Hello cyber learners,
I will teach you everything about OSINT and intelligence gathering in this blog series. I will share some practical tools and tips on how a hacker or a government agent performs an OSINT investigation. also, we will discuss the OSINT Framework, some real-life OSINT investigations, and how you can protect your identity from these open source intelligence gathering tools and remain anonymous from the government.
If you want to know how to start your career in ethical hacking then you can check my blog on How to Become an Ethical Hacker | Techofide where our IT professional thoughts and experiences are shared.
In this blog, I will provide a brief overview of what is OSINT?, and which industries are using OSINT. and how OSINT is used by hackers. Additionally, we'll talk about several effective OSINT techniques and tools.
- What is OSINT?
- How OSINT is Important in Real Life
- What is the OSINT Framework?
- Which Fields are using OSINT?
- Open Source Intelligence in Cybersecurity
- Which are the Best Tools for OSINT?
- Do Hackers use OSINT?
- What are OSINT Best Practices?
- Conclusion
- Commonly Asked Questions
What is OSINT?
It stands for Open-Source Intelligence (OSINT) which refers to the process of gathering information from publicly available sources to support decision-making and information security operations. In today’s world, the amount of information available online is growing rapidly and OSINT has become an essential tool for organizations and individuals to stay informed and make informed decisions.

OSINT covers various information sources, including news articles, social media posts, government reports, and other publicly accessible data. This information is collected and analyzed to gain insights into potential threats, market trends, and competitors, without having to go through traditional intelligence-gathering channels. This makes OSINT a cost-effective and efficient means of obtaining valuable information.
How OSINT is Important in Real Life
OSINT has become increasingly important in the intelligence community, with intelligence agencies, law enforcement, and businesses using it to gather information and make informed decisions. With the growing threat of cybercrime and other online threats, OSINT has become an essential tool for organizations to protect themselves and their assets.

