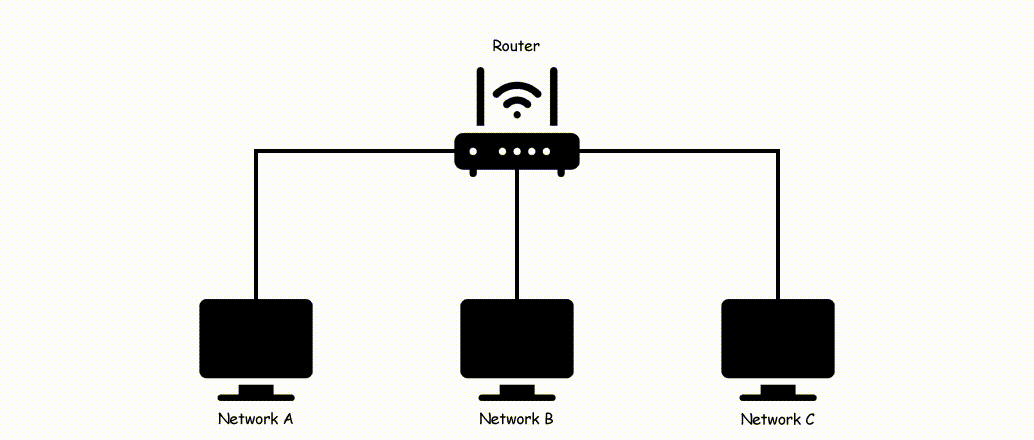
Now if you are new and don't have the knowledge like what is the same network and what is different so take a look at the below image.
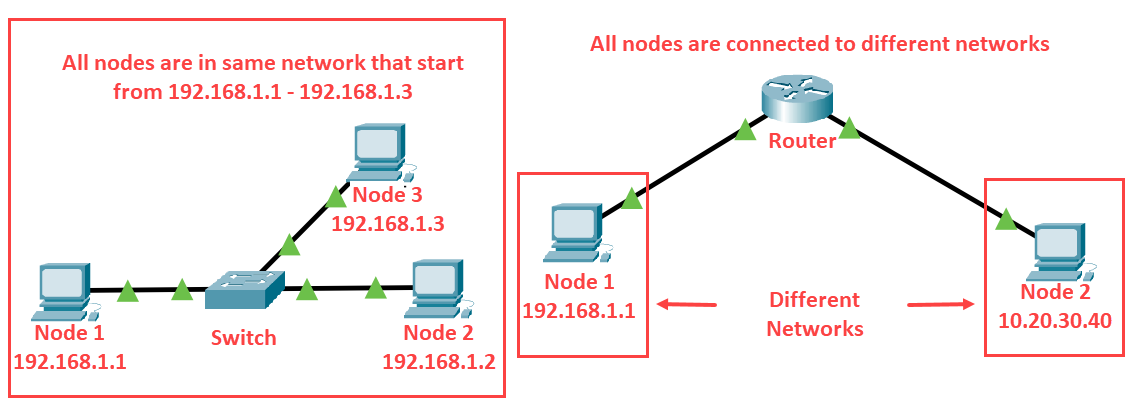
Note: Switch and Hubs only used to connect nodes in the same network where the router is used to connect different networks.
Modem
The modem is a very common networking device that is available in almost every house. Yes, it is your wifi box that is used to connect your device with the internet over the existing telephone line. It converts the digital data into an analog signal over the telephone lines.

Server
In simple words, it is a highly configured powerful machine that responds to the requests of the clients. Let's understand it with an example;
So you searched for google.com on browser and you just reach to that website. Do you how many things happen at that time in milliseconds? Let me tell you in the networking language.
- Now when you (client) searched for google.com it means you are sending the request to google's server.
- When your request reaches google's server it analyzes your request and sends you back your demanded resource as a server response.
- Now your system receive the response from the server and shows you the demanded content.
So this is how client-server architecture works and process your request. Check out the below animation for reference.
