Hello cyber learners,
In this blog, I will show you what is packet sniffing, the types of packet sniffing, how to perform packet sniffing, how packet sniffing works and a practical demo on Wireshark of how hackers are capturing your data.
We will also see are MITM and Packet Sniffing are the same or not. At the end of this blog, I will share the practical video and show how you can protect yourself from packet sniffing.
If you want to know how to start your career in ethical hacking then you can check my blog on How to Become an Ethical Hacker | Techofide where our IT professional thoughts and experiences are shared.
Before directly understanding packet sniffing let's break it down and understand what is packet and what is sniffing.
So let's get started...
- What is Packet?
- What is Sniffing?
- What is Packet Sniffing?
- How Packet Sniffing Works?
- Types Of Packet Sniffing?
- What is Man In The Middle Attack?
- Is Man In The Middle Attack and Packet Sniffing Both Are Same?
- Requirements To Perform Practical Packet Sniffing
- How to Perform Packet Sniffing?
- A Practical Video on Packet Sniffing
- How To Prevent Man In The Middle Attacks and Packet Sniffing?
What is Packet?
A packet is a small part of the data, or we can say that packet is a small chunk of the message sent over the computer networks.
You can refer to the below image to understand what is packet.
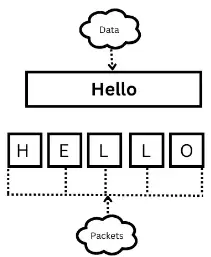
So we will start from the top of the image,
- As you can see data is written in a cloud-shaped image that contains a Hello message.
- Data can not flow over the network as a whole because the network has its fixed size. So if you want to send data to someone then that data should be sent into pieces which are often known as packets.
- So, from the above, you can see the first packet contains an " H " character, the second character contains an " E " character, the third packet contains an " L" character, the fourth packet again contains an " L " character, and the last packet contains an " O " It shows data is fragmented into pieces. In this way, data is flowing over the network.
Note: When the packets reached the destination place then all packets merge and form data which is shown in the above image, which means packets will gain their original form or position.
What is Sniffing?
Sniffing is a technique in computer security that involves intercepting and capturing network traffic in order to obtain sensitive information, such as passwords, login credentials, and other confidential data. It is a form of eavesdropping on a network and can be performed passively or actively.
What is Packet Sniffing?
Packet sniffing is a method of intercepting and examining data packets that are transmitted over a network. The process is carried out using a packet sniffer, a software or hardware device designed to capture and analyze network traffic.
We are continuously telling we are capturing packets but what exactly do that packets contain?
This packet contains sensitive information which leads to financial loss, account takeover, and many more things that can be done through packet sniffing. For example, the packet may contain crucial information like login-id password, account number, OTP, and the conversation between friends.
How Packet Sniffing Works?
Packet sniffing is the process of intercepting and analyzing network traffic to gather data from packets that are transmitted over a network. It works by using a software or hardware device, known as a packet sniffer, to capture and analyze data packets as they travel over the network.
The packet sniffer examines the header and payload of each packet to determine its source and destination, as well as the type of data it contains.
This information can be used for various purposes, such as monitoring network performance, troubleshooting network issues, detecting security breaches, and collecting data for analysis.
However, packet sniffing can also be used maliciously to steal sensitive information, such as login credentials or sensitive data, which is why it is important to secure networks against packet sniffing attacks.
There are many tools available for packet sniffing but Wireshark is the most popular tool even one of my favourites that helps to analyze the traffic over the network.
Types of Packet Sniffing
Now, after learning about what packet sniffing is and how packet sniffing works, Now we will look at the types of packet sniffing.
There are mainly two types of packet sniffing which we will discuss one by one
Active Packet Sniffing
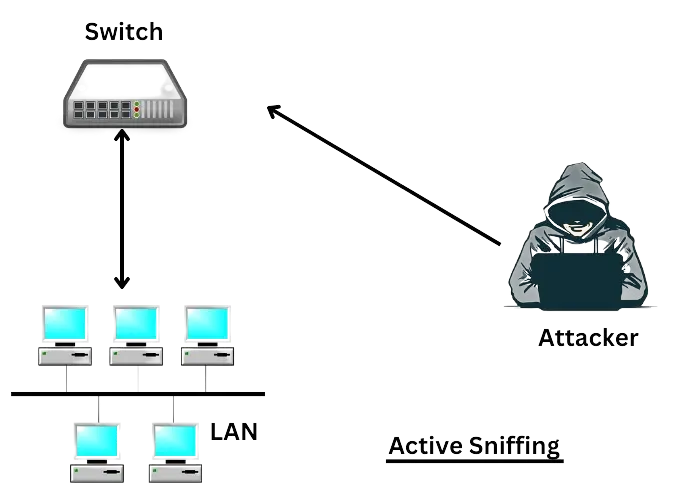
- Active sniffing is a technique used in computer security to capture and analyze network traffic by actively altering the network environment. Unlike passive sniffing, which simply listens to the network traffic without interfering, active sniffing involves sending packets to the network in order to disrupt normal operations or gather information.
