Hello cyber learners,
Welcome back to our ongoing journey into the complex world of the dark web. This is our second blog of the Dark Web Operation series. In our previous blog post, we delved into the depths of the dark web, unravelling its mysteries and shedding light on its elusive nature. If you missed it, you can catch up by visiting What is the Dark Web | Is the Dark Web Illegal? - An Introduction
Today, we embark on a journey to deepen our understanding of this enigmatic corner of the internet as we delve into "How to Access Dark Web". So, grab your virtual flashlight and join me as we navigate through the shadows to uncover what lies under the surface.
Caution: This post is just for educational purposes. The links I have shared are only to aware you of the dark web. Techofide is not responsible if you use those links in illegal activities.
- What is the Dark Web?
- How to Use Dark Web Links Safely
- How to Access Dark Web
- Best Dark Web Sites in 2024
- Legal Considerations for Darkweb Users
- Conclusion
- Commonly Asked Questions
What is the Dark Web?
Before we delve into safety measures, let's briefly revisit what the dark web entails. Unlike the surface web accessible through conventional search engines, the dark web operates on encrypted networks, requiring specialized software like Tor. Anonymity is the power of the dark web, which makes it a haven for various activities, including cybercrime, illicit trade, and anonymous communication.
How to Use Dark Web Links Safely
Before directly accessing or using dark web links we need to make sure we are taking care of all possible security measures. I have mentioned below the mandatory one.
- Update your Tor browser and use strong antivirus and firewall protection before delving into the dark web. If you are using an updated version of Windows, then just keep your default Windows Defender turned on.
- Avoid clicking suspicious links and interactions, and prioritize security over curiosity.
- Verify URLs and sources carefully to minimize security risks.
- Protect your identity by refraining from sharing personal information.
- Be aware of potential scams and risks associated with cryptocurrency. Exercise caution and research thoroughly before engaging in financial transactions on the dark web.
- Stay informed about emerging security threats and trends by actively participating in professional cybersecurity communities and forums. Continuously monitor the evolving landscape of the dark web.
How to Access Dark Web
To begin your journey into the dark web, you'll need reliable tools that prioritize security and anonymity.
Step 1: Download the Tor browser from the official website (https://www.torproject.org/) and install it on your device.
For this, refer to our Tor installation blog: What is Tor | How to Use Tor Browser?
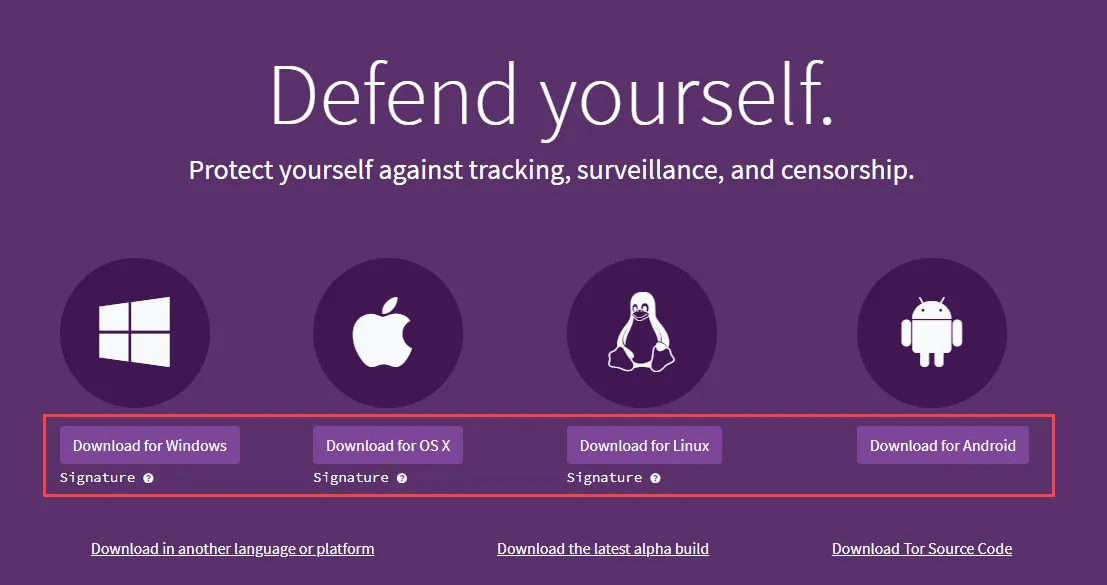