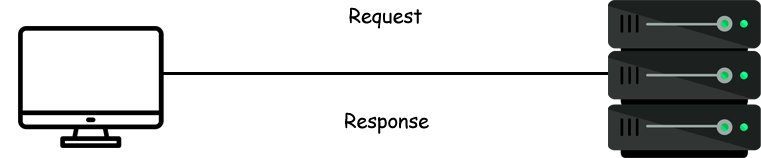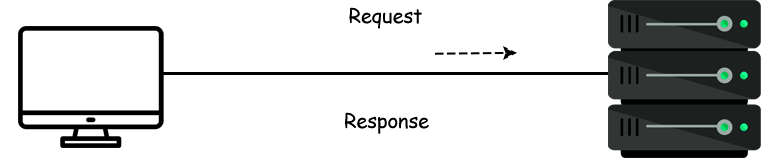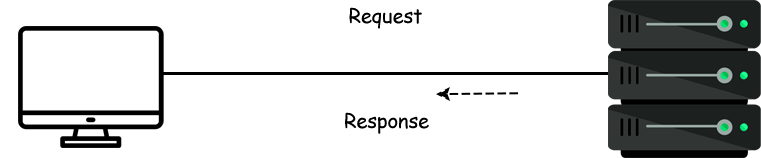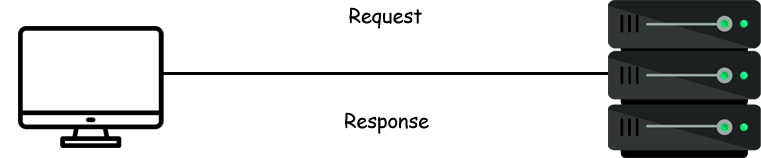
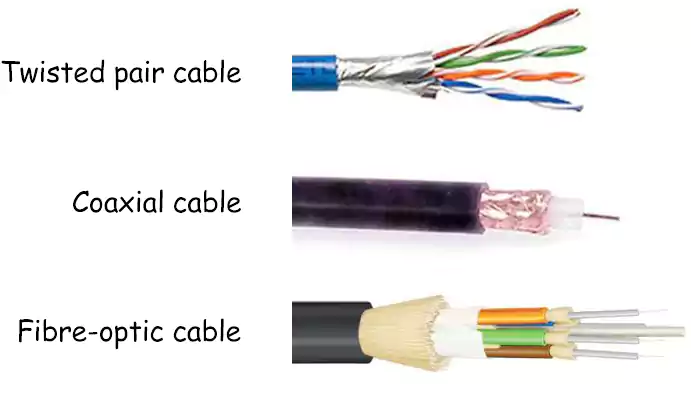
Cables
It is simply used to connect networking device to transmit signal. Cables and connectors both are equally used to connect devices to develop different topologies of networks.
There are three types of cables used in transmission:
- Twisted pair cable
- Coaxial cable
- Fibre-optic cable
How does a Computer Network Works?
So if I just tell you simply how it works then it will look like that "Computer networks connect nodes like computers, routers, and switches using cables, fibre optics, or wireless signals. These connections allow devices in a network to communicate and share information and resources" But do you not think it is a bit difficult to understand?
Let's understand the working of the computer networks with a practical example.
Here we will understand the working of computer networks with the help of the working of the Internet.
Do you know how the internet works? How does traffic move? What happening in the backend? Let's see and understand how things are actually working.
Check out the below image side by side for reference to understand the working of the Internet.