- Active sniffing is typically performed on switched networks, where data is transmitted only between the source and destination devices, and not to all devices on the network. To perform active sniffing on a switched network, an attacker must find a way to trick the switch into forwarding the traffic intended for other devices to the attacker's device.
- One common method of active sniffing is ARP ( Address Resolution Protocol ) spoofing, where the attacker sends false ARP messages to the network, claiming to be the IP address of a target device. The switch then forwards all traffic intended for the target device to the attacker's device, allowing the attacker to capture and analyze the traffic.
Passive Packet Sniffing
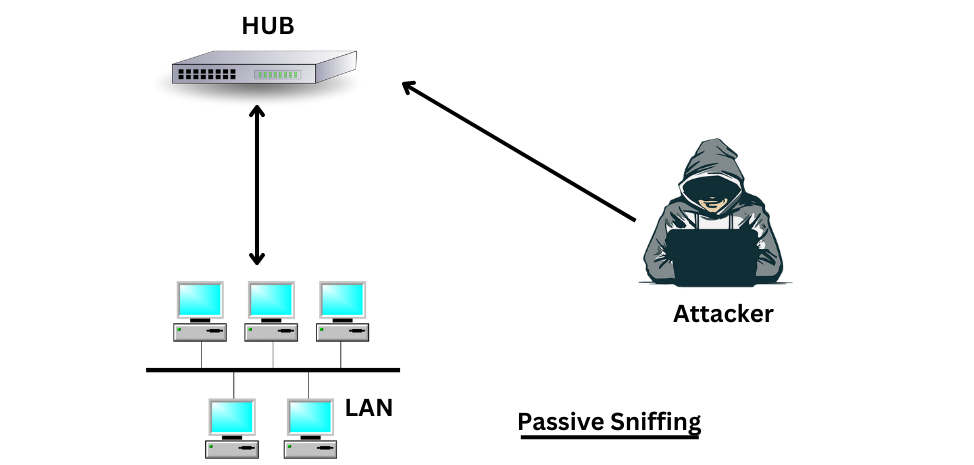
- Passive sniffing is a method of capturing network data packets that are transmitted over a network without interfering with the normal operations of the network. This technique is used to monitor network traffic and gather information such as IP addresses, passwords, email content, and other sensitive information.
- Passive sniffing is performed by placing a network sniffer on a network segment, allowing it to listen to all traffic that is transmitted over the network. The sniffer captures the data packets and analyzes them to gather information. This information can be used for malicious purposes such as stealing sensitive information or for ethical purposes such as network analysis and troubleshooting.
- Passive sniffing is different from active sniffing. Passive sniffing is considered a passive form of attack because it does not interfere with the normal operation of the network.
Note: It is important to note that passive sniffing is not always legal and can have serious consequences. In many cases, it is considered illegal to capture and use network traffic without the permission of the owner of the network or the individuals whose information is being captured.
What is Man in The Middle Attack?
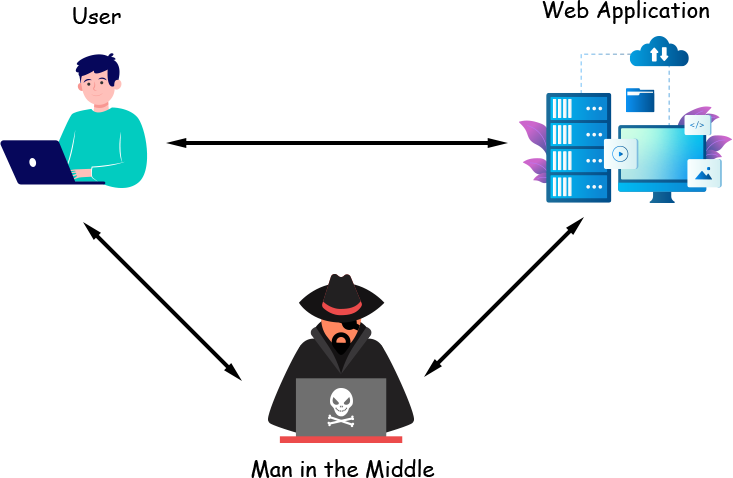
A man-in-the-middle attack is a technique in which an attacker can capture the packet which is flowing over the network. In this, an attacker can sit between the server and the client and capture the packets and steal sensitive information.
In this attack an attacker can compromise the integrity and confidentiality of the data, an attacker can craft malicious packets and trick the victim to respond to the malicious packets. also, an attacker can perform BIB ( Browser In The Browser ) attack.
It is hard to identify the man-in-the-middle attack.
What is a BiB attack?
A "browser in the browser" (BIB) attack is a type of security vulnerability that allows an attacker to embed a malicious browser inside a legitimate website or web application. This malicious browser can then be used to steal sensitive information, such as login credentials or financial information, or to perform other malicious actions.