One of the advantages of OSINT is that it provides access to a vast amount of information that is otherwise not easily accessible. This information can be used to support decision-making, provide early warning of potential threats, and assist in investigations.
OSINT also enables organizations and individuals to gather information in real-time, making it a valuable tool for staying up-to-date with current events and trends.
Risks and Challenges with OSINT?
Despite its many benefits, OSINT also comes with certain risks and challenges. With so much information available online, it can be difficult to determine the accuracy and reliability of the information. Additionally, the use of OSINT can raise privacy and security concerns, with organizations and individuals having to be careful about what information they access and how they use it.
What is the OSINT Framework?
OSINT Framework refers to a collection of tools and techniques used for gathering and analyzing information from publicly available sources. The goal of an OSINT Methodology is to provide a systematic and structured approach to gathering and analyzing information from various sources, including the internet, social media, government databases, and more.
It is designed to help individuals and organizations gather information from publicly available sources in an organized and systematic manner. The framework categorizes online resources into several categories, such as people search, network analysis, vulnerability search, and more.
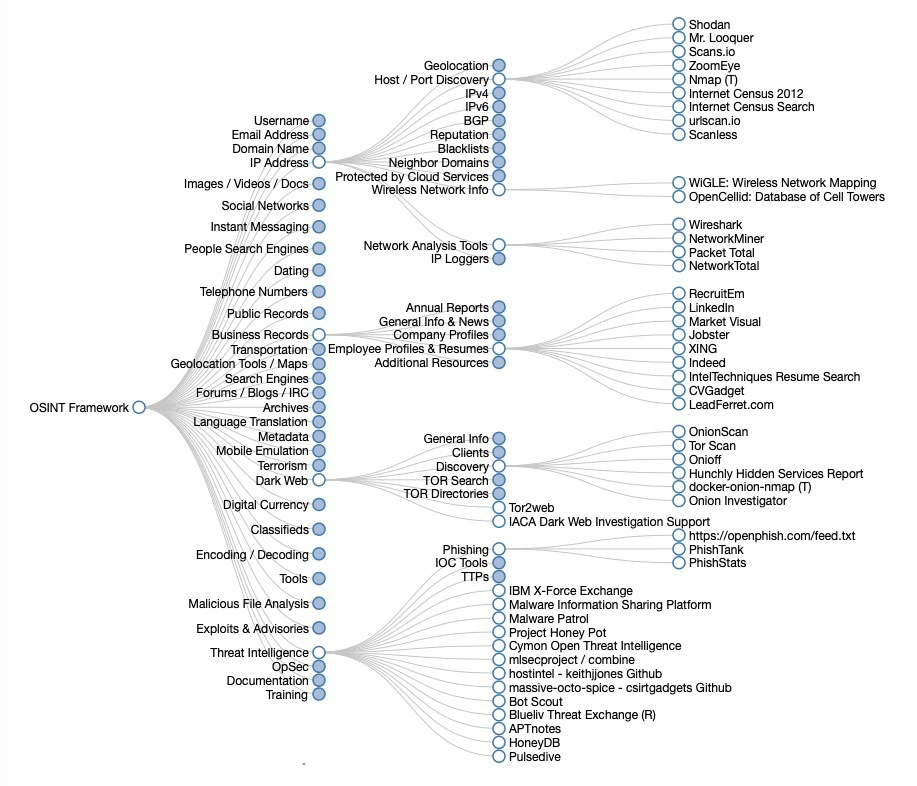
You can also visit the official website of OSINT to access the OSINT Framework
Each category contains a list of online resources that can be used for OSINT gathering. For example, the people search category contains online resources for gathering information about individuals, such as social media profiles, online directories, and more.
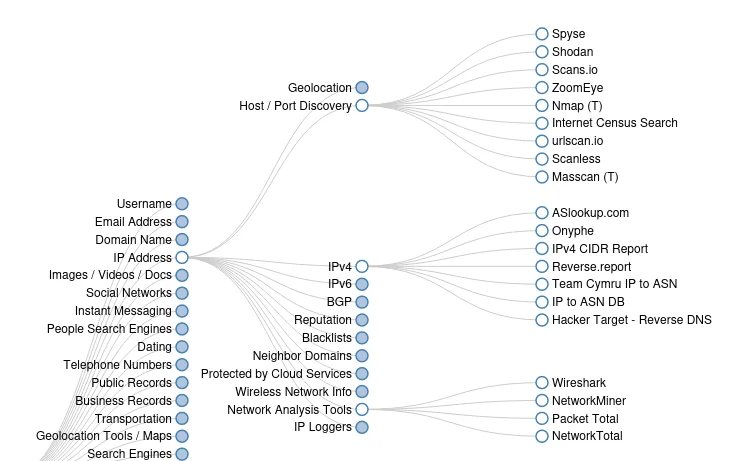
The network analysis category contains online resources for gathering information about infrastructure, such as IP addresses, subdomains, and more.
This website provides a starting point for individuals and organizations who want to gather information from publicly available sources. It is not a comprehensive list of all online resources for OSINT, but it provides a good starting point for those who are new to OSINT. By using the OSINT Methodology, you can maximize the benefits of OSINT and stay ahead of potential security risks.
Which Fields are using OSINT?
Nowadays, almost every domain is adopting OSINT (Open-Source Intelligence). Let's discuss some basic fields that are frequently using OSINT.
- Threat Intelligence: Cybersecurity professionals use OSINT in threat intelligence for Gathering information about potential threats to an organization or individual, such as cyber threats, terrorism, and criminal activities.
- Market Intelligence: Marketing professionals use OSINT for Gathering information about market trends, competition, and consumer behavior.
- Investigative Journalism: journalists and news reporters use OSINT for Investigating and reporting on social, political, and economic issues.
- Business Intelligence: Startups and Business managers use OSINT to Gather information about competitors, customers, and market trends to support business decisions.
- Law Enforcement: Government use OSINT techniques to support criminal investigations and intelligence gathering.
- Political Analysis: OSINT is also useful in Analyzing political developments and events to support decision-making.
- Recruitment: Companies use OSINT for Screening job candidates and gathering information about their backgrounds and qualifications.
- Social Media Monitoring: OSINT is useful in Monitoring social media platforms for mentions of a brand or individual, and gathering insights into public opinion.
- Cybersecurity: Cybersecurity professionals use OSINT for Gathering information about cyber threats and vulnerabilities to support incident response and threat mitigation efforts.
- Intelligence Analysis: OSINT is one of the best tools for intelligence agencies. they use it for Gathering information from publicly available sources to support intelligence analysis and decision-making in the military and government sectors.
- Fraud investigation: OSINT can be used to gather information about potential fraud and to support investigations into fraudulent activities.
- Reputation management: OSINT can be used to monitor an organization's or individual's online reputation and to address any negative publicity.
Open Source Intelligence in Cybersecurity
Now we have a basic understanding of OSINT so let's move towards OSINT in real-life cybersecurity.
Open Source Intelligence (OSINT) is a critical tool in the field of cybersecurity. It refers to information that is publicly available and can be collected, analyzed, and used to mitigate security risks and defend against cyber threats. The increasing amount of digital data available online and the growing number of cyber threats have made OSINT a crucial component of modern cybersecurity.