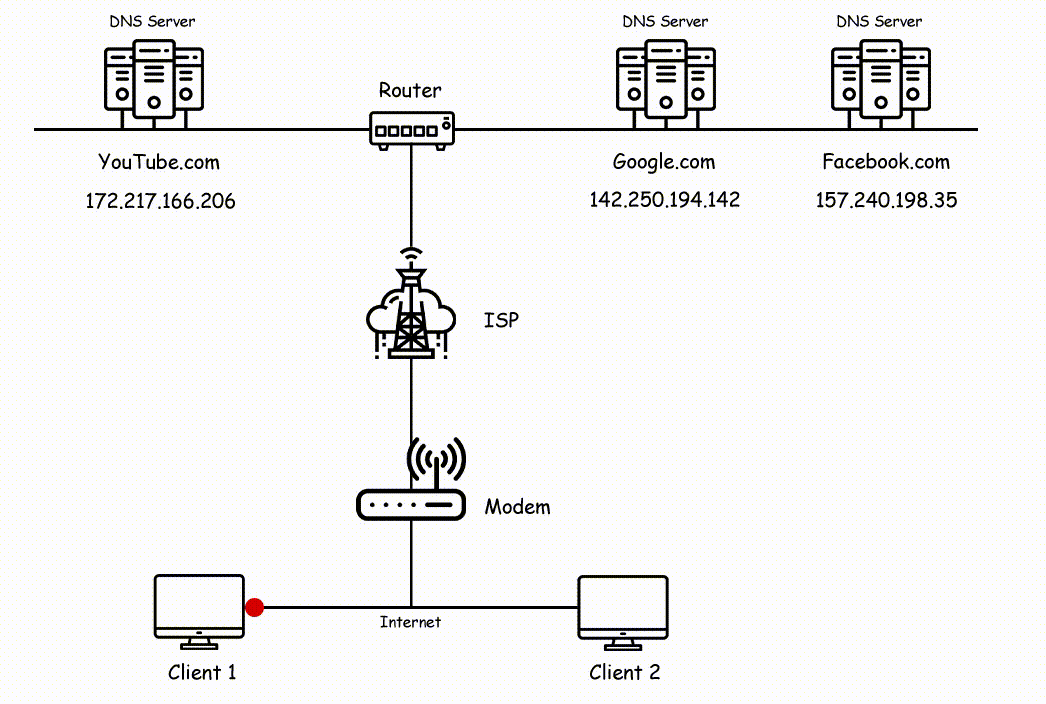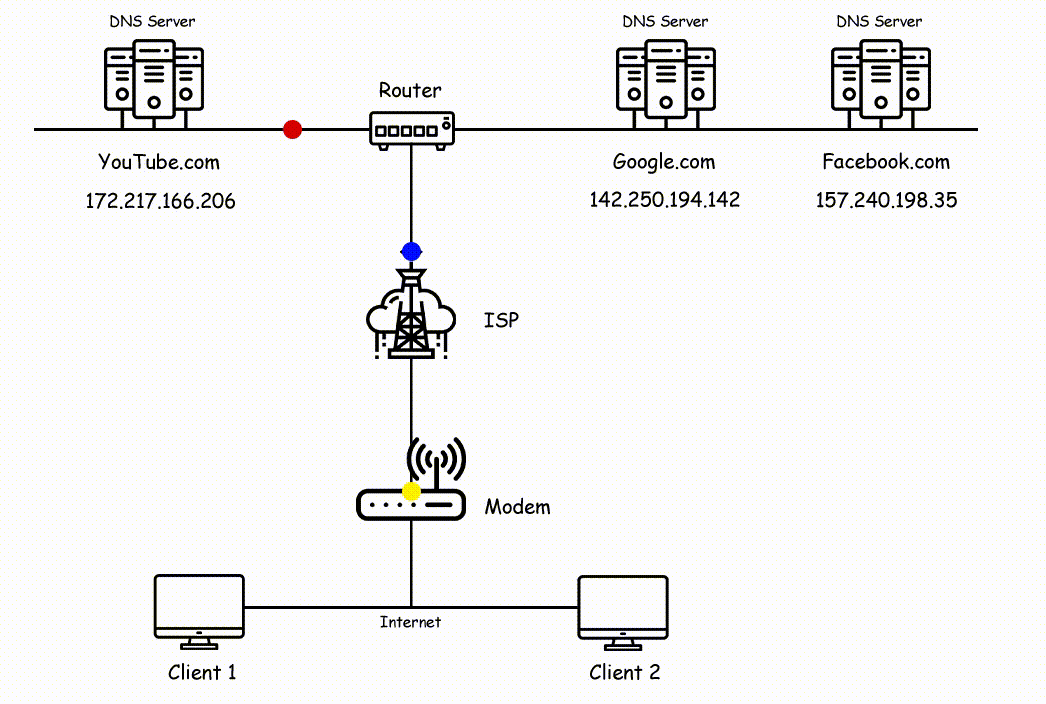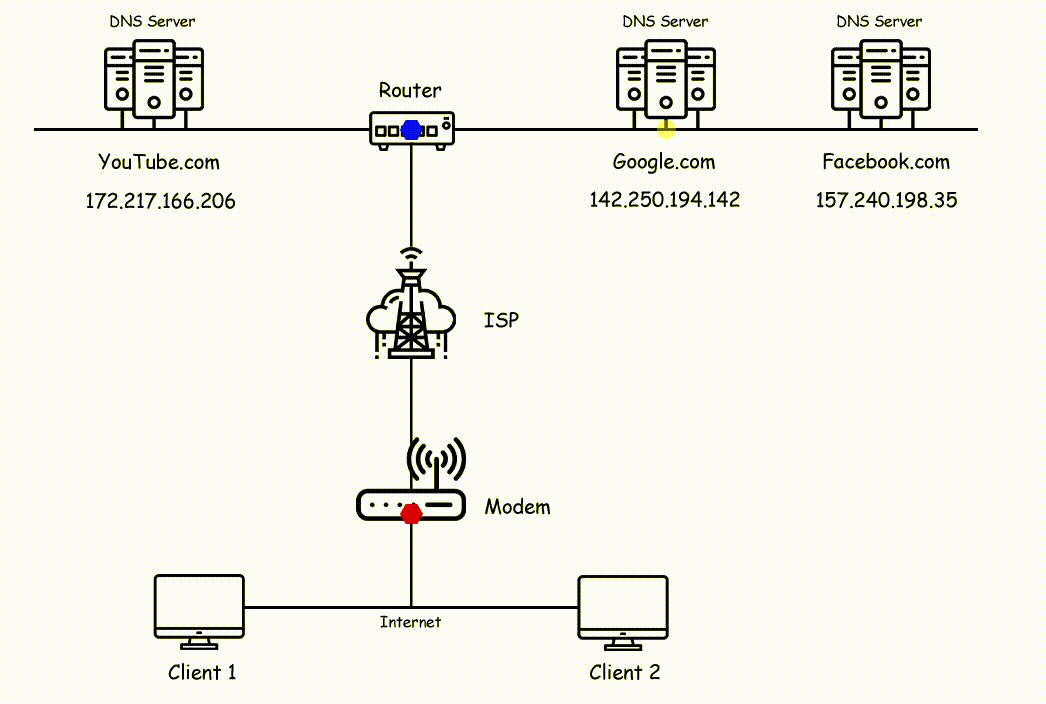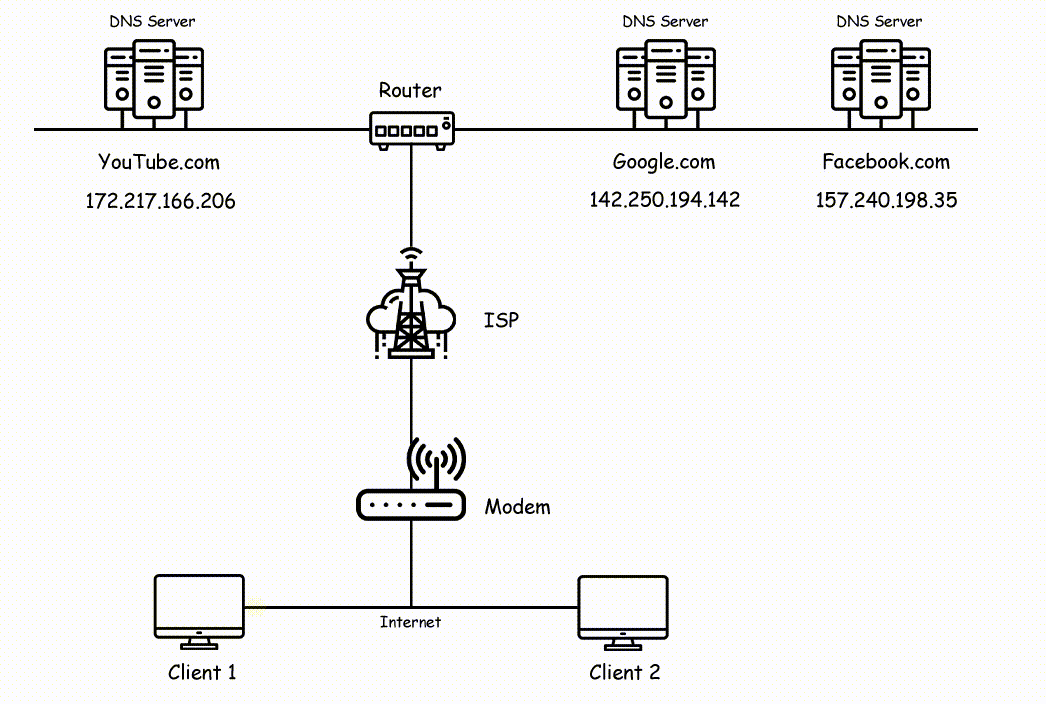
In the above image, you can see two clients are sending a request to different servers where client 1 sending a request to youtube and google's server and client 2 sending a request to facebook's server. All request is known as packets which are broken into chunks and travel through wires.