In a BIB attack, the attacker creates a malicious iframe within a legitimate website. Iframe is a HTML tag used to create a seprate window within the browser. The iframe is designed to look and function like a separate browser window, and the user may not be aware that it is running within the context of a legitimate website. The attacker can then use this malicious iframe to carry out phishing attacks, steal sensitive information, or perform other malicious actions.
In the Man in the middle attack, we mentioned some terms confidentiality and integrity if you are not aware of that terms then don't worry below I have described them for you in easy language.
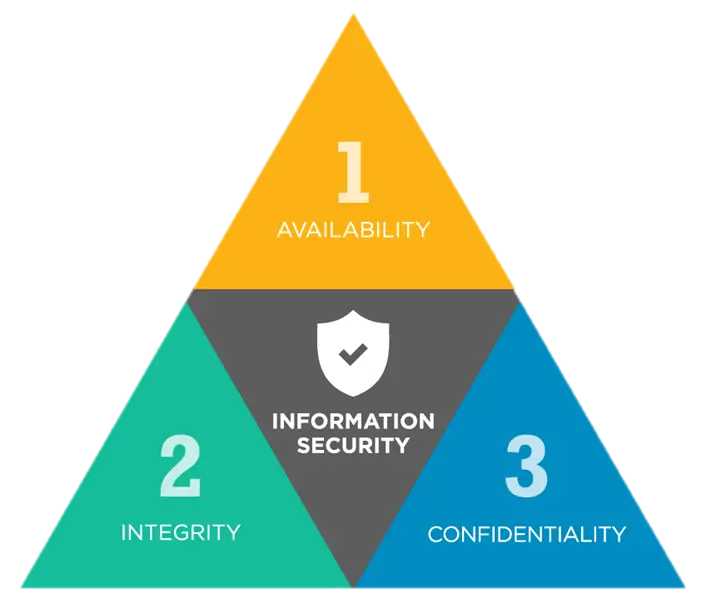
So, Cyber Security works with three pillars which are confidentiality, integrity and availability.
These pillars represent the core principles of effective cybersecurity and are used to guide the development and implementation of security measures to protect against cyber threats.
-
Confidentiality: Confidentiality is the principle of ensuring that sensitive information is protected from unauthorized access or disclosure and is only available to authorized individuals.
-
Integrity: Integrity measures aim to prevent malicious actors from altering or modifying sensitive information and to ensure that information is accurate and consistent.
-
Availability: Availability is the principle of ensuring that information and systems are available and accessible to authorized users when they need them.
Man In The Middle Attack And Packet Sniffing Both are Same?
Yes, both are the same but there is a minor difference between these two, In Man In The Middle attack an attacker can modify/alter the data packet but in Packet Sniffing an attacker can not modify/alter the data packet.
Both are different we will discuss them on the basis of different criteria let's discuss them one by one
- Purpose: MITM attacks are carried out with the intention of intercepting and manipulating communication between two parties, while packet sniffing is used for analyzing network traffic.
- Active vs Passive: MITM attacks are active attacks as the attacker actively intercepts and manipulates communication, while packet sniffing is a passive method of capturing and analyzing network packets.
- Involvement of the parties: In MITM attacks, the attacker is positioned between the two communicating parties, while in packet sniffing, the attacker is simply observing network traffic.
- Modification of data: In MITM attacks, the attacker can modify the communication between the two parties, while in packet sniffing, the attacker can only observe the data being transmitted.
- Legitimate use: Both MITM and packet sniffing can be used for malicious purposes, but packet sniffing can also be used for legitimate purposes such as network troubleshooting and monitoring by network administrators.
Man In The Middle Attack (MITM) can change the integrity of the packet and this is another way of Shoulder Surfing.
What is Shoulder Surfing?
Shoulder surfing is a type of social engineering or physical attack where a person tries to gather sensitive information by looking over the shoulder of someone who is entering it into a computer or a mobile device. The attacker tries to see the password, PIN, or other confidential data as it is being typed, often in a public place such as an ATM or a busy street.
Now we have a basic understanding of packet sniffing, with its working and types so it is time to see that attack practically.
Get ready with your systems to dig into the attack.
Requirements to Perform Packet Sniffing Practical?
There are a few requirements to perform a packet sniffing attack which are mentioned below:
- Wireshark: We need a packet sniffer tool. I am going to use the Wireshark. If you don't know what is Wireshark, how to install and use it then you can check my blog on How to install and use Wireshark
- Victim Machine: The victim machine will be any machine it may be your android phone, Windows, macOS, or Linux, in my case, I will use the same Kali machine. Basically, we required a device to generate traffic so we can capture packets.
- Attacker Machine: The machine where you have installed Wireshark will be your attacker machine. In my case, it is Kali Linux.