Cybersecurity professionals are using OSINT according to their roles and responsibilities. I have discussed some of the important below.
Threat Intelligence
OSINT is a valuable source of threat intelligence. Cybersecurity professionals use it to monitor and gather information about known and emerging cyber threats, including malware, botnets, phishing attacks, and zero-day exploits.
This information can be used to protect against these threats proactively and to develop strategies for responding to and mitigating the impact of cyber attacks. Some organizations are also using paid threat intelligence tools like Rapid7, SOC Radar, Tenable.io etc.
Vulnerability Assessment
OSINT can be used to identify vulnerabilities in software, systems, and networks. For example, a cybersecurity professional may use OSINT to find publicly available information about vulnerabilities in popular software applications and operating systems.
This information can then be used to prioritize and address these vulnerabilities before malicious actors can exploit them. Some organizations also prefer paid services that trigger alerts for them if any new vulnerabilities or zero-day threat occurs. Tenable.io and Rapid7 insights are popular tools among organizations.
Social Engineering and Phishing Defense
OSINT can be used to detect and prevent social engineering and phishing attacks. Cybersecurity professionals may use OSINT to monitor public sources for information about new phishing scams or social engineering tactics.
This information can then be used to educate employees and other users about these threats and how to avoid falling victim to them. Organisations also deploy paid email security gateways like Proofpoint, Knowbe4's PhishER or Cisco's email box utility to use AI-based solutions.
Network and System Monitoring
OSINT can also be used to monitor network and system activity for signs of cyber threats. For example, a cybersecurity professional may use OSINT to track public sources for information about malware infections, system breaches, and other security incidents.
This information can then be used to identify potential threats and take action to prevent them from causing harm. Some paid tools such as Cisco Umbrella, Microsoft cloud app security, and threat explorer are also adopted by organizations.
Which are the Best Tools for OSINT?
There is no "best tool" at all in OSINT. It's all about your preferences every tool has its own use case. OSINT is used for many different purposes. so the tools we are using are also different in every single case. In my upcoming blogs, I am going to cover all OSINT techniques and tools that I personally use.
I don't want you to wait more so below I share a small list of the free OSINT tools that I am using. for now,
The most common search engine Google is a powerful utility that can help you gather information from a variety of sources. It is one of the most commonly used free OSINT tools, and it is an excellent starting point for any OSINT investigation. Google Dorks are extremely helpful in some social media OSINT cases.

Question: What is Google Dork?
Ans: Google Dorks is a term used to describe advanced Google search queries that can be used to find specific information from the Internet. By using specific keywords and operators, you can gather information about people, organizations, and infrastructure to help identify potential targets for further security research.
Shodan
Shodan is a search engine for internet-connected devices. It allows you to search for devices, such as webcams, servers, and routers, and it provides information about the devices, including IP addresses, locations, and vulnerabilities.

Maltego
Maltego is a data visualization and information-gathering tool that allows you to gather information about entities, such as organizations, individuals, and IP addresses. It provides a visual representation of the information and allows you to see connections between entities.

Whois Lookup
Whois Lookup is a tool that allows you to gather information about domain names, including information about the domain owner, registrar, and contact information. This tool is useful for gathering information about websites and web services.

Recon-ng
recon-ng is a web reconnaissance framework that allows you to gather information about websites and web services. It provides a variety of modules that can be used to gather information, including information about domains, IP addresses, and subdomains.
Archive.org
Archive.org is a digital archive that provides access to billions of websites, images, and videos. It allows you to view older versions of websites and to see how websites have changed over time.

The Harvester
The Harvester is a tool that allows you to gather information about email addresses, subdomains, and hosts associated with a specific domain. This information can be used to identify potential targets for further security research.

WhoisXML API
WhoisXML API is an API that allows you to gather information about domain registrations, IP addresses, and other network-related information. This information can be used to identify potential targets for further security research.

Netcraft
Netcraft is a security research organization that provides a range of tools and services to help identify potential security risks. Their website provides a wealth of information about the Internet and its infrastructure, including information about web technologies, SSL certificates, and more.