Step 2: After installation, Launch your Tor Browser and search for any website you want. In my case, it is techofide.com (You can go for any other website if you want)
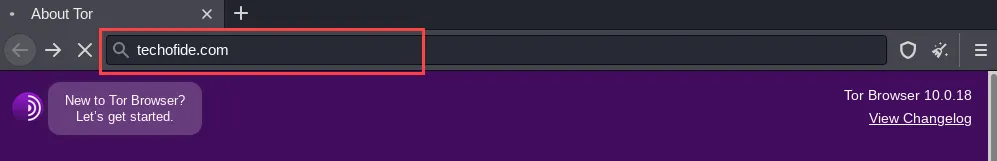
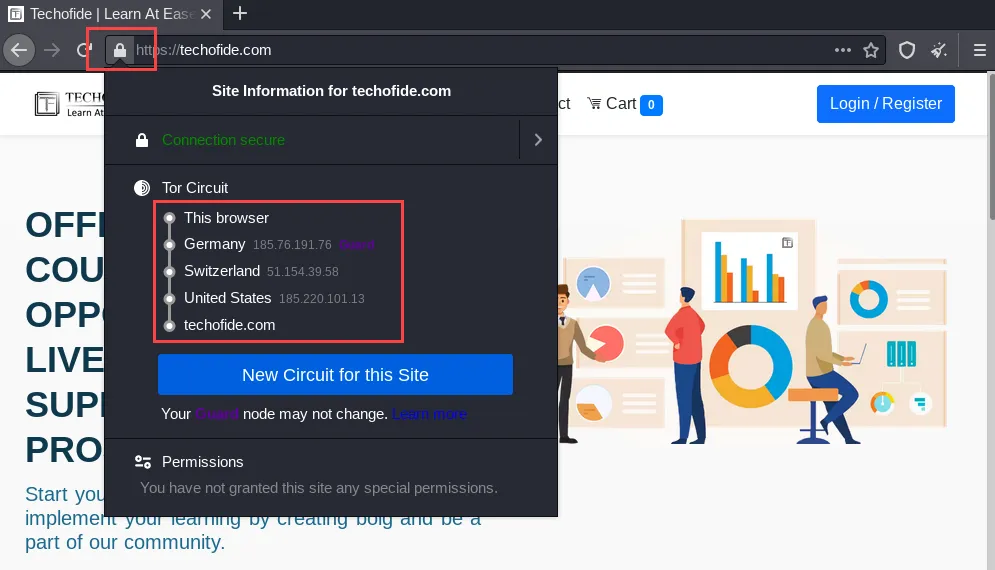
Step 3: Click on the Lock icon to check the layers from which you came to your desired website. Now in the below image, you can see our request first passes from Germany, then it passes from Switzerland and at the end, it passes from the United States and reaches to techofide.com
Step 4: If you want to change your Identity again, you can click on a new identity. It will close your Tor Browser and reconnect you with the Tor network. Check the below image for reference.
Step 5: Now, you are ready to explore the dark web! below, I have provided some best dark websites from which you can start your journey.
Note: There are other advanced options as well to enable you to make your Tor more secure. However, it is optional but in case you want to configure it for more security you can check my post on How to safely use the Tor browser
Avoid sharing any identifiable details or using real credentials on any platform. Exercise Professionalism and Ethical Conduct As a professional navigating the dark web, uphold ethical standards and responsible behavior at all times. Refrain from engaging in illegal activities or supporting illicit content. Remember that your actions reflect on your professional reputation, so prioritize integrity and professionalism in your online interactions.
Best Dark Web Sites in 2024
I have shared the top 10 best websites that I use in my day-to-day life to browse the dark web.
Ahima
Ahmia is the Google of the dark web. launched in 2014, carves a unique niche as a search engine specifically designed for the Tor network. Unlike Google and other search engines, Ahmia doesn't index the traditional web. Instead, it delves into the onion sites – hidden services accessible only through the anonymizing Tor browser. This opens the door to a vast, often veiled world of information, fostering legitimate and potentially illicit content.
While Ahmia filters out illegal activities like child pornography, navigating this hidden landscape responsibly remains crucial. Despite its niche focus, Ahmia boasts over 5,000 indexed sites, making it a valuable tool for researchers, journalists, and anyone seeking information beyond the clear web's surface. However, remember, with anonymity comes the potential for encountering undesirable content, so exercising caution is paramount.
Link:
juhanurmihxlp77nkq76byazcldy2hlmovfu2epvl5ankdibsot4csyd.onion
Proton Mail
You should not use Gmail and Outlook to create accounts on dark websites, because it may lead to break your privacy. Instead of using traditional Gmail, you can use Protonmail as an email provider. ProtonMail's website stands out in the crowded email landscape by prioritizing user privacy and security.