Note: You can use Kali Linux as an attacker machine because the Wireshark is pre-installed on that machine. Don't know what is Kali Linux and how to install don't worry check my blog on how to install Kali Linux.
How to Perform Packet Sniffing
Now, after learning all about what packet sniffing is, how packet sniffing works, the types of packet sniffing, and a man-in-the-middle attack. we will learn practically how to perform packet sniffing.
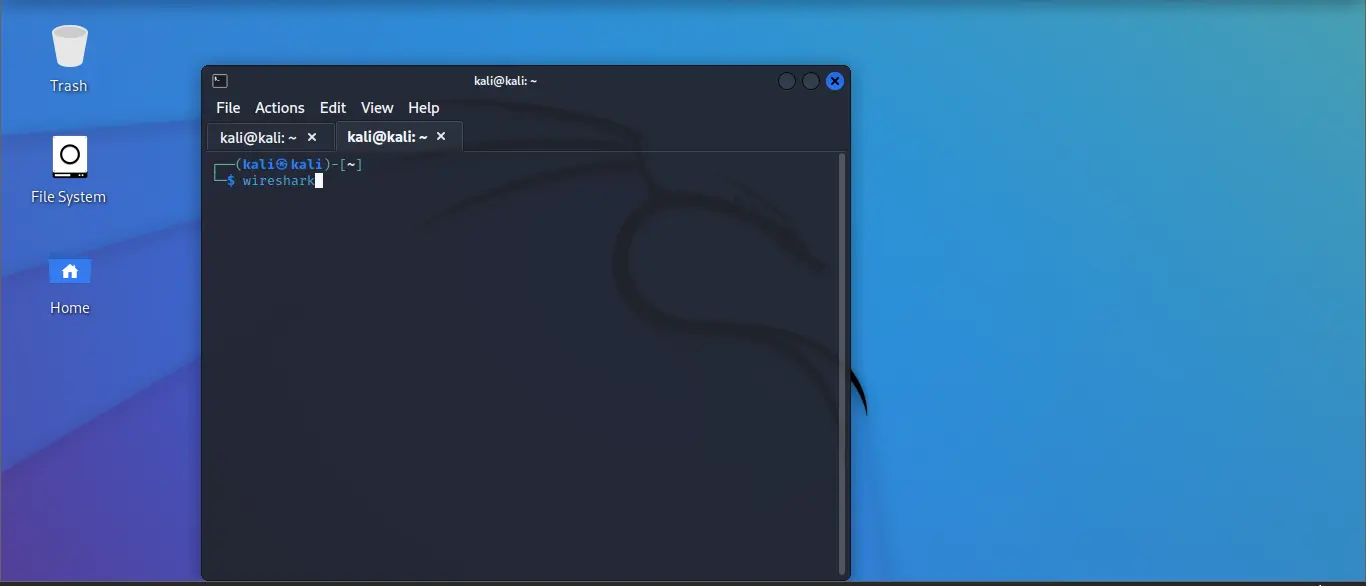
Step 1: In your Kali Linux open the terminal and type the command that is shown below.
wireshark
You can see the same in the below screenshot. You just need to wait for a few seconds and it will open the Wireshark tool.
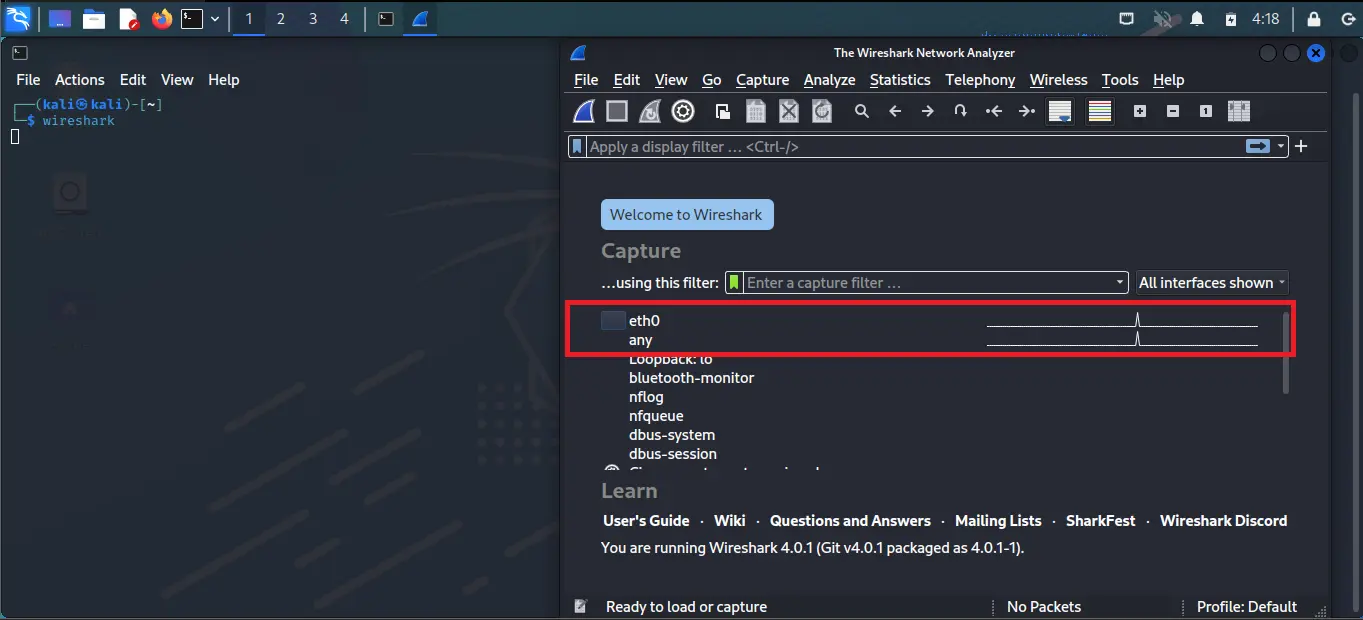
Step 2: Once your Wireshark start you can see many network interfaces, along with each interface you can see there is a wave, which indicates the network has a flow of traffic.