Do Hackers use OSINT?
Yes, hackers use OSINT as part of their reconnaissance phase to gather information about potential targets and to identify vulnerabilities. OSINT can be used to gather information about people, organizations, and infrastructure, such as email addresses, subdomains, and IP addresses. This information can be used to craft targeted attacks and to identify potential targets for further exploitation.
Question: what is reconnaissance?Ans: Reconnaissance is the preliminary stage of information gathering in the field of cybersecurity. It involves actively seeking and gathering information about a target system, network, or organization with the goal of identifying vulnerabilities and potential attack points.

Hackers also use OSINT for social engineering attacks, which are often used to steal sensitive information such as passwords, credit card numbers, and personal information.
They gather information about potential targets from public sources, such as social media profiles, to develop a profile of their behavior and habits. This information is then used to create convincing phishing emails or phone calls to trick the target into providing sensitive information.
we will learn about those tools and techniques one by one in our upcoming blogs
When it comes to black hat hacking, normal people think that some guy in a black hoodie with high-tech payloads and zero days is attacking million-dollar organizations and the government. but this is totally wrong in the case of real-world hacking.
If you visit the list of the past 10 year's biggest hacking attacks, 95% of them are done by social engineering an employee and getting admin access to the target system. OSINT is the best tool for black hat hackers because social engineering totally depends on the information of your target person.
"If you know the enemy and know yourself, you need not fear the result of a hundred battles."
-Sun Tzu(Art of War)
However, it is important to note that the use of OSINT for malicious purposes is illegal and can result in serious consequences. It is always recommended to use OSINT for legitimate purposes and to respect privacy and security. Techofide will not be responsible for any illegal activities.
What are OSINT Best Practices?
Now let's move towards OSINT best practices.
- Determine the purpose of your OSINT investigation: Before you start your OSINT investigation, it is important to determine the purpose of your investigation and the information you are looking to gather. This will help you to focus on your search and ensure that you are using OSINT effectively.
- Use multiple sources: When using OSINT, it is important to use multiple sources to gather information. This helps to ensure that the information you gather is accurate and reliable.
- Respect privacy: When using OSINT, it is important to respect privacy and to only access information that is publicly available. This will help to avoid any privacy and security issues.
- Stay up-to-date: The information available online is constantly changing, so it is important to stay up-to-date with the latest developments and to regularly update your information.
- Use tools and techniques: There are various tools and techniques available to help you with your OSINT investigation. It is important to use these tools and techniques effectively to maximize the information you gather.
- Keep records: When using OSINT, it is important to keep records of the information you gather. This will help you to track the information and ensure that you are using it.
Conclusion
In conclusion, OSINT is a valuable tool for organizations and individuals looking to gather information from publicly available sources. It provides access to a vast amount of information, enables real-time updates, and supports decision-making. However, it is important to be aware of the risks and challenges associated with the use of OSINT and to use it responsibly.
Commonly Asked Questions
Q1. What is open source threat intelligence?
Ans. Open source threat intelligence refers to the collection and analysis of threat-related information that is freely available from publicly accessible sources.
Q2. What is OSINT and is it possible to get a job as an OSINT analyst?
Ans.Yes, it is possible to get a job as an OSINT analyst. OSINT (Open Source Intelligence) analysts are in high demand, as the need for effective cyber security measures continues to grow. OSINT analysts are responsible for collecting, analyzing and interpreting information from publicly available sources to support organizations in protecting against potential threats.
Q3. What qulifications are required to get job as OSINT analyst?
Ans. To get a job as an OSINT analyst, you may need to have a relevant degree or certifications in information security, digital forensics, or a related field. It is also helpful to have experience with a variety of OSINT tools and techniques, as well as strong research and analytical skills. Networking, building a strong online presence and staying up-to-date with the latest trends and developments in the field can also increase your chances of getting hired as an OSINT analyst.
Q4. Is OSINT legal?
Ans. Yes, OSINT (Open Source Intelligence) is generally considered legal. OSINT involves collecting information from publicly available sources, such as news articles, government reports, social media posts, and other sources that are accessible to the general public. As long as the information being collected is publicly available, it is generally considered legal to use for OSINT purposes.
Related Blogs
- What is Smurf Attack? | What is the Denial of Service Attack? | Practical DDoS Attack Step By Step Guide
- What is DoS Attack | How to do Denial of Service Attack [Practical Demo]
- How to Install Kali Linux Step-By-Step Guide
- How to Become an Ethical Hacker | Techofide
- What is Computer Network | Basics of Networking [With Practical Examples]
- What is Metasploit Framework | What is Penetration Testing | How to use Metasploit
- How to Install Metasploit on Windows and Linux | [Step by Step Guide]
- How to Use Metasploit | Metasploit Commands | Metasploit Tutorial