Their website serves as a portal to the encrypted email service, offering additional privacy-focused tools like Proton Drive and Calendar.
Link:
protonmailrmez3lotccipshtkleegetolb73fuirgj7r4o4vfu7ozyd.onion
Dread
Dread emerges as a pivotal dark web forum reminiscent of Reddit, specifically tailored for discussions surrounding darknet markets. Despite encountering temporary disruptions in 2019, Dread persists as a resilient platform, facilitating discussions ranging from the dissemination of stolen data to intricate guides on illicit drug production.
Furthermore, it serves as a forum for analyzing market closures and vulnerabilities, fostering an exchange of information crucial for navigating the clandestine digital realm.
Link:
dreadytognbh7m5nlmqsogzzlxjy75iuxkulewbhxcorupbqahact2yd.onion
XSS.is
XSS.is emerges as a hub for the Russian hacking community, providing a platform for discussions, collaboration, and the exchange of tools and techniques. Founded on the principles of anonymity and expertise, XSS.is facilitates a space where individuals with diverse skills converge to share insights and resources related to cybersecurity and digital intrusion.

From discussions on the latest exploits to tutorials on penetration testing, the forum serves as a valuable resource for both aspiring and seasoned hackers alike. However, it's essential to approach such forums with caution, as participation in illicit activities can have serious legal repercussions.
Link:
xssforumv3isucukbxhdhwz67hoa5e2voakcfkuieq4ch257vsburuid.onion
Adamant Decentralized Messenger
Adamant Decentralized Messenger is a privacy-focused messenger for dark web users. It offers a secure and private communication platform built upon blockchain technology. With an emphasis on decentralization and encryption, Adamant ensures that messages remain confidential and tamper-proof, free from the prying eyes of third parties.

Link:
adamant6457join2rxdkr2y7iqatar7n4n72lordxeknj435i4cjhpyd.onion
Secure Drop
SecureDrop provides a secure platform for whistleblowers to anonymously submit sensitive information to journalists and media organizations. Developed by the Freedom of the Press Foundation, The website serves as the entry point to this encrypted platform, where individuals can securely share documents and communicate with journalists without fear of reprisal or exposure.
By facilitating the exchange of information vital to public interest reporting, SecureDrop empowers whistleblowers to shine a light on corruption, injustice, and wrongdoing while safeguarding their identities.
Link:
sdolvtfhatvsysc6l34d65ymdwxcujausv7k5jk4cy5ttzhjoi6fzvyd.onion
Infocon
InfoCon is a centralized archive of hacking convention materials led by volunteers and initiated by The Dark Tangent. It aims to provide year-round access to hacking-related content, originating from DEF CON's "hard disk duplication village" in 2014. This collaborative effort consolidates resources, fostering community collaboration and knowledge sharing within the dark web ecosystem.
Link:
w27irt6ldaydjoacyovepuzlethuoypazhhbot6tljuywy52emetn7qd.onion
CIA
The CIA's dark web presence reflects a shift towards digital engagement, offering a discreet platform for accessing sensitive materials and secure communication. Providing insights into historical events and contemporary intelligence methods, it underscores the agency's adaptation to the evolving digital landscape while upholding transparency within national security boundaries.
Link:
ciadotgov4sjwlzihbbgxnqg3xiyrg7so2r2o3lt5wz5ypk4sxyjstad.onion
Comic Book Library
The Comic Book Library on the dark web hosts a diverse collection of free comics, spanning classic superheroes to niche publications, catering to enthusiasts worldwide. Its user-friendly interface facilitates easy browsing and downloading, fostering a sense of community among fans. Offering access to comics that may be hard to find elsewhere, the library invites readers to explore the vibrant worlds of sequential art, regardless of geographical or economic constraints.
Link:
nv3x2jozywh63fkohn5mwp2d73vasusjixn3im3ueof52fmbjsigw6ad.onion
Hidden Answers
Hidden Answers functions as a dark web counterpart to Quora and Reddit, providing an anonymous space for users to ask and answer questions on a wide range of topics. While the platform offers a diverse array of discussions, from the mundane to the profound, users should be prepared for unfiltered content.
It serves as a valuable resource for newcomers seeking information about the dark web, with minimal restrictions on topics discussed, except for illegal activities.