Step 3: Before entering into any interface let's see what we need to open in our victim machine.
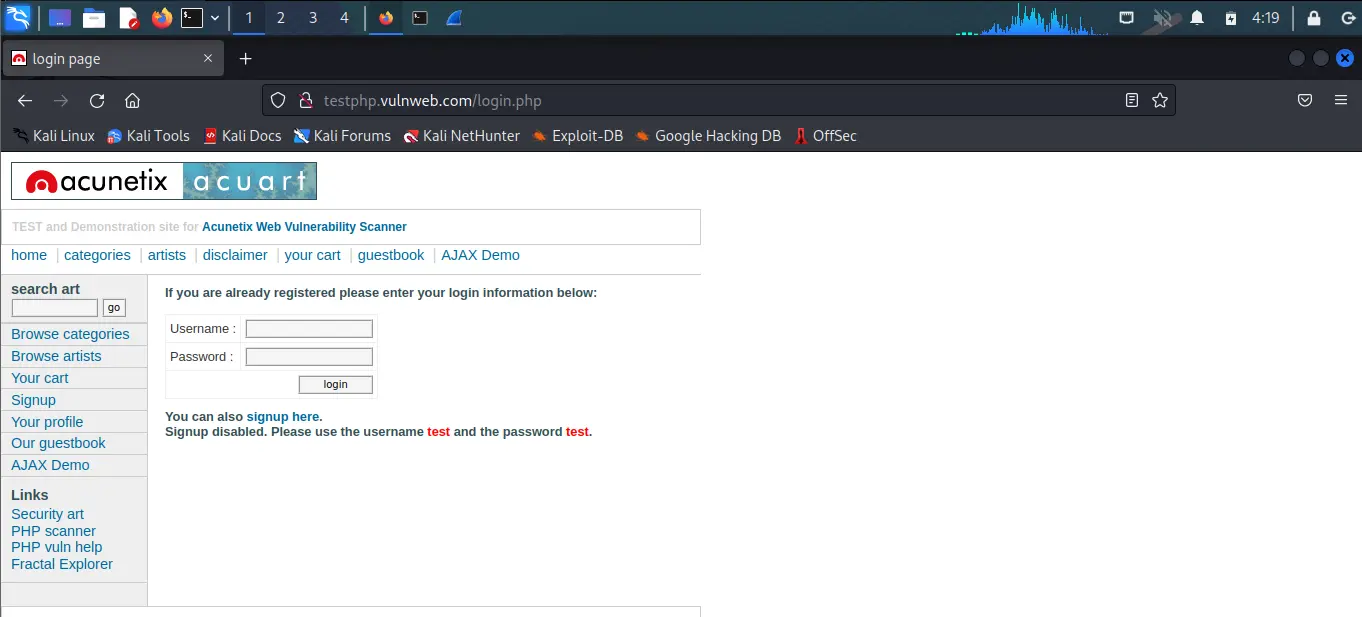
So I am using vulnweb website to demonstrate the practical. This website is opened in my Kali Linux. You can open it on any device where you want but just make sure it is connected to the same network where your other devices are connected i.e, on the same Wi-Fi
You can see the same in the below screenshot.
Note: I am using vulnweb website because it is made to perform practicals like this and the admin mentioned the same on the website which means we are allowed to perform such attacks. I also suggest you to perform on the same website. Performing such attacks on other websites without permission is illegal and we are not promoting any illegal activities. Techofide will not responsible for any illegal activity done by you.
Step 4: As you can see in the below image eth0, any, Bluetooth-monitor etc... are the available interfaces in my machine, I select eth0 because the victim machine runs on the eth0 interface in my case, the selected interface is highlighted with colour in the below snapshot.