The data chunks first pass through your modem and your modem sending those chunks to ISP. Now ISP will forward that chunks to the nearest routers and as we know routers will check the physical address of your data and forward that to the right path where they belong.
So Router diverts chunks to the right path and then it reaches the respective servers where again chunks converted into packets and the server looks for your request data.
Now as the response, the server will send back your requested page and again the same process will continue, where it converts packets into chunks and that chunks will reaching your destination by following the nearest path and it will reach your computer.
When chunks reach your computer chunks again converts themselves into packets and shows the result on your screen i.e, Client 1 will see Google.com and Youtube.com and Client 2 will see Facebbok.com.
This is how the internet works in the backend and that process happening in milliseconds.
Types of Network
There are many different types of networks available but all of them are derived from 3 types of networks that we will discuss below, These types can be used for different purposes and by different people and company. Here are some of the networks types that may come across:
LAN
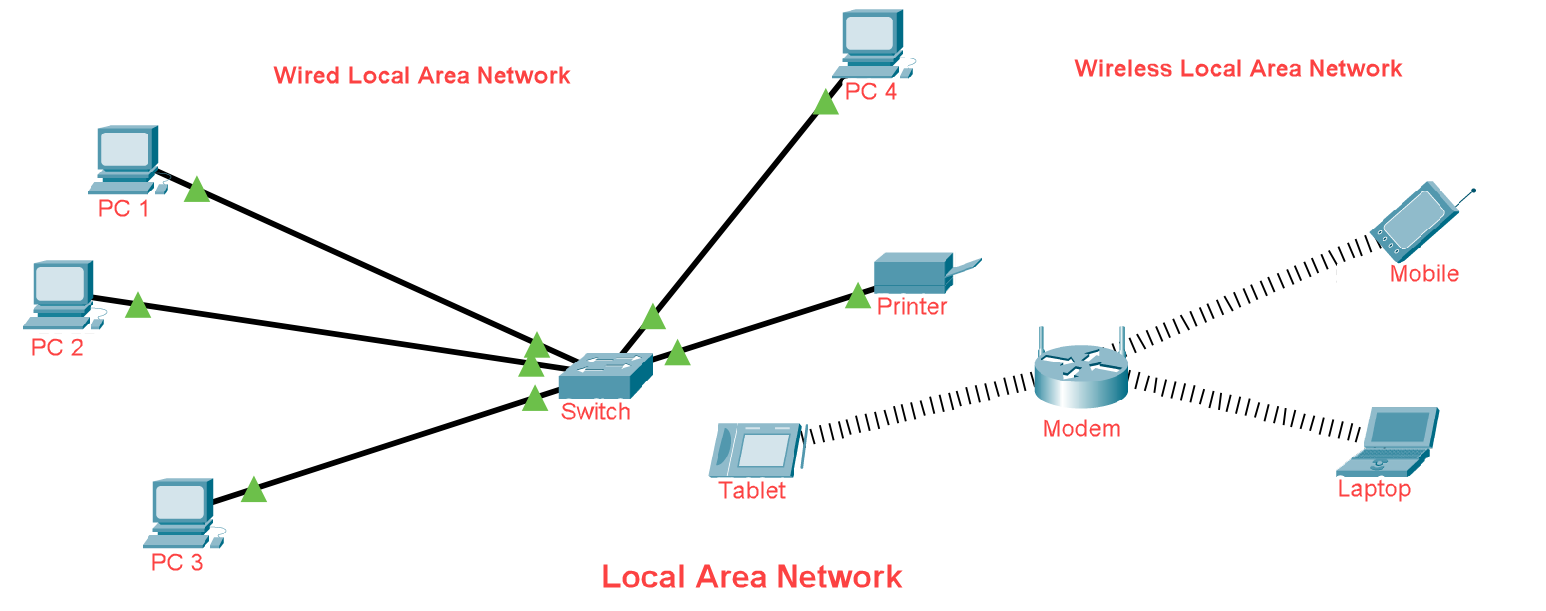
It simply stands for Local Area Network that is a group of networking device such as computers, printers, servers, switches that connected with each other and used to build small environment like school, hospital, apartment etc. It is a very secure connection because it can only communicate within a network where it set up and no outside connection can connect with it.