Link:
7eoz4h2nvw4zlr7gvlbutinqqpm546f5egswax54az6lt2u7e3t6d7yd.onion
Random Chat
Random Chat offers a straightforward and minimalist approach to connecting with strangers within the dark web community, providing a platform for spontaneous and anonymous interactions. With no registration required, users can dive into conversations immediately upon landing on the site, engaging in one-on-one chats with random individuals selected by the platform.
Users have the freedom to discuss any topic within the bounds of legality, with the option to share links and upload files to enrich their conversations. With no lingering traces of past chats, each interaction on Random Chat is ephemeral, emphasizing the transient nature of connections forged within the dark web's enigmatic realm.
Link:
notbumpz34bgbz4yfdigxvd6vzwtxc3zpt5imukgl6bvip2nikdmdaad.onion
Legal Considerations for Darkweb Users
As individuals from around the world explore the dark web and utilize tools like Tor for privacy and anonymity, understanding the legal landscape is essential to staying within legal boundaries. Laws and regulations vary between countries, and knowledge of relevant legal frameworks can help users navigate potential legal risks effectively.

Understanding Legal Frameworks
As a professional, you should also be familiar with certain laws and regulations for using Dark Web
Dark Web Laws: In the United States, laws such as the Computer Fraud and Abuse Act (CFAA) prohibit unauthorized access to computer systems, including those on the dark web. Additionally, the Controlled Substances Act regulates the sale and distribution of illicit drugs, which may extend to transactions facilitated through dark web marketplaces.
In India, the Information Technology (IT) Act addresses various cybercrimes, including hacking, data theft, and identity fraud, which may apply to illegal activities conducted on the dark web. The Narcotic Drugs and Psychotropic Substances Act (NDPS) regulates the sale and distribution of narcotics, including those traded on the dark web.
Tor Usage Laws: While using Tor itself is legal in most countries, engaging in illegal activities using Tor can lead to legal consequences. Laws related to cybercrime, child exploitation, and intellectual property infringement may apply to Tor users who violate legal boundaries.

Conclusion
Exploring the dark web demands a cautious approach that balances curiosity with safety and legal considerations. Users must prioritize personal security by fortifying digital defences, adopting safe browsing practices, and staying informed about potential threats. Utilizing tools like VPNs, Tor, and secure browsers can enhance anonymity but requires regular updates and vigilance against vulnerabilities. Additionally, maintaining ethical conduct and adhering to legal boundaries are crucial for responsible navigation. By embracing these principles, users can unlock the potential of the dark web while safeguarding their privacy, security, and reputation.
Commonly Asked Questions
Q1. Are there any legal risks associated with using Tor or browsing the dark web?
Ans. While using Tor itself is legal in most countries, engaging in illegal activities on the dark web can have legal consequences. It's essential to understand the legal frameworks in your jurisdiction and adhere to ethical and legal boundaries while browsing the dark web.
Q2. How can I ensure the security of my digital devices while accessing the dark web?
Ans. You can enhance the security of your devices by:
- Keeping your operating system, browser, and security software up to date to patch vulnerabilities.
- Avoiding downloading files or clicking on suspicious links while on the dark web.
- Using a separate virtual machine (VM) or sandbox environment to open potentially harmful files, rather than running them directly on your host machine.
Q3. Can I use the dark web for legitimate purposes, such as accessing secure communication platforms or obtaining information anonymously?
Ans. Yes, the dark web can be used for legitimate purposes, such as accessing encrypted communication platforms like ProtonMail or submitting sensitive information to journalists through platforms like SecureDrop. However, it's essential to exercise caution and ethical conduct while navigating the dark web to avoid involvement in illegal activities.
Related Blogs
- What is the Dark Web | Is Dark Web Illegal? - An Introduction
- What is Tor | How to Use Tor Browser?
- How to Access Dark Web | Use Dark Web Links Safely
- What is Tor? | How Does it Work? | Everything About Tor Network
- How are TOR Onion Hidden Addresses Created | How Does it Work?
- Vulnerabilities in Tor | Is the Tor Browser Safe?
- OWASP ZAP | A Powerful Web Application Security Testing Tool
- What is Wireshark | How to Use Wireshark [Practical Demo]
- How to Install Kali Linux Step By Step Guide
- What is Computer Network | Basics of Networking [With Practical Examples]
- Types of Network Topology with Network Topology Diagram | Techofide
- What is DoS Attack | How to do Denial of Service Attack [Practical Demo]
- Nmap Commands | How to Use Nmap Tool
- Linux Commands | Linux Commands Cheat Sheet
- What is OSINT? | OSINT Framework | Tools for OSINT | Best OSINT Techniques