In your case interface might look different. If you are using Wi-Fi then the interface name might start with Wi-Fi. Before choosing any interface make sure that is active which you can easily examine by checking the waves in front of the interface.
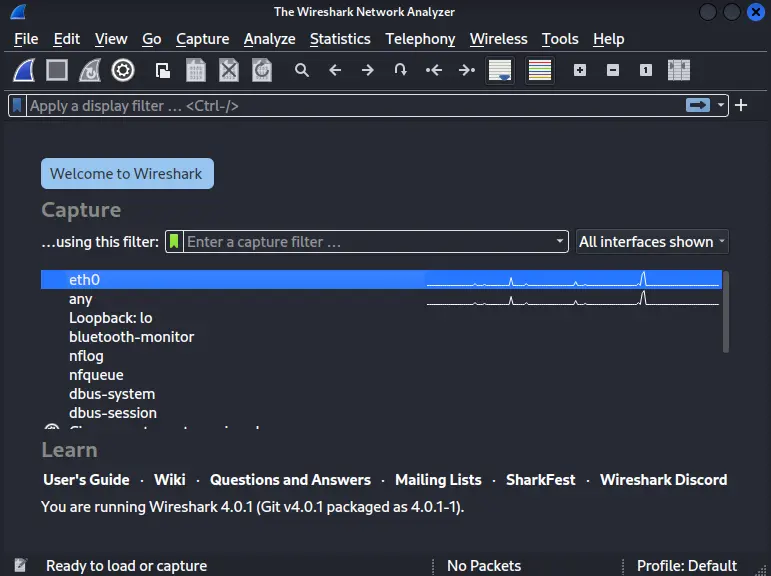
Step 5: Click on start capturing packets after selecting the interface, you can see in the below screenshot the Wireshark start packet capturing.
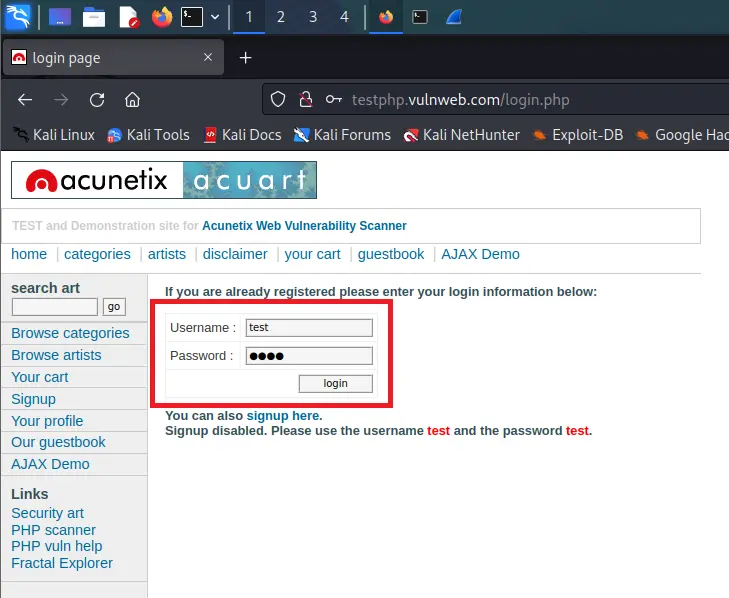
Step 6: Go to vulnweb website and enter the credentials username as test and password as a test, and click login. You can enter any credential you want.
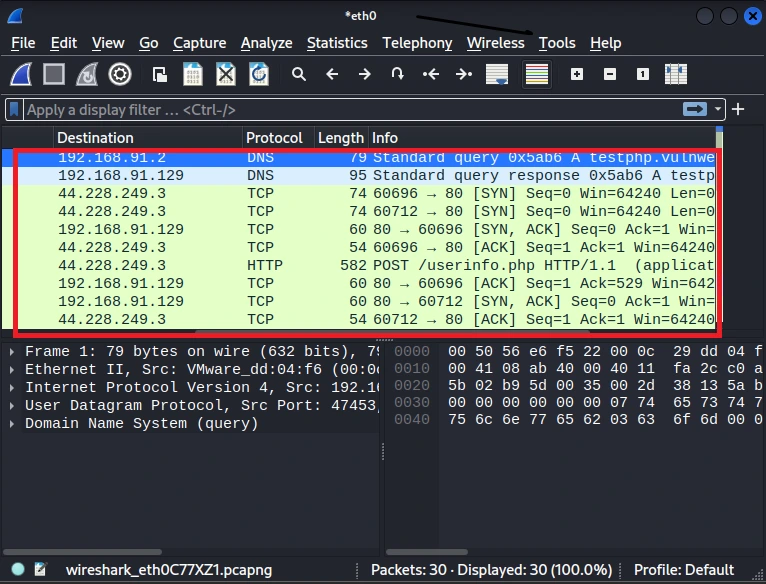
Step 7: After clicking on login go to Wireshark and stop capturing the network packets, The button is on the top right corner in red colour.