LAN are a small size network that is considerably faster, their speed can range anywhere from 100 to 100Mbps because of high bandwidth.
LAN's are not only wired nowadays it is also used as wireless, where mobile, tab, laptops also play important jobs. see the below picture for more reference.
MAN
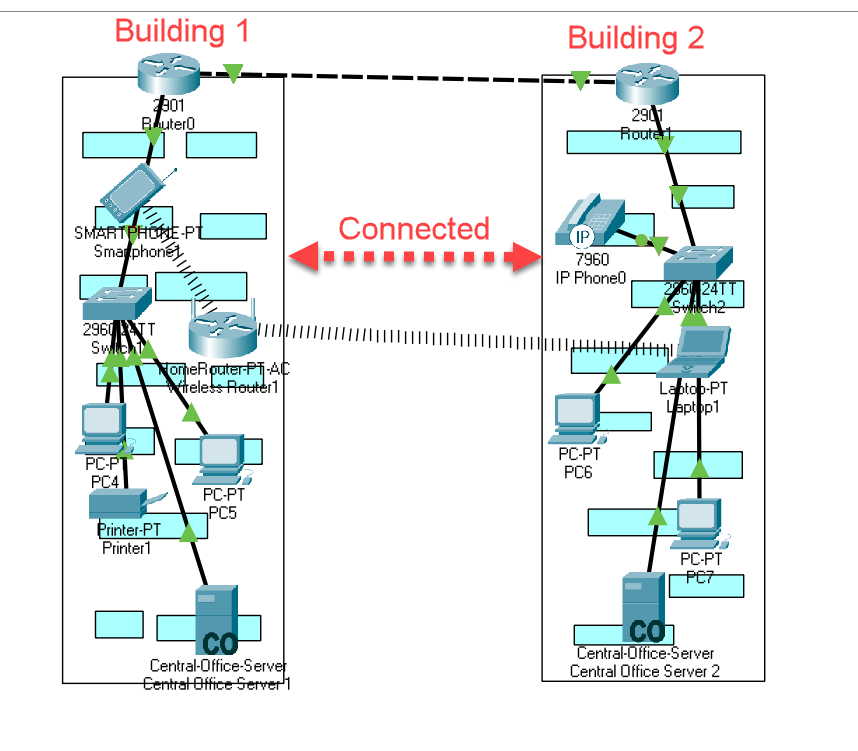
MAN stands for Metropolitan area network that covers a larger area as compared to LAN's. In this various small networks are connected with each other. The size of the Metropolitan area networks is larger than LANs
MANs basically used to cover the largest area of a city or town. This network setup is commonly found in companies and various buildings. Check out the below image to see how these networks looks
WAN
WAN (wide area network) can be easily guessed by its name i.e, a network made to cover wide areas. It provides long-distance transmission of data. The size of the WAN is larger and can cover the country, continent or even a whole world. A very common example of WAN is the Internet
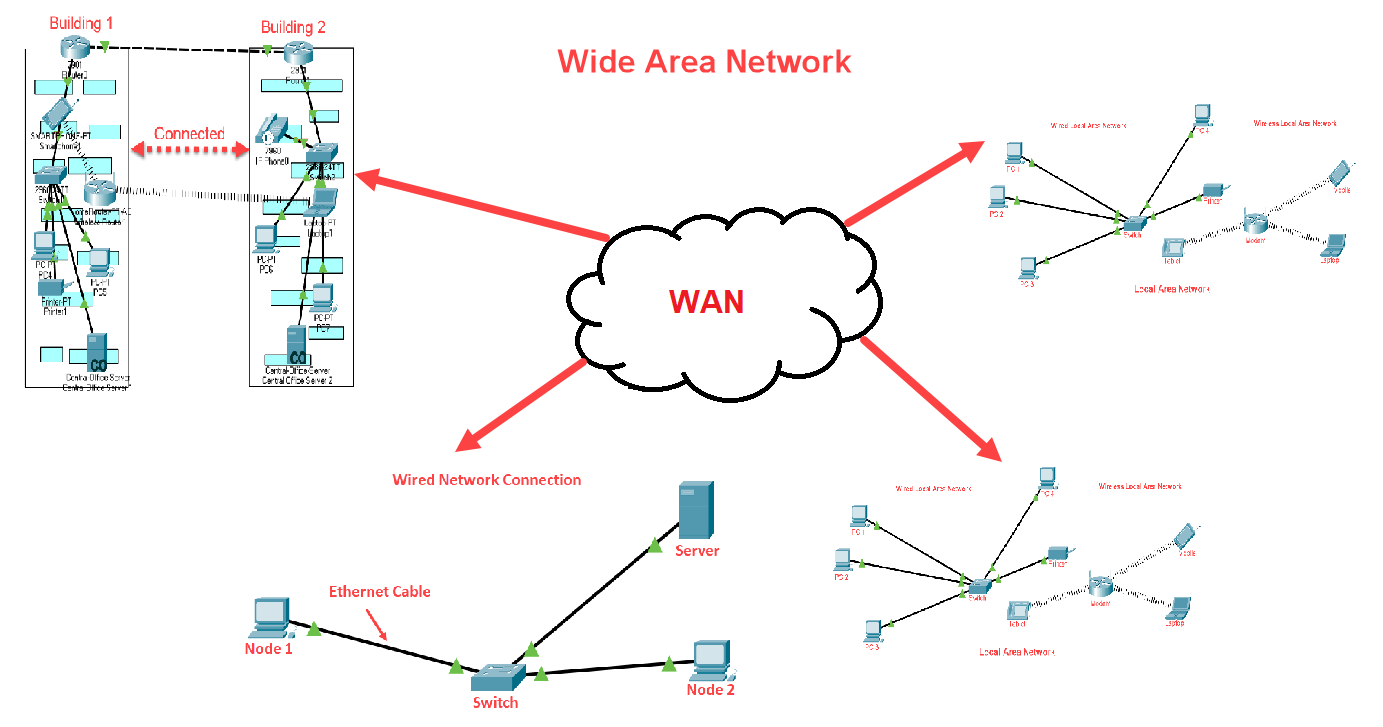
Now there are more such types of networks but all are derived from the above three types that we discussed.
For example PAN (Poratbale Area Network), HAN (Home Area Network), CAN (Campus Area Network) all are smaller versions of LAN. Now same EAN (Enterprise Area Network), BBN (Backbone) are the smaller versions of MAN. GAN (Global Area Network) is just another name of WAN.
Basics of Networking
So let's see some basic rules or standards that everyone should know and follow before making any network.
Standards are the set of rules for data communication that are required for the exchange of information among devices. It is important to follow Standards which are created by various Standard Organizations like IEEE (Institute of Electronics and Electrical Engineers), ISO (International Standards Organization), ANSI (American National Standards Institute) etc.
- The range of IP addresses is starting from 1 and goes up to 255 i.e, the bits of IP addresses can be 10.9.3.1 - 255.255.255.255
- An IP address with all 0s (0.0.0.0) is used to show the default route
- An IP address with all 255s (255.255.255.255) is used for broadcast to all hosts on a network.
- The IP 127.0.0.0 is reserved for diagnostics and testing and known as the loopback address
- There are two types of cables that are used to connect networking device to establish a connection Straight-Through cable and Cross-Over cable
- Straight-Through cable is used when you want to connect two devices of different types together for example switch to router, switch to PC etc...
- Cross-over cable is used when you want to connect two devices of the same types together for example switch to switch, PC to PC etc...
- The size of the packet can be max up to 65,535 bytes, but in reality, no more than 1500 bytes most packets exceed
- Different networks can not communicate directly, they require a device like a router that helps to do communication.
Computer Network Design
So Nowadays there is no such type of predefined topology or designs that anyone can use to design their own networking infrastructure because these designs are varied and depend upon scenarios. This Network design points to the planning of the implementation of a computer network infrastructure.
Network design is simply performed by computer network architects, network support specialists, developers, Technical expert, Network administrators and other related staff to networking. The designing of the network is done before the implementation of a network infrastructure.
It includes the evaluation, understanding and scope of the network to be deployed. The entire network design is typically represented as a network diagram that serves as a design for physical network deployment. Typically, the network layout including the following:
- A logical map will be built
- The structure of cabling will be decided.
- Location, Type, Quantity requires to be a plan where networking devices will be places
- IP addressing ranges need to manage
- Also need to build a budget.
Some topologies still exist from where network designers make their own networks like Star, Mesh, Bus, Ring, Point to Point, Hybrid, Tree and Daisy chain topology. To know more about these topologies you can click on Types of Network Topology
Networking Protocols
If you want to build a network and make a successful communication, you need to follow some rules and standards that must be agreed upon at the end of transmission and reception of the system. These rules and standards are called protocols. Different protocols are used for different types of communication.
So, Whenever computers are connected to a network, they need to use protocols to communicate with each other.
If devices want to communicate over the Internet, they have to use Internet network protocols. There are many networks that are not connected to the Internet but use Internet protocols because they are only made for that.
Now we will see the three categories of protocols under which we will see each and every most usable protocol that you must know.
Network Communication Protocols
Communication protocols are essential for the operation of a network, without protocol network not exist. This is essential for the exchange of messages between your computer and telecommunications systems, both for hardware and software.
Let's see some most used protocols under network communication protocols
- HTTP: It stands for the Hypertext transfer protocol whose main work is to build a communication between your browser and server.
- TCP: Transmission Control Protocol (TCP) distinct data into packets that can be transmitted over a network. These packets can then be sent by network devices like switches and routers.
- UDP: User Datagram Protocol (UDP) works the same way as TCP, transmitting packets of data over the network. The main difference between them is TCP confirms a connection is established between the application and server, but UDP does not.
Network Management Protocols
Network management protocols used to define policies and procedures to monitor, manage and maintain your computer's network, and helps to communicate these requirements across the network to ensure stable communication and optimal performance across the network.
In general, network administrators can use a management protocol to troubleshoot connections between host and client devices.
- SNMP: Simple Network Management Protocol (SNMP) is used to observe and handle network devices. This is a TCP-based protocol that allows administrators to check and modify endpoint information to change the behaviour of devices across the network.
- ICMP: Internet Control Message Protocol (ICMP) is primarily used for troubleshooting. Devices use this protocol to transmit error messages, providing information regarding network connectivity issues between devices. Ping command is the common example for ICMP
Network Security Protocols
Network security protocols ensuring the packets that are transmitting over the network should be secure and not captured by anyone. Its main motive is to provide a secure network.
It usually helps to prevent sniffing attacks from the hacker by the end to end encrypting your data. So let's see some most used security based protocols.
- SSL: Stands for Secure Socket Layer is a network security protocol that provides a secure packet transmission over the internet. It provides an encrypted connection between client to server and server to server. It encrypts data end to end so that no one in the middle can read that data.
- SFTP: Secure File Transfer Protocol (SFTP) is used to securely transfer files across a network. Here data is encrypted and the client/server are authenticated.
- HTTPS: Again it is the hypertext transfer protocol with the "S" that means Secure, you can say that it is the secure version of HTTP. So here the information exchange between the browser and server is encrypted to ensuring protection
Conclusion
Hi Techies, Thanks for reading this blog, I have tried to cover all basic concepts of computer network with real-life practical examples, this blog will very helpful for you If you want to start ethical hacking because I have almost covered all the important concepts of networking.
There are lots of other things in networking that we will cover in our next blog. If you want me to make more such blogs with practical demonstrations then please give the upvote below and comment.
In our next blog, I will tell you some more about network security, the future scope of networking, career opportunities, how to become a network administrator, how to use networking with ethical hacking and much more...
Related Blogs
- Types of Network Topology with Network Topology Diagram
- How to Become an Ethical Hacker | Techofide
- Official Networking Data from CISCO
- What is Metasploit Framework | What is Penetration Testing | How to use Metasploit
- How to Install Metasploit on Windows and Linux | [Step by Step Guide]
- How To Install Arch Linux [Installation Guide] 2023 | Techofide