After that, you can see that there are lots of packets, and it is difficult to find the particular packet, So in order to find the packet you have to filter the packets by entering the protocol name, here we know the website is using HTTP protocol so I entered HTTP keyword on the search bar.
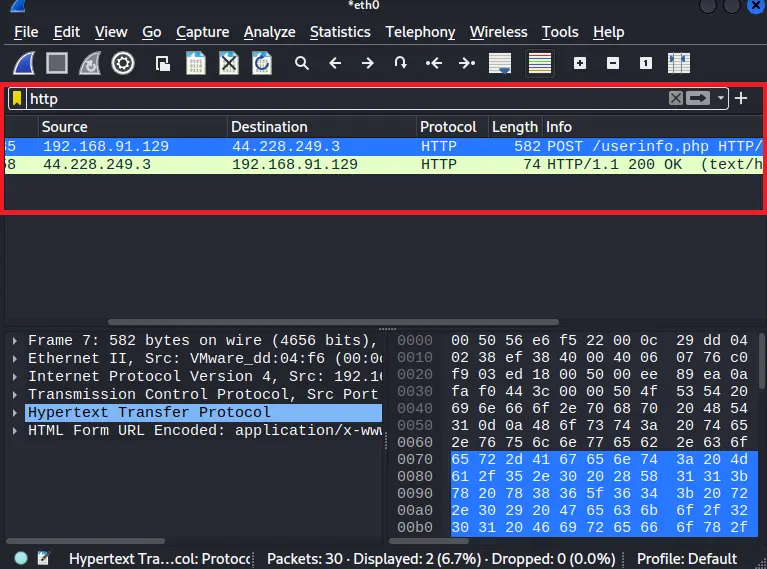
Step 8: After filtering the packet you can see HTTP protocol packets, now right click on the HTTP protocol packet, and you can see lots of options available, go to the Follow option after that you can see the TCP stream and HTTP stream click on TCP stream option.
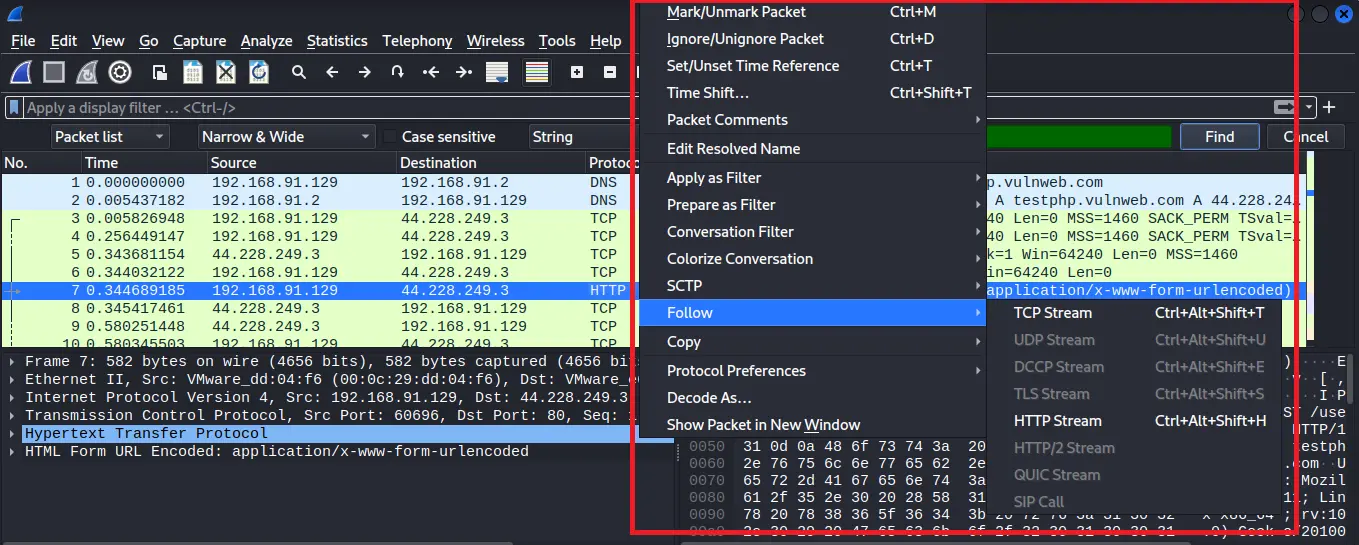
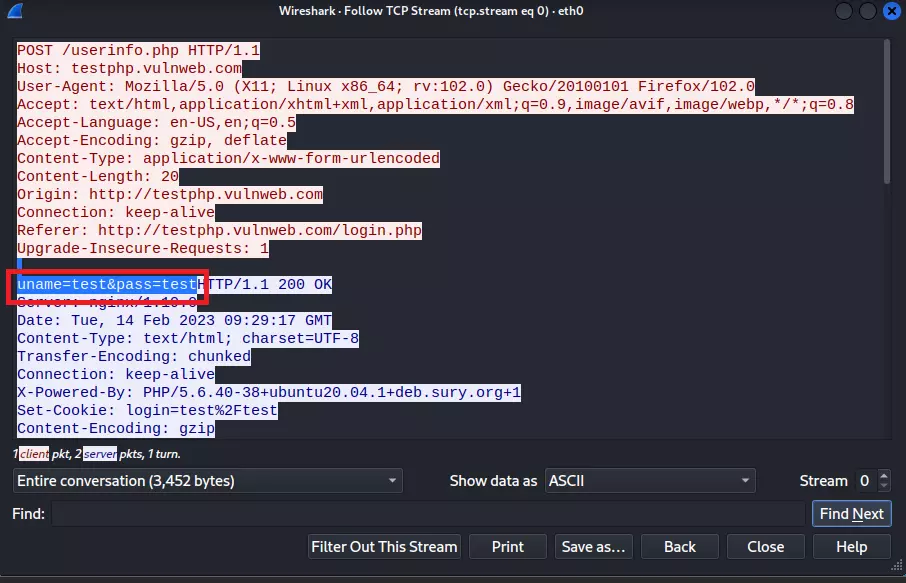
Step 9: After clicking on the TCP stream option a new window will open and you have to navigate for uname and pass keywords in the packet, as you can see in the below image in my case uname and pass is showing credentials.
How to prevent Packet Sniffing and Man In the Middle attacks?
Now, we will learn about the prevention of Packet Sniffing and Man In the Middle attacks, because prevention helps us to be safe from Packet Sniffing and man In the middle attacks.
- Always visit or surf https:// based websites rather than http:// because https provide secure data transmission by encrypting data end to end. As you can see below pictures HTTPS website is secure and a lock symbol is present on https website, and in HTTP websites are Not Secure, so anything can be visible on the link or textual form.


- Always avoid entering data/credentials on HTTP websites because network traffic on HTTP protocol is not encrypted so anyone can sniff the packet and read your data.
- Always check the spelling of the domain name. For example, the fake page of AMAZON might be written as AMAZ0N here you can see we just replace the letter 'O' with the number '0'
- Avoid using open/public networks like any Wi-fi from airports, Hotels, Coffee shops etc... (But if it is necessary to use then always connect with VPN)

A Practical Video on Packet Sniffing
It is time now to watch a practical demonstration in the video of how to perform packet sniffing. So below is the video watch it and increase your practical knowledge.
Conclusion
Packet Sniffing is a powerful technology that can be used for both good and bad purposes. It allows network administrators to monitor and troubleshoot network issues, while also allowing attackers to steal sensitive information or disrupt network operations.
To prevent unauthorized packet sniffing, organizations should implement security measures such as encryption, network segmentation, and access controls. Additionally, network administrators should be vigilant in monitoring network activity and be trained in detecting and responding to security threats.
Overall, packet sniffing is a crucial aspect of network security and should be approached with caution and a thorough understanding of its potential risks and benefits.
I hope you like this blog, please like, share, and drop your comment below it will be great support from you
Thanks for reading this article
Commonly Asked Questions
Que 1: Is packet sniffing on a public network legal?
Ans: The legality of packet sniffing on a public network depends on various factors, such as the terms of service of the network, the intent behind the sniffing, and the type of data being collected. Collecting sensitive information without consent is likely illegal, while monitoring network traffic for security or research purposes and collecting non-sensitive information may be legal. However, local laws and regulations should be consulted before engaging in any packet sniffing activity.
Que 2: Is packet sniffing detectable?
Ans: Detection of packet sniffing is possible through monitoring network traffic for unusual activity, using IDS/IPS systems. If you are targeting a comapny then it can be easily track by the network or security team.
Que 3: Are there any packet sniffing tools for iPhone or Android?
Ans: Yes, there are packet sniffing tools available for both iPhone and Android devices. One example of a packet sniffing tool for iPhone is iNetTools Pro, which includes a network scanner and packet sniffer. Another example is Wireshark, which has an app available for Android devices that allows users to capture and analyze network traffic.
Related Blogs
- What is Wireshark | How to Use Wireshark [Practical Demo]
- How to Install Kali Linux Step By Step Guide
- What is Computer Network | Basics of Networking [With Practical Examples]
- Types of Network Topology with Network Topology Diagram | Techofide
- What is DoS Attack | How to do Denial of Service Attack [Practical Demo]
- Nmap Commands | How to Use Nmap Tool
- Linux Commands | Linux Commands Cheat Sheet
- What is OSINT? | OSINT Framework | Tools for OSINT | Best OSINT Techniques
- What is Smurf Attack? | What is the Denial of Service Attack? | Practical DDoS Attack Step-By-Step